Beware! Fake AI Video Generation Platforms Drop Stealer Malware on Your Computers
As artificial intelligence (AI) tools gain mainstream traction for content creation, cybercriminals are capitalizing on the hype with a sophisticated new attack vector, fake AI platforms promising advanced video and image editing capabilities. These fraudulent sites, amplified through viral social media campaigns and Facebook groups with tens of thousands of views, lure users into uploading […] The post Beware! Fake AI Video Generation Platforms Drop Stealer Malware on Your Computers appeared first on Cyber Security News.

As artificial intelligence (AI) tools gain mainstream traction for content creation, cybercriminals are capitalizing on the hype with a sophisticated new attack vector, fake AI platforms promising advanced video and image editing capabilities.
These fraudulent sites, amplified through viral social media campaigns and Facebook groups with tens of thousands of views, lure users into uploading personal media, only to deliver a previously undocumented malware dubbed Noodlophile Stealer.
This malicious payload steals browser credentials, cryptocurrency wallets, and sensitive data, often deploying a remote access trojan (RAT) like XWorm for deeper system control.
The Lure: Fake AI Platforms
According to the Morphisec team report exclusively shared with Cyber Security News, The campaign stands out for its exploitation of public enthusiasm for AI-powered tools, targeting creators and small businesses exploring productivity-enhancing technologies.
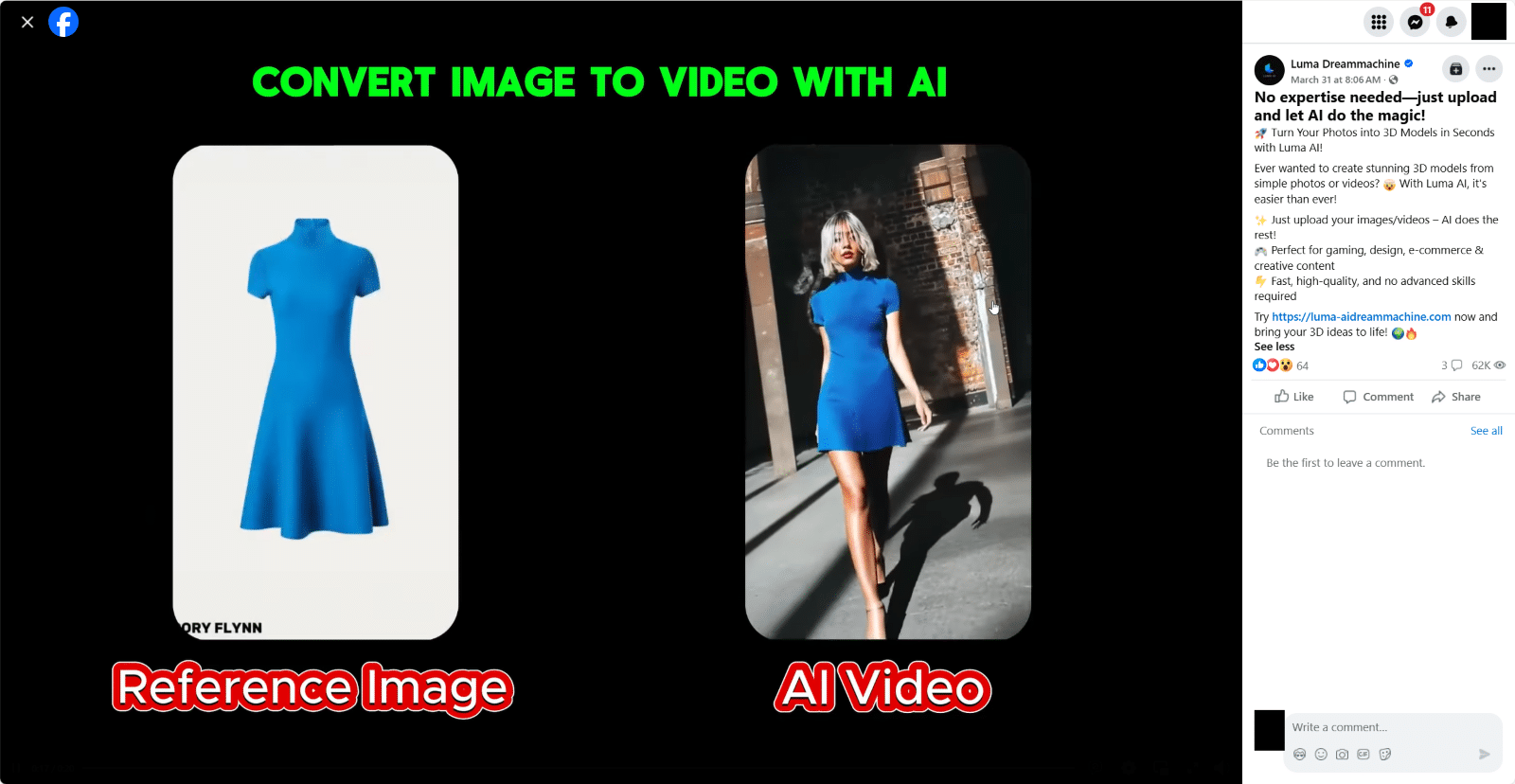
Unlike traditional phishing or pirated software scams, these attackers craft convincing websites mimicking legitimate AI services, such as video generation platforms.
Social media posts, particularly on Facebook, drive traffic to these sites, with one post alone garnering over 62,000 views.
Users are enticed to upload images or videos, expecting AI-generated content in return. Instead, they are prompted to download a malicious file disguised as their “processed” output.
The downloaded file, often a ZIP archive named VideoDreamAI.zip, contains an executable misleadingly titled Video Dream MachineAI.mp4.exe.
This file masquerades as a video but is a 32-bit C++ application, repurposing a legitimate video editing tool (CapCut, version 445.0) and signed with a fraudulent certificate to evade detection. Upon execution, it initiates a multi-stage infection chain, deploying Noodlophile Stealer and, in some cases, XWorm.

