Top 10 Best Cyber Attack Simulation Tools – 2025
Cyber attack simulation tools help organizations identify vulnerabilities, test security defenses, and improve their cybersecurity posture by simulating real-world attacks. These tools range from breach and attack simulation (BAS) platforms to adversary emulation frameworks. Here are some of the top cyber attack simulation tools: Cyberattack is not at all a distant threat. Any organization can […] The post Top 10 Best Cyber Attack Simulation Tools – 2025 appeared first on Cyber Security News.

Cyber attack simulation tools help organizations identify vulnerabilities, test security defenses, and improve their cybersecurity posture by simulating real-world attacks.
These tools range from breach and attack simulation (BAS) platforms to adversary emulation frameworks. Here are some of the top cyber attack simulation tools:
Cyberattack is not at all a distant threat. Any organization can be its target. This type of cyber attack simulation is a method of computer security testing.
These identify the vulnerabilities and attack the technique that the malicious actors use.
The Cyber Attack Simulation tools act like a continuous and automated process where it gets to improve by the inherent limitation of red and blue team testing.
- Red team plays the malicious attackers‘ role, and the Blue team helps to deter the attacks.
- Breach and Cyber attack simulation play a critical role in protecting organizational assets by stimulating the attack technique.
- This whole situation has to lead by the security professional, and it stages under a controlled environment.
- Both sides will work together to get a clear picture of the organization’s security.
Basically, it acts as a new type of tool that has come to rescue your organization.
Top 10 Cyber Attack Simulation Tools 2025
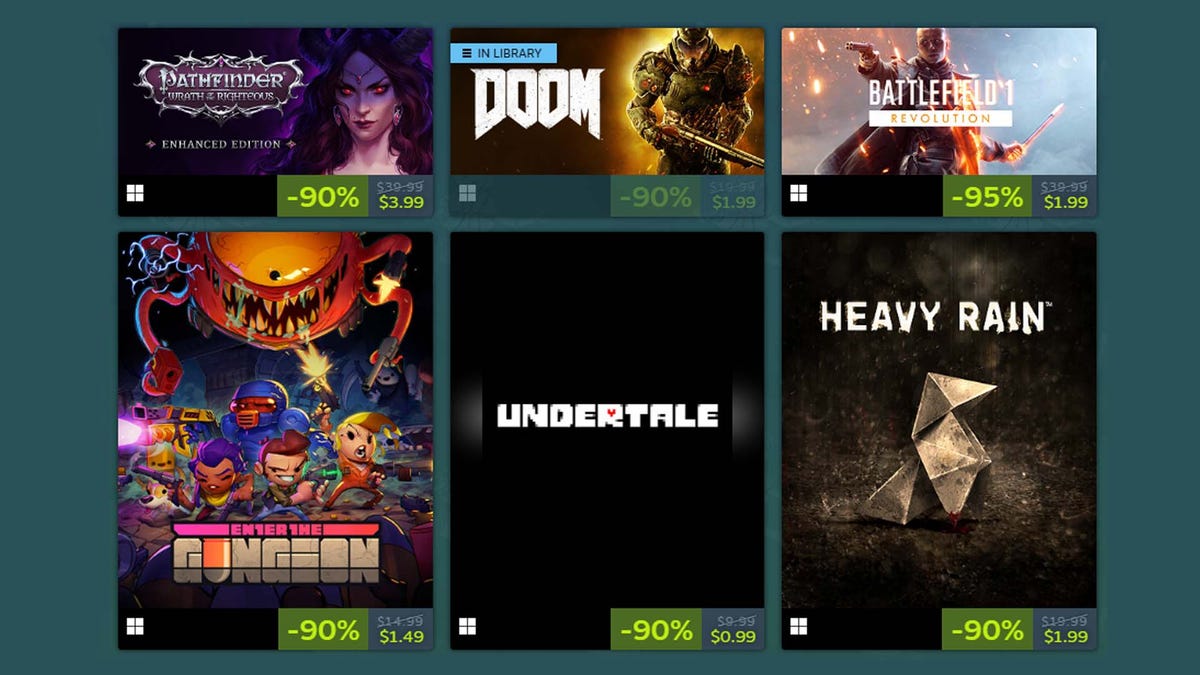
- BreachLock – A cloud-based penetration testing platform that offers automated and manual security testing for web applications, networks, and APIs.
- Foreseeti – A threat modeling and attack simulation tool that helps organizations assess risk and improve security strategies using attack graphs.
- Infection Monkey – An open-source breach and attack simulation (BAS) tool that tests network resilience by simulating lateral movement and post-exploitation techniques.
- AttackIQ – A leading BAS platform that continuously validates security controls by simulating real-world cyber threats.
- Picus – A BAS solution that enables security teams to assess and enhance their defenses by running attack simulations and providing mitigation insights.
- Cymulate – A BAS platform offering automated attack simulations across email, endpoint, web gateway, and cloud environments to evaluate security effectiveness.
- Randori – An automated red teaming and attack surface management tool that simulates sophisticated attacks to uncover weaknesses.
- CALDERA – An open-source adversary emulation platform developed by MITRE, using AI-powered automation to test defensive capabilities.
- NeSSi2 – A network security simulation tool designed for research and testing, focusing on network intrusion detection and response evaluation.
- XM Cyber – A hybrid BAS and attack path management platform that continuously simulates attack paths to uncover security gaps.
10 Best Cyber Attack Simulation Tools 2025 Features
| Best Cyber Attack Simulation Tools | Features |
|---|---|
| 1. BreachLock | 1. Vulnerability Scanning 2. Penetration Testing 3. Web Application Testing 4. Mobile Application Testing 5. Network Infrastructure Testing |
| 2. Foreseeti | 1. Threat modeling 2. Attack path analysis 3. Risk assessment 4. Vulnerability management 5. Security control validation |
| 3. Infection Monkey | 1. Automated attack simulations 2. Continuous security testing 3. Virtual exploitation of vulnerabilities 4. Risk-based prioritization 5. Real-time monitoring and reporting |
| 4. AttackIQ | 1. Automated security control validation 2. Continuous security testing 3. Simulated threat scenarios 4. Attack emulation |
| 5. Picus | 1. Picus is a cybersecurity platform. 2. It offers continuous security validation and testing. 3. It provides real-time visibility into security vulnerabilities. 4. It enables proactive threat hunting and detection. |
| 6. Cymulate | 1 Security posture assessment 2. Continuous security testing 3. Attack simulations 4. Real-time monitoring and reporting |
| 7. Randori | 1. Attack surface discovery 2. Continuous reconnaissance 3. Vulnerability identification 4. Threat intelligence integration |
| 8. CALDERA | 1. Automated adversary simulations 2. Attack scenario creation 3. Red teaming capabilities 4. Threat intelligence integration |
| 9. NeSSi2 | 1. NeSSi2 is a network security simulator. 2. It supports modeling and simulating complex network scenarios. 3. It allows for the evaluation of network security measures and protocols. 4. It provides a graphical user interface for easy configuration and visualization. |
| 1. Automated attack stimulations 2. Continuous security testing 3. Virtual exploitation of vulnerabilities 4. Risk-based prioritization |
1. BreachLock

