Ce site utilise des cookies. En continuant à naviguer sur le site, vous acceptez notre utilisation des cookies.
Tous
techno-science.net
presse-citron.net
lesnumeriques.com
siecledigital.fr
begeek.fr
itespresso.fr
macgeneration.com
alsacreations.com
frandroid
captainjob
blogduwebdesign-articles
zataznews
phonandroid
fredzone
fredcavazza.net
iphon.fr
smartphonefrance.info
androidpit.fr
lesmobiles.com
spfandroid
macbidouille.com
igen.fr
iphoneaddictfr
megaflux.macg.co
lknfr
Tous
journaldunet.com
lemondeinformatique.fr
developpez.com
linuxfr.org
typepad-agxj
journalducm.com
iadn.eu
leptidigital.fr
news.humancoders.com
oezratty.net
leblogducommunicant2-0.com
journaldunet.com
web.developpez.com
usbeketrica.com
jslive.fr
agorapulse.com
1min30
Optimisez votre site en nettoyant les balises...
Avr 28, 2025 0
Emmaüs & Fondation Abbé Pierre : le changemen...
Avr 26, 2025 0
Réputation & RSE : Attention, péril antiwokis...
Avr 26, 2025 0
Communication & Relations Presse : Faut-il bl...
Avr 26, 2025 0
[video] useActionState : Le nouveau hook de R...
Avr 26, 2025 0
Tous
datasecuritybreach.fr
undernews-ocma
lemagit.fr
lemondeinformatique.fr
lemonde.fr
globalsecuritymag.fr
cyberguerre.numerama.com
blog.kaspersky.fr
usine-digitale.fr
b3b-blog
Les cybercriminels ont volé 16,6 milliards de...
Avr 25, 2025 0
Le réseau d'achat-revente Easy Cash prévient ...
Avr 25, 2025 0
Cybersécurité : Vers une montée en compétence...
Avr 25, 2025 0
Bleu franchit le J0, Meta AI utilise les donn...
Avr 24, 2025 0
- Accueil
- LIVE TV
-
Technologie
- Tous
- techno-science.net
- presse-citron.net
- lesnumeriques.com
- siecledigital.fr
- begeek.fr
- itespresso.fr
- macgeneration.com
- alsacreations.com
- frandroid
- captainjob
- blogduwebdesign-articles
- zataznews
- phonandroid
- fredzone
- fredcavazza.net
- iphon.fr
- smartphonefrance.info
- androidpit.fr
- lesmobiles.com
- spfandroid
- macbidouille.com
- igen.fr
- iphoneaddictfr
- megaflux.macg.co
- lknfr
- Web
- Dev
- Security
- Source d'actu
- Ajoutez votre flux




































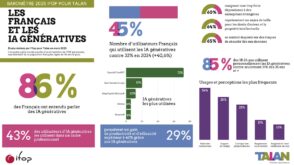



























.webp)












































































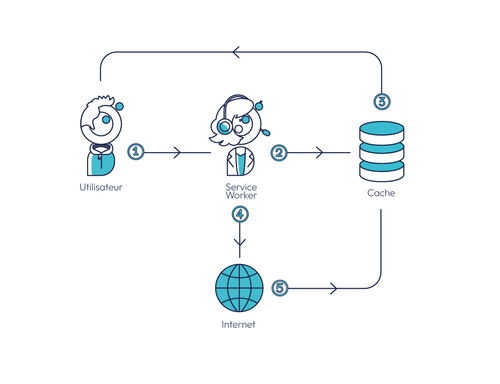
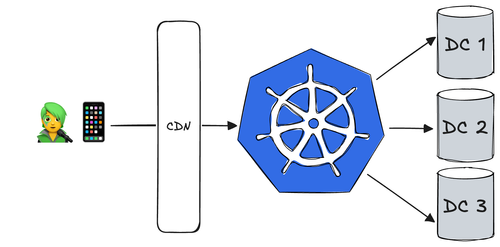










































![Comment Synology combine solutions matérielles et logicielles pour assurer la protection de vos données [Sponso]](https://c0.lestechnophiles.com/www.numerama.com/wp-content/uploads/2025/04/img-dsm-feature-hyper-backup.jpg?resize=1600,900&key=4d057135&watermark)