Noodlophile Stealer
Noodlophile Stealer is a previously undocumented infostealer, combining browser credential theft, cryptocurrency wallet exfiltration, and optional RAT deployment.
Its modular design and obfuscated delivery make it a formidable addition to the malware ecosystem. The malware communicates stolen data via a Telegram bot, enabling covert exfiltration.
Open-source intelligence (OSINT) investigations revealed Noodlophile being offered in cybercrime marketplaces as part of malware-as-a-service (MaaS) schemes, alongside tools for account takeover and credential theft.
The developer, likely Vietnamese based on language indicators and social media profiles, actively promotes the malware in related Facebook groups.
The Attack Chain
The infection begins when users interact with a fake AI site, upload media, and download the malicious ZIP. Inside, a hidden folder (5.0.0.1886) contains key components:
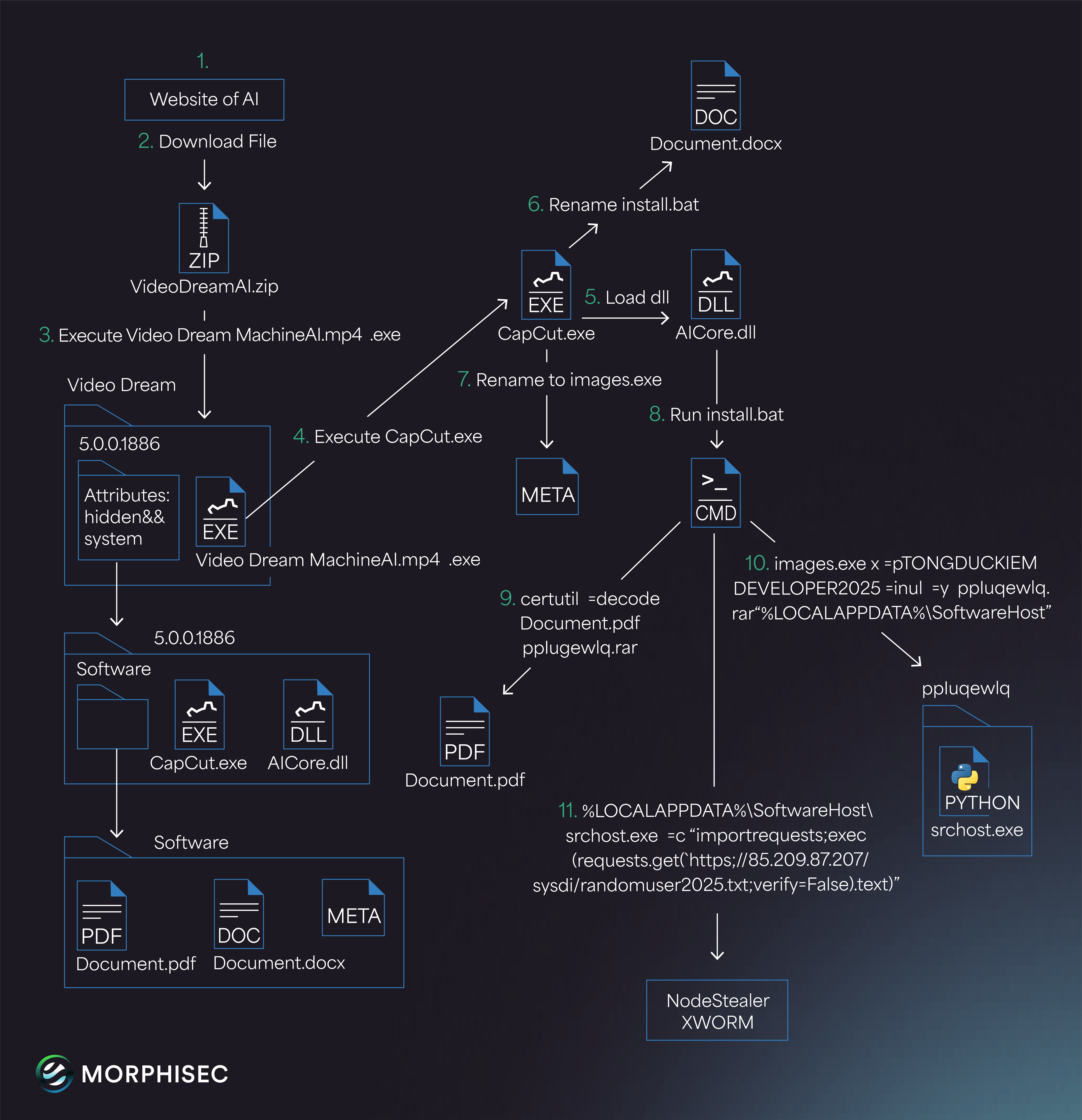
- CapCut.exe: A 140MB C++ binary embedding a .NET runtime wrapper to load malicious .NET code in-memory, evading static scanners. It contains 275 embedded PE files, mostly .NET assemblies, for modular obfuscation.
- AICore.dll: A helper DLL with a single active export (cmdhelper) for executing external commands.
- Document.pdf: A Base64-encoded, password-protected RAR archive disguised as a PDF, containing cPython components.
- Document.docx: A batch file masquerading as a Word document, encoded with FF FE markers to hinder analysis. Renamed to install.bat, it orchestrates the infection.
- meta: A Win-RAR utility, renamed to images.exe, for extracting the RAR archive.
The infection proceeds as follows:
- CapCut.exe launches, using embedded .NET logic to invoke CapCutLoader.
- CapCutLoader verifies connectivity by pinging google.com and renames disguised files (Document.docx to install.bat, meta to images.exe).
- install.bat decodes Document.pdf into a RAR archive using certutil.exe, extracts it with a hardcoded password (TONGDUCKIEMDEVELOPER2025), and registers persistence via the Windows Registry.
- A Python payload (srchost.exe), downloaded from a remote server, deploys Noodlophile Stealer and XWorm.
The final payload includes a Noodlophile variant for credential theft and a Python-based XWorm loader with two propagation methods: in-memory shellcode injection or PE hollowing into RegAsm.exe to evade detection.
The campaign employs advanced obfuscation, including base85 decoding, zlib decompression, and Python’s marshal module to execute payloads in-memory, avoiding disk-based detection.