One technology that offers penetration testing as a service (PaaS) is BreachLock, which is used for cyber assault simulation.
A couple of clicks are all it takes to set up the vulnerability to run automatically at predetermined periods.
Based on the findings, the BreachLock team may track white-hat ethical hackers as they conduct manual pen tests.
Features
- This is a platform for protection called BreachLock.
- It provides full vulnerability scanning and review.
- It offers services like vulnerability testing and ethical hacking.
- It works with both human and automated testing methods.
| What is Good ? | What Could Be Better ? |
|---|---|
| Comprehensive Testing | Reliance on External Service |
| Customizable Approach | Time and Resource Constraints |
| Actionable Recommendations | Limited Control |
| Continuous Monitoring | Cost Considerations |
Price
you can get a free trial and personalized demo from here.
BreachLock – Trial / Demo
2. Foreseeti

In order to evaluate and control the risk, this program lets you virtually assault your infrastructure.
In addition to providing direct experience, it explains three basic concepts:
A firewall, server, service, router, and server can all be added using this method.
Whether or not you wish to take the test is the only option you have.
Discovering when your system will fail is why this procedure is so important.
The technique relies solely on simulation data to provide reports that can be put into action.
You, the user, can also put things into action to reduce risk generally.
You will learn how it works and get a feel for it if you give the community edition a go; it’s enterprise-ready but has restricted functionality.
Features
- Foresee, which used to be called security, is a tool for security.
- It lets you model threats and evaluate risks before they happen.
- It makes attack routes visible and lets you analyze them.
- It lets you create very complicated IT networks and infrastructures.
| What is Good ? | What Could Be Better ? |
|---|---|
| Proactive Threat Modeling | Learning Curve |
| Attack Path Visualization | Complexity for Small Organizations |
| Quantitative Risk Analysis | Dependency on Accurate Inputs |
| Customization and Flexibility | Limited Real-Time Monitoring |
Price
you can get a free trial and personalized demo from here.
Foreseeti – Trial / Demo
3. Infection Monkey

