Criminals are targeting Bitcoin owners on Facebook with a multi-stage malware campaign - follow these steps to stay safe
Fake crypto ads on Facebook now deliver malware that quietly spins up a local server on your machine.

- Experts warn Facebook crypto ads now deliver malware through trusted brand impersonation
- Malware deploys only when victims meet specific browser or profile criteria
- Local server and PowerShell commands allow stealthy data exfiltration and control
A new wave of malware attacks is targeting Bitcoin and crypto owners through Facebook ads that mimic trusted names in the industry.
Bitdefender says it has uncovered a multi-stage malvertising campaign that exploits the reputations of well-known platforms like Binance, TradingView, ByBit, and others.
These malicious ads don’t just trick users, they also adapt in real time to avoid detection and deliver malware only when conditions are ideal for the attackers.
Highly evasive delivery system
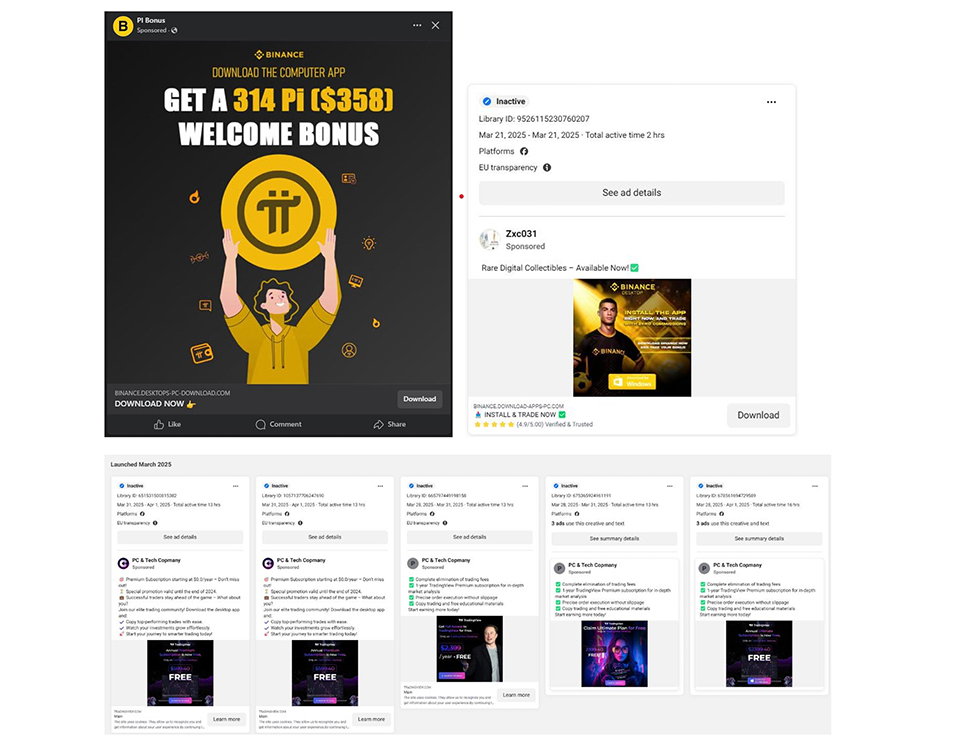
The scheme begins when cybercriminals hijack or create Facebook accounts and use Meta’s ad network to run fraudulent promotions.
These ads feature fake offers and use photos of celebrities - Zendaya, Elon Musk, and Cristiano Ronaldo are the usual suspects - to appear more convincing.
Once clicked, users are redirected to lookalike websites that impersonate legitimate cryptocurrency services and prompt them to download what appears to be a desktop client.
The malware delivery system is highly evasive. Bitdefender says the front-end of the fake site works with a local server quietly spun up by the initial install, allowing attackers to send payloads directly to the victim's system while dodging most security software.
Delivery only happens if the victim meets specific criteria, such as being logged into Facebook, using a preferred browser like Microsoft Edge, or matching a certain demographic profile.
Some malware samples run lightweight .NET servers locally and communicate with the website using advanced scripts that execute encoded PowerShell commands. These can exfiltrate sensitive data like installed software, system and OS info, and even GPU details.
Depending on the findings, the malware may download further payloads or simply go dormant if it suspects it's being analyzed in a sandbox.
Bitdefender researchers found hundreds of Facebook accounts promoting these campaigns. One ran more than 100 ads in a single day. Many ads target men aged 18 and older, with examples found in Bulgaria and Slovakia.
How to stay safe

Scrutinize ads carefully: Be highly skeptical of ads offering free crypto tools or financial perks. Always verify links before clicking.
Download from official sources only: Visit platforms like Binance or TradingView directly. Never trust redirects from ads.
Use link-checking tools: Tools like Bitdefender Scamio or Link Checker can alert you to dangerous URLs before you engage.
Keep your security software up to date: Use a reputable antivirus that gets regular updates to catch evolving threats.
Watch for suspicious browser behavior: Pages that insist you use Edge or redirect erratically are massive red flags.
Report shady ads: Flag suspicious content on Facebook to help others avoid falling into the same trap.
You might also like
- Stay protected with the best antivirus tools around
- We've also rounded up the best free antivirus solutions
- Hackers steal over $1bn in one of the biggest crypto thefts ever

























































![Apple Shares 'Last Scene' Short Film Shot on iPhone 16 Pro [Video]](https://www.iclarified.com/images/news/97289/97289/97289-640.jpg)
![Apple M4 MacBook Air Hits New All-Time Low of $824 [Deal]](https://www.iclarified.com/images/news/97288/97288/97288-640.jpg)
![An Apple Product Renaissance Is on the Way [Gurman]](https://www.iclarified.com/images/news/97286/97286/97286-640.jpg)
![Apple to Sync Captive Wi-Fi Logins Across iPhone, iPad, and Mac [Report]](https://www.iclarified.com/images/news/97284/97284/97284-640.jpg)
![So your [expletive] test failed. So [obscene participle] what?](https://regmedia.co.uk/2016/08/18/shutterstock_mobile_surprise.jpg)










![[Fixed] Gemini 2.5 Flash missing file upload for free app users](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/03/google-gemini-workspace-1.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)


![As Galaxy Watch prepares a major change, which smartwatch design to you prefer? [Poll]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2024/07/Galaxy-Watch-Ultra-and-Apple-Watch-Ultra-1.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)


































































































































![[The AI Show Episode 146]: Rise of “AI-First” Companies, AI Job Disruption, GPT-4o Update Gets Rolled Back, How Big Consulting Firms Use AI, and Meta AI App](https://www.marketingaiinstitute.com/hubfs/ep%20146%20cover.png)

















































































![Ditching a Microsoft Job to Enter Startup Purgatory with Lonewolf Engineer Sam Crombie [Podcast #171]](https://cdn.hashnode.com/res/hashnode/image/upload/v1746753508177/0cd57f66-fdb0-4972-b285-1443a7db39fc.png?#)


![[DEALS] Internxt Cloud Storage Lifetime Subscription: 10TB Plan (88% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)






































