A Python script (randomuser2025.txt) contains 10,000 redundant operations to break automated analysis tools. The use of legitimate tools like certutil.exe and RegAsm.exe further complicates detection.
This campaign highlights the growing sophistication of cybercriminals in exploiting emerging technologies. By weaponizing trust in AI, attackers target a broader, less skeptical audience.
The introduction of Noodlophile Stealer underscores the evolving malware landscape, with MaaS models enabling rapid proliferation.
Users are urged to verify the legitimacy of AI platforms, avoid downloading files from untrusted sources, and employ robust security solutions to detect multi-stage threats.
Are you from the SOC and DFIR Teams? – Analyse Real time Malware Incidents with ANY.RUN -> Start Now for Free.
The post Beware! Fake AI Video Generation Platforms Drop Stealer Malware on Your Computers appeared first on Cyber Security News.








































































![New iPad 11 (A16) On Sale for Just $277.78! [Lowest Price Ever]](https://www.iclarified.com/images/news/97273/97273/97273-640.jpg)

![Apple Foldable iPhone to Feature New Display Tech, 19% Thinner Panel [Rumor]](https://www.iclarified.com/images/news/97271/97271/97271-640.jpg)

























-xl.jpg)














































































































































































































![[The AI Show Episode 146]: Rise of “AI-First” Companies, AI Job Disruption, GPT-4o Update Gets Rolled Back, How Big Consulting Firms Use AI, and Meta AI App](https://www.marketingaiinstitute.com/hubfs/ep%20146%20cover.png)


















































































































![[FREE EBOOKS] Offensive Security Using Python, Learn Computer Forensics — 2nd edition & Four More Best Selling Titles](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)














































![Ditching a Microsoft Job to Enter Startup Purgatory with Lonewolf Engineer Sam Crombie [Podcast #171]](https://cdn.hashnode.com/res/hashnode/image/upload/v1746753508177/0cd57f66-fdb0-4972-b285-1443a7db39fc.png?#)

































-Nintendo-Switch-2-Hands-On-Preview-Mario-Kart-World-Impressions-&-More!-00-10-30.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)

















































.jpg?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)