Infection Monkey is a great tool for testing infrastructure running on Azure, Google Cloud, AWS, or your own premises if you’re considering deploying your service to the cloud.
Installable on Windows, Debian, and Docker, this is a top-notch open-source utility. Automated cyber-attack simulations can help you prevent credential theft and misconfiguration.
When you run Infection Monkey’s attack simulation, it won’t interfere with your network in any way.
Memory and CPU usage are kept to a minimum. It was able to depict the network and trace the attacker’s pattern of attack with ease.
Feel free to try out the demo version before committing to the full version.
Features
- Infection Monkey is an open-source security tool.
- It simulates real-world cyber attacks to test network resilience.
- It helps identify vulnerabilities and weaknesses in the network.
- Finds holes in the security measures.
- Works with a number of operating platforms.
| What is Good ? | What Could Be Better ? |
|---|---|
| Security Assessment | Limited Scope |
| Vulnerability Identification | False Positives and Negatives |
| Lateral Movement Simulation | Potential Disruption |
| Continuous Testing | Technical Expertise |
Price
you can get a free trial and personalized demo from here..
Infection Monkey – Trial / Demo
4. AttackIQ

When it comes to validating security, this is among the most used cyber-attack simulation programs.
The platform becomes more scalable, which enhances the data center’s security.
This solution is designed to assist security operation engineers in developing offensive and defensive strategies in collaboration with the red team.
This tool is fully compatible with MITRE ATT&CK and other critical frameworks.
The AttackIQ research team powers it, which operates as a market leader in the security industry.
Making sure everything is secure allows you to tailor the attack scenario to make it seem completely different from the actual danger.
It guarantees that the user will receive a security status report and that the assault will become automated.
It is compatible with the main OS and works in tandem with the current setup.
Use the FREE trial option to take your time making a decision so you can have a better understanding of this technology.
Features
- AttackIQ is a platform for defense.
- It lets protection be checked and confirmed all the time.
- It takes care of security controls and reviews automatically.
- It mimics threats that happen in the real world to test how well security works.
| What is Good ? | What Could Be Better ? |
|---|---|
| Continuous Security Validation | Complexity |
| Automated Testing | Dependency on External Service |
| Realistic Adversary Simulations | Cost |
| Risk Prioritization |
Price
you can get a free trial and personalized demo from here.
AttackIQ – Trial / Demo
5. Picus

One of the top risk and security management solutions, it keeps you ahead of cybercriminals with continual assessments, measures, and vulnerabilities.
The platform is designed to make it easy for customers to test their defenses and identify real attackers, and configuring and utilizing the dashboard is also quite easy.
It provides sufficient security as well.
There are a few benefits Below
- It has an extensive threat database with protection.
- It provides real-time identification that gives a strong security layer and it allows the team to get a quick identity.
- It also maximizes security so that technology does not become change.
- It makes quick identification of vulnerabilities and suggests you the optimum mitigation to reduce the risk.
Features
- Picus simulates real-world assaults and threats to test system security.
- It delivers firms real-time technological security data, revealing vulnerabilities and threats.
- Picus automatically examines systems, apps, and networks for security flaws.
- It lets firms rank security issues by severity to save resources and reduce hazards.
| What is Good ? | What Could Be Better ? |
|---|---|
| Real-Time Threat Detection | Help for Customers |
| Continuous Security Validation | Maintaining and making changes |
| Attack Simulation | |
| Actionable Insights |
Price
you can get a free trial and personalized demo from here..
Picus – Trial / Demo
6. Cymulate
.webp)
This program uses the MITRE ATT&CK database and other industry standards as its foundation.
It is an optimization platform that runs in the background, automatically uploads books to the network, and then gives a detailed report with information like scores, vulnerabilities, and more.
Features
- Cymulate is a tool for security.
- It gives ongoing testing and validation of security.
- It lets you test how well security works by simulating attacks.
- It works with many types of attack, such as email, web, and network.
| What is Good ? | What Could Be Better ? |
|---|---|
| Comprehensive Security Testing | Accuracy of Simulation |
| Continuous Security Validation | |
| Customizable Assessments | |
| Actionable Insights |
Price
you can get a free trial and personalized demo from here.
Cymulate – Trial / Demo
7. Randori

As part of the cyber assault simulation platform’s automated red team, this tool is incredibly dependable.
By warding off assaults, it’s great for the security system.
An attacker also has to attack in the same manner that this tool searches for the safest route, because it can launch real attacks.
The following are some of the many advantages of this tool:
We can evaluate the security solution and find the weak spot on this platform.
gives a glimpse of how an attacker may perceive the assets of the company.
Helps the group entice the actual intruders and pave a secure path to the company’s IT infrastructure.
You can’t relax and think you’re safe since it offers real-time attack target analysis, allowing you to pinpoint vulnerabilities and test defenses.
Features
- Randori is a tool for security.
- It gives security testing and monitoring all the time.
- As well as proactive attack training, it offers red teaming services.
- It helps the group figure out where its defenses are weak or open to attack.
| What is Good ? | What Could Be Better ? |
|---|---|
| Realistic Attack Simulations | Lack of Attention to Technique |
| Continuous Testing | It’s too much for beginners |
| Actionable Recommendations | |
| Comprehensive Coverage |
Price
you can get a free trial and personalized demo from here..
Randori – Trial / Demo
8. CALDERA

