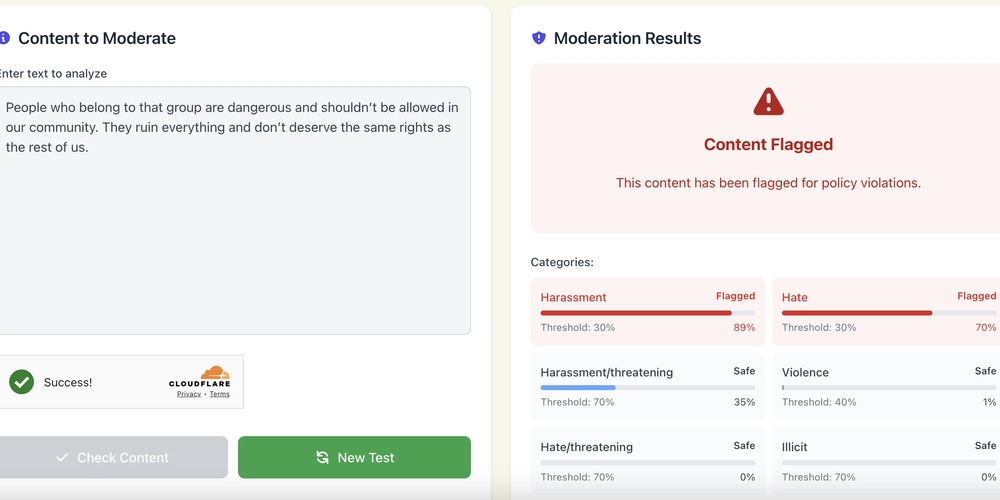
Hackers Weaponize MMC Script to Deploy MysterySnail RAT Malware
A sophisticated cyberespionage campaign leveraging malicious Microsoft Management Console (MMC) scripts to deploy the stealthy MysterySnail remote access trojan (RAT). First identified in 2021 during an investigation into the CVE-2021-40449 zero-day vulnerability, MysterySnail RAT had seemingly disappeared from the cyber threat landscape. Attributed to the Chinese-speaking threat actor known as IronHusky, which has operated since […] The post Hackers Weaponize MMC Script to Deploy MysterySnail RAT Malware appeared first on Cyber Security News.

A sophisticated cyberespionage campaign leveraging malicious Microsoft Management Console (MMC) scripts to deploy the stealthy MysterySnail remote access trojan (RAT).
First identified in 2021 during an investigation into the CVE-2021-40449 zero-day vulnerability, MysterySnail RAT had seemingly disappeared from the cyber threat landscape.
Attributed to the Chinese-speaking threat actor known as IronHusky, which has operated since at least 2017, this malware has apparently remained active but undetected for years.
“It turned out that the implant has been actively used in cyberattacks all these years although not reported,” Kaspersky said.
Sophisticated Infection Chain
The attack begins with a malicious MMC script disguised as a document from Mongolia’s National Land Agency (ALAMGAC). This social engineering tactic increases the likelihood that government targets will open the disguised file.
Once executed, the script initiates a multi-stage infection process. First, it retrieves a ZIP archive containing a second-stage payload and a legitimate DOCX file from file[.]io storage.
The archive is extracted to a specific directory: %AppData%\Cisco\Plugins\X86\bin\etc\Update
A legitimate executable (CiscoCollabHost.exe) is launched, which loads a malicious library (CiscoSparkLauncher.dll) through DLL sideloading.
Further, persistence is established through registry modifications and the lure document opens to avoid raising suspicion.
The researchers identified an innovative intermediary backdoor that communicates with command-and-control (C2) servers by abusing the open-source piping-server project.
In an unusual anti-analysis technique, the backdoor stores Windows API function information in an external file (log\MYFC.log), which is encrypted with single-byte XOR and loaded at runtime.
The backdoor communicates with https://ppng.io to receive commands including:
- RCOMM: Runs command shells.
- FSEND: Downloads files from C2.
- FRECV: Uploads files to C2.
- FEXEC: Creates new processes.
- FDELE: Deletes files.
Evolved MysterySnail RAT
The latest version maintains persistence as a service and uses sophisticated encryption techniques. Its malicious DLL loads a payload encrypted with RC4 and XOR from a file named attach.dat, and employs reflective loading through DLL hollowing using the run_pe library.
Communications have been observed with multiple attacker-controlled domains including watch-smcsvc[.]com and leotolstoys[.]com.
Unlike its 2021 predecessor, which implemented approximately 40 commands in a single component, the new MysterySnail employs a modular architecture with five specialized DLLs downloaded at runtime:
- BasicMod.dll: Handles drive listing, file deletion, and system fingerprinting.
- ExplorerMoudleDll.dll: Manages file reading, service administration, and process creation.
- process.dll: Lists and terminates running processes.
- cmd.dll: Creates processes and command shells.
- tcptran.dll: Manages network connections.
Researchers also discovered a lightweight variant dubbed “MysteryMonoSnail” that communicates via WebSocket protocol instead of HTTP and offers reduced functionality with just 13 basic commands.
This reemergence highlights the importance of maintaining vigilance against dormant threats.
“While conducting threat hunting activities, it’s crucial to consider that old malware families, which have not been reported on for years, may continue their activities under the radar,” warn researchers.
The case of MysterySnail demonstrates how threat actors can maintain operational persistence by making minimal modifications to existing malware, allowing them to remain undetected for extended periods.
Malware Trends Report Based on 15000 SOC Teams Incidents, Q1 2025 out!-> Get Your Free Copy
The post Hackers Weaponize MMC Script to Deploy MysterySnail RAT Malware appeared first on Cyber Security News.


































































![Apple Watch Series 10 Back On Sale for $299! [Lowest Price Ever]](https://www.iclarified.com/images/news/96657/96657/96657-640.jpg)
![Apple Slips to Fifth in China's Smartphone Market with 9% Decline [Report]](https://www.iclarified.com/images/news/97065/97065/97065-640.jpg)
![EU Postpones Apple App Store Fines Amid Tariff Negotiations [Report]](https://www.iclarified.com/images/news/97068/97068/97068-640.jpg)












![What’s new in Android’s April 2025 Google System Updates [U: 4/18]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/01/google-play-services-3.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)





























































































_Andreas_Prott_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)






















































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)