How can Desktop Apps Interact Securely with Web APIs
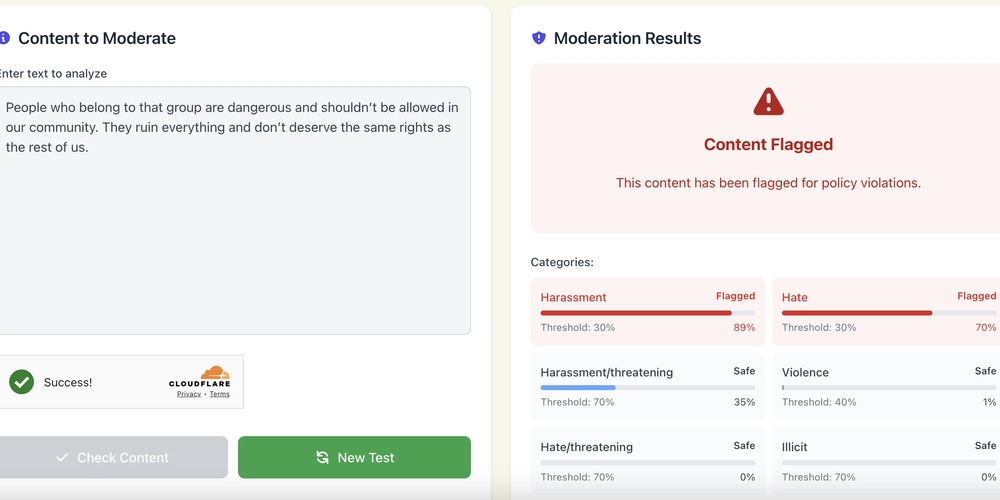
SafeLine WAF is a self-hosted alternative to CloudFlare WAF, protecting all application with HTTP/HTTPS protocol. It's powered by a semantic analysis engine and very easy to deploy & configure. Website: https://ly.safepoint.cloud/ionBhgY When a desktop application talks to a web API, the security concerns are very similar to browser or mobile apps — but there are some extra risks (like local reverse engineering or token stealing). Here’s the typical secure approach: 1️⃣ Use HTTPS (TLS) — always All communication between your desktop app and the API should go over HTTPS to: Encrypt the data Prevent eavesdropping Ensure server authenticity via certificates 2️⃣ Use Proper Authentication Mechanisms Scenario Recommended Method User-specific access OAuth 2.0 Authorization Code Flow Device-specific access OAuth 2.0 Device Code Flow / mTLS Application-level (no user) API Key + Signature / mTLS OAuth 2.0 is the most common and secure way for desktop apps to authenticate the user and obtain access tokens for API calls. 3️⃣ Avoid Embedding Secrets in the App Desktop binaries can be decompiled. Avoid hardcoded secrets. Solutions: Use dynamic secret exchange (OAuth flow). Offload sensitive logic to the server. Use certificate pinning to prevent TLS interception. 4️⃣ Token Storage Best Practices Once the desktop app gets a token: Windows: Use Credential Locker. macOS: Use Keychain. Linux: Use libsecret or GNOME Keyring. Never store tokens in plain text. 5️⃣ Validate at the API Side Validate tokens (signature, expiration, audience). Rate-limit and monitor traffic per user or device. Check for abuse patterns (bot traffic, invalid IPs, replay attacks). 6️⃣ Extra Hardening (Optional) Use certificate pinning to detect MITM attacks. Use signed requests (HMAC) for critical actions. Pair with device attestation to detect modified clients. ✅ Summary For a secure desktop-to-API interaction: Always use HTTPS. Use OAuth 2.0 or a proven auth scheme. Store tokens securely. Validate tokens and traffic on the server. Monitor and log unusual behavior.

SafeLine WAF is a self-hosted alternative to CloudFlare WAF, protecting all application with HTTP/HTTPS protocol. It's powered by a semantic analysis engine and very easy to deploy & configure.
Website: https://ly.safepoint.cloud/ionBhgY
When a desktop application talks to a web API, the security concerns are very similar to browser or mobile apps — but there are some extra risks (like local reverse engineering or token stealing). Here’s the typical secure approach:
1️⃣ Use HTTPS (TLS) — always
All communication between your desktop app and the API should go over HTTPS to:
- Encrypt the data
- Prevent eavesdropping
- Ensure server authenticity via certificates
2️⃣ Use Proper Authentication Mechanisms
| Scenario | Recommended Method |
|---|---|
| User-specific access | OAuth 2.0 Authorization Code Flow |
| Device-specific access | OAuth 2.0 Device Code Flow / mTLS |
| Application-level (no user) | API Key + Signature / mTLS |
OAuth 2.0 is the most common and secure way for desktop apps to authenticate the user and obtain access tokens for API calls.
3️⃣ Avoid Embedding Secrets in the App
Desktop binaries can be decompiled. Avoid hardcoded secrets.
Solutions:
- Use dynamic secret exchange (OAuth flow).
- Offload sensitive logic to the server.
- Use certificate pinning to prevent TLS interception.
4️⃣ Token Storage Best Practices
Once the desktop app gets a token:
- Windows: Use Credential Locker.
- macOS: Use Keychain.
- Linux: Use libsecret or GNOME Keyring.
Never store tokens in plain text.
5️⃣ Validate at the API Side
- Validate tokens (signature, expiration, audience).
- Rate-limit and monitor traffic per user or device.
- Check for abuse patterns (bot traffic, invalid IPs, replay attacks).
6️⃣ Extra Hardening (Optional)
- Use certificate pinning to detect MITM attacks.
- Use signed requests (HMAC) for critical actions.
- Pair with device attestation to detect modified clients.
✅ Summary
For a secure desktop-to-API interaction:
- Always use HTTPS.
- Use OAuth 2.0 or a proven auth scheme.
- Store tokens securely.
- Validate tokens and traffic on the server.
- Monitor and log unusual behavior.


































































![Apple Watch Series 10 Back On Sale for $299! [Lowest Price Ever]](https://www.iclarified.com/images/news/96657/96657/96657-640.jpg)
![Apple Slips to Fifth in China's Smartphone Market with 9% Decline [Report]](https://www.iclarified.com/images/news/97065/97065/97065-640.jpg)
![EU Postpones Apple App Store Fines Amid Tariff Negotiations [Report]](https://www.iclarified.com/images/news/97068/97068/97068-640.jpg)












![What’s new in Android’s April 2025 Google System Updates [U: 4/18]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/01/google-play-services-3.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)





























































































_Andreas_Prott_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)






















































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)