You can tell it’s an adversary emulation program that works with Windows Domain networks just by looking at the name.
This program is able to evaluate and reproduce the system’s behavior since it uses the ATT&CK model.
The Metta by Uber is another option to consider.
Features
- Complex adversary missions in CALDERA can simulate real-life attacks.
- Defining your enemies’ TTPs helps you create new assault scenarios.
- CALDERA and MITRE ATT&CK allow users plan and track opponent techniques.
- It automates actions so planned enemy exercises can be executed.
| What is Good ? | What Could Be Better ?What Could Be Better ? |
|---|---|
| Automated Adversary Emulation | Technical Expertise Required |
| Customizable Scenarios | Learning Curve |
| Threat Intelligence Integration | |
| Metrics and Reporting |
Price
you can get a free trial and personalized demo from here.
CALDERA – Trial / Demo
9. NeSSi2

Similar to other open-source tools, this one is built on the JIAC architecture.
Network Security Simulator is its primary function.
It mostly tests algorithms, profile-based automated attacks, network analysis, and other types of intrusion detection.
You must have MySQL and Java SE7 installed in order to use this program.
Features
- NeSSi2 can design sophisticated network scenarios including nodes, connections, and protocols.
- It enables you simulate network security protocols and their behavior.
- NeSSi2’s GUI simplifies virtual network setup, viewing, and monitoring.
- It includes many pre-set attack and defense strategies for network security simulations.
| What is Good ? | What Could Be Better ? |
|---|---|
| Flexibility | Limited Scope |
| Realistic Simulations | Realistic Simulations |
| Comprehensive Analysis | |
| Collaboration and Research |
Price
you can get a free trial and personalized demo from here.
NeSSi2 – Trial / Demo
10. XM Cyber

This Cyber Attack Simulation provides automated APT (advanced persistent threat) protection.
To ensure that the perpetrators get the report’s prioritized remediation, all you have to do is choose the target and perform the setup.
Some important things concerning this tool can be written down:
Adapting the attack scenario to specific requirements is within its capabilities.
The attack path can also be visualized.
To ensure it is always current, XM Cyber constantly follows the attack approach.
In addition, it follows the best practices and does the best activities as instructed.
Features
- This is XM Cyber, a tool for cybersecurity.
- It gives ongoing testing and validation of security.
- It lets you simulate complex attacks and do automatic red teaming.
- It checks the safety of networks and things that are very important.
- It finds weak spots, vulnerabilities, and wrong settings.
| What is Good ? | What could Be Better ? |
|---|---|
| Continuous Security Testing | Integration Challenges |
| Realistic Attack Simulations | Dependence on Correct Simulation |
| Risk Prioritization | |
| Actionable Recommendations |
Price
you can get a free trial and personalized demo from here..
XM Cyber – Trial / Demo
Final Thoughts – Cyber Attack Simulation Tools
As a business owner, managing an organization’s IT, security risk is always challenging.
We hope that all the above cyber attack simulation tools can help you to implement world-class control at lower risk.
Here all mentioned tools offer a free trial so you can try those first and decide to go for a purchase
The post Top 10 Best Cyber Attack Simulation Tools – 2025 appeared first on Cyber Security News.




































































![Sonos Abandons Streaming Device That Aimed to Rival Apple TV [Report]](https://www.iclarified.com/images/news/96703/96703/96703-640.jpg)
![HomePod With Display Delayed to Sync With iOS 19 Redesign [Kuo]](https://www.iclarified.com/images/news/96702/96702/96702-640.jpg)
![iPhone 17 Air to Measure 9.5mm Thick Including Camera Bar [Rumor]](https://www.iclarified.com/images/news/96699/96699/96699-640.jpg)







































































































_Andrii_Yalanskyi_Alamy.jpg?#)





























































![[The AI Show Episode 139]: The Government Knows AGI Is Coming, Superintelligence Strategy, OpenAI’s $20,000 Per Month Agents & Top 100 Gen AI Apps](https://www.marketingaiinstitute.com/hubfs/ep%20139%20cover-2.png)


![[The AI Show Episode 138]: Introducing GPT-4.5, Claude 3.7 Sonnet, Alexa+, Deep Research Now in ChatGPT Plus & How AI Is Disrupting Writing](https://www.marketingaiinstitute.com/hubfs/ep%20138%20cover.png)






































































































































.png?width=1920&height=1920&fit=bounds&quality=80&format=jpg&auto=webp#)
-Rainbow-Six-Siege-X---Official-Gameplay-Trailer-00-01-00.png?width=1920&height=1920&fit=bounds&quality=80&format=jpg&auto=webp#)