AirPlay Zero-Click RCE Vulnerability Enables Remote Device Takeover via Wi-Fi
A critical vulnerability in Apple’s AirPlay protocol, dubbed AirBorne, has exposed over 2.35 billion active Apple devices and tens of millions of third-party gadgets to remote code execution (RCE) attacks requiring no user interaction. Researchers at Oligo Security discovered that the flaw allows attackers on the same Wi-Fi network to hijack devices ranging from Macs […] The post AirPlay Zero-Click RCE Vulnerability Enables Remote Device Takeover via Wi-Fi appeared first on Cyber Security News.

A critical vulnerability in Apple’s AirPlay protocol, dubbed AirBorne, has exposed over 2.35 billion active Apple devices and tens of millions of third-party gadgets to remote code execution (RCE) attacks requiring no user interaction.
Researchers at Oligo Security discovered that the flaw allows attackers on the same Wi-Fi network to hijack devices ranging from Macs and iPhones to CarPlay-enabled vehicles and smart speakers.
AirBorne Vulnerabilities
The Airborne vulnerabilities stem from flaws in Apple’s AirPlay protocol and its Software Development Kit (SDK), which third-party manufacturers use to integrate AirPlay compatibility. Oligo identified 23 vulnerabilities, 17 of which received CVE designations, including:
- CVE-2025-24252: A use-after-free flaw in macOS’s AirPlay implementation that, when chained with authentication bypass (CVE-2025-24206), enables zero-click RCE on devices set to “Anyone on the same network”.
- CVE-2025-24132: A stack-based buffer overflow in the AirPlay SDK affecting speakers, TVs, and CarPlay systems, allowing wormable zero-click exploits.
- CVE-2025-24271: An access control list (ACL) bypass lets attackers send unauthenticated AirPlay commands, which can be weaponized with other flaws for one-click RCE.
These vulnerabilities exploit AirPlay’s handling of property lists (plists), structured data formats used to serialize commands. Improper validation of plist parameters, such as assuming all inputs are dictionaries, led to type confusion, memory corruption, and arbitrary code execution.
For example, sending malformed plists via the /setProperty command crashes the ControlCenter process, while flooding RTSP SETUP requests can overload the WindowServer service, forcibly logging users out.
Attack Vectors and Real-World Impact
Attackers can leverage Airborne in multiple scenarios:
Macs and iOS devices with AirPlay receiver enabled (default: “Current User”) are vulnerable to zero-click attacks if paired with CVE-2025-24206. Oligo demonstrated exploiting this to overwrite memory in Apple’s Music app, potentially spreading malware across networks.
Third-party speakers and CarPlay units using the vulnerable SDK are equally at risk. Researchers hijacked a Bose speaker to display custom logos and audio.
The buffer overflow (CVE-2025-24132) permits self-propagating attacks. A compromised device on a corporate network could infect others without user interaction, enabling lateral movement for espionage or ransomware. Public Wi-Fi hotspots, like those in airports, are prime targets for mass exploitation.
Over 800 car models with wireless CarPlay are vulnerable to proximity-based attacks. If a vehicle’s Wi-Fi hotspot uses a weak password, attackers within range can execute RCE to manipulate infotainment systems-playing disruptive audio, tracking locations, or eavesdropping via built-in microphones. Bluetooth-based pairing (requiring PIN entry) and USB connections also pose risks.
Apple’s Response and Patch Status
Apple released patches in macOS Sequoia 15.4, iOS 18.4, and AirPlay SDK 2.7.1/3.6.0.126 to address these issues. However, Oligo warns that many third-party devices may remain unpatched indefinitely due to fragmented update mechanisms.
Gal Elbaz, Oligo’s co-founder, emphasized, “AirPlay’s integration into diverse ecosystems means some devices will linger vulnerable for years”.
To minimize exposure:
- Update Apple Devices: Ensure all Apple products run the latest OS versions.
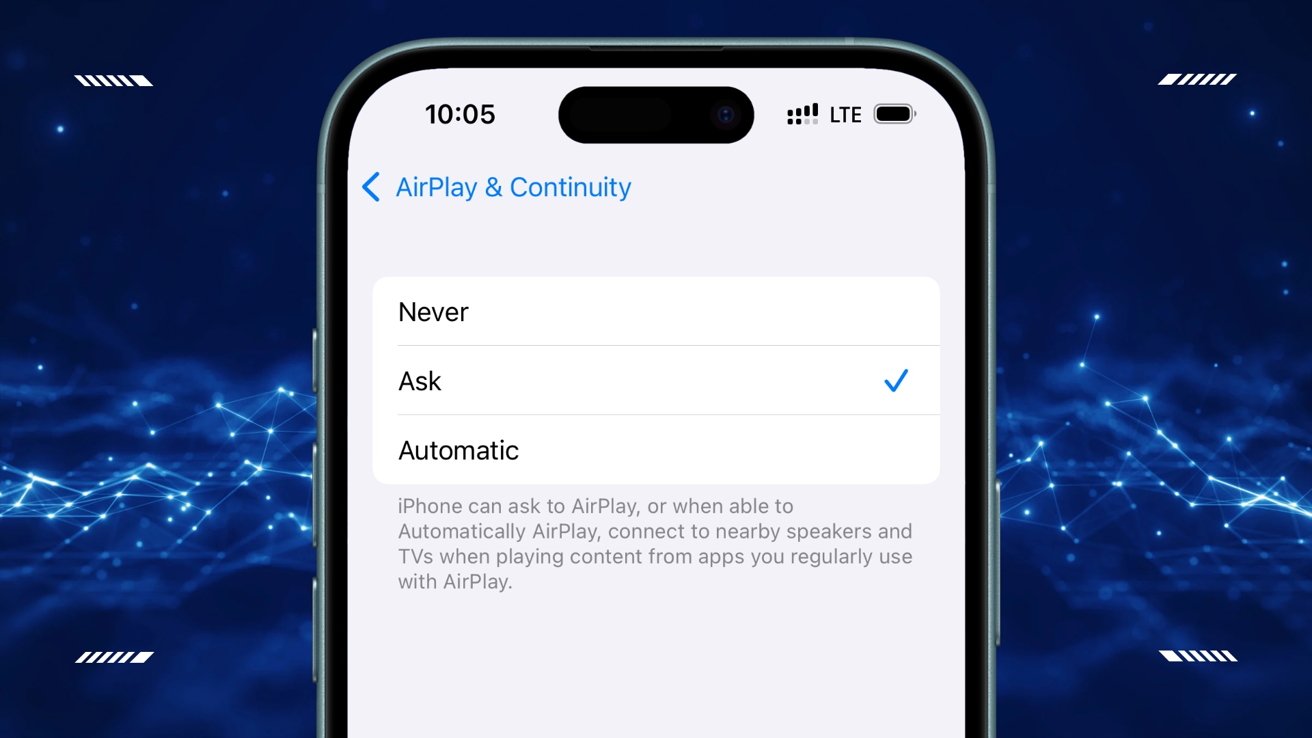
- Disable AirPlay Receiver: Turn off AirPlay in settings if unused.
- Network Hardening: Restrict port 7000 (AirPlay) to trusted devices via firewalls.
- Third-Party Vigilance: Contact manufacturers for SDK updates and monitor for firmware patches.
The AirBorne flaws underscore systemic risks in widely adopted protocols. As Apple’s ecosystem expands- 2.35 billion active devices as of January 2025- and third-party integrations proliferate, coordinated disclosure and rapid patching are critical.
Yet, the longevity of unpatched devices in consumer and industrial settings remains a persistent challenge, highlighting the need for proactive security frameworks in IoT development.
Apple has not reported active exploitation but has confirmed the severity of the vulnerabilities, urging immediate updates. For enterprises, Oligo recommends segmenting networks to isolate AirPlay-enabled devices and auditing connected endpoints for signs of compromise.
Are you from the SOC and DFIR Teams? – Analyse Malware Incidents & get live Access with ANY.RUN -> Start Now for Free.
The post AirPlay Zero-Click RCE Vulnerability Enables Remote Device Takeover via Wi-Fi appeared first on Cyber Security News.



































































![Standalone Meta AI App Released for iPhone [Download]](https://www.iclarified.com/images/news/97157/97157/97157-640.jpg)


































































































































































































































![[The AI Show Episode 145]: OpenAI Releases o3 and o4-mini, AI Is Causing “Quiet Layoffs,” Executive Order on Youth AI Education & GPT-4o’s Controversial Update](https://www.marketingaiinstitute.com/hubfs/ep%20145%20cover.png)


































































































































































































.jpg?#)