Cluster Security Standards Enforcement Via Kyverno (Policy as Code)
Kyverno, an open-source Kubernetes policy engine that lets you write policies as simple YAML manifests. Kyverno has become increasingly important in today’s cloud-native world due to the growing adoption of Kubernetes and the increasing demand for security, compliance, and automation in cluster management. Why Kyverno: Security & Policy Enforcement Today more and more organizations adopt Kubernetes, and managing multi-tenant clusters securely becomes critical. Kyverno helps you Enforcing Pod Security Standards -- Ensuring network policies are always defined -- Preventing usage of deprecated APIs Automated Governance & Compliance Regulatory requirements such as GDPR and HIPAA need consistent policy enforcement. Kyverno helps you; -- Automate auditing of non-compliant resources -- Ensure labels, annotations, or resource limits are always set -- Implement multi-cluster governance -- Policy as Code, Kubernetes-Native Unlike OPA/Gatekeeper, which uses a separate language—Rego, Kyverno Uses Kubernetes-native YAML for policies. -- Easier for K8s users to adopt -- Policies look like other Kubernetes resources -- Great fit for GitOps workflows such as ArgoCD and Flux Mutation & Generation Capabilities Kyverno can mutate and generate resources dynamically -- Auto-inject sidecars/configurations -- Generate default network policies/configmaps -- Patch fields in newly created resources. Validation at Admission Time Kyverno policies work with the Kubernetes Admission Controller to prevent invalid/non-compliant configurations before they go live. -- Helps shift security and compliance left -- Reduces production incidents due to misconfigurations Multi-cloud, Multi-cluster Support With teams running hybrid environments across AWS, Azure, GCP, and on-prem, Kyverno ensures policy consistency across clusters. Some of the cases we can use keyverno includes Block the creation of privileged pods (a common security best practice) Enforce resource requests/limits Label enforcement for workloads Time for some hands-on! Lets see it in action with a simple demo to grasp the power of kyverno Install Kyverno: run the below command in your terminal to install Kyverno kubectl create -f https://raw.githubusercontent.com/kyverno/kyverno/main/config/release/install.yaml Follow the below instructions to enforce resource requests and limits—this ensures that every container in a pod has CPU and memory requests and limits set. require-resources.yaml apiVersion: kyverno.io/v1 kind: ClusterPolicy metadata: name: require-resources spec: validationFailureAction: Enforce rules: - name: check-resources match: resources: kinds: - Pod validate: message: "CPU and memory requests/limits must be set for all containers." foreach: - list: "spec.containers[]" pattern: resources: requests: memory: "?*" cpu: "?*" limits: memory: "?*" cpu: "?*" Run the below command, which will apply the “require-resources” policy to your Kubernetes cluster. kubectl apply -f require-resources.yaml Okay, now run the below code block in your terminal to create a resource and test the policy enforcement in action. cat
Kyverno, an open-source Kubernetes policy engine that lets you write policies as simple YAML manifests.
Kyverno has become increasingly important in today’s cloud-native world due to the growing adoption of Kubernetes and the increasing demand for security, compliance, and automation in cluster management.
Why Kyverno:
Security & Policy Enforcement
Today more and more organizations adopt Kubernetes, and managing multi-tenant clusters securely becomes critical. Kyverno helps youEnforcing Pod Security Standards
-- Ensuring network policies are always defined
-- Preventing usage of deprecated APIsAutomated Governance & Compliance
Regulatory requirements such as GDPR and HIPAA need consistent policy enforcement. Kyverno helps you;
-- Automate auditing of non-compliant resources
-- Ensure labels, annotations, or resource limits are always set
-- Implement multi-cluster governance
-- Policy as Code, Kubernetes-NativeUnlike OPA/Gatekeeper, which uses a separate language—Rego, Kyverno
Uses Kubernetes-native YAML for policies.
-- Easier for K8s users to adopt
-- Policies look like other Kubernetes resources
-- Great fit for GitOps workflows such as ArgoCD and FluxMutation & Generation Capabilities
Kyverno can mutate and generate resources dynamically
-- Auto-inject sidecars/configurations
-- Generate default network policies/configmaps
-- Patch fields in newly created resources.Validation at Admission Time Kyverno policies work with the Kubernetes Admission Controller to prevent invalid/non-compliant configurations before they go live.
-- Helps shift security and compliance left
-- Reduces production incidents due to misconfigurationsMulti-cloud, Multi-cluster Support With teams running hybrid environments across AWS, Azure, GCP, and on-prem, Kyverno ensures policy consistency across clusters.
Some of the cases we can use keyverno includes
- Block the creation of privileged pods (a common security best practice)
- Enforce resource requests/limits
- Label enforcement for workloads
Time for some hands-on!
Lets see it in action with a simple demo to grasp the power of kyverno
Install Kyverno: run the below command in your terminal to install Kyverno
kubectl create -f https://raw.githubusercontent.com/kyverno/kyverno/main/config/release/install.yaml
- Follow the below instructions to enforce resource requests and limits—this ensures that every container in a pod has CPU and memory requests and limits set.
require-resources.yaml
apiVersion: kyverno.io/v1
kind: ClusterPolicy
metadata:
name: require-resources
spec:
validationFailureAction: Enforce
rules:
- name: check-resources
match:
resources:
kinds:
- Pod
validate:
message: "CPU and memory requests/limits must be set for all containers."
foreach:
- list: "spec.containers[]"
pattern:
resources:
requests:
memory: "?*"
cpu: "?*"
limits:
memory: "?*"
cpu: "?*"
Run the below command, which will apply the “require-resources” policy to your Kubernetes cluster.
kubectl apply -f require-resources.yaml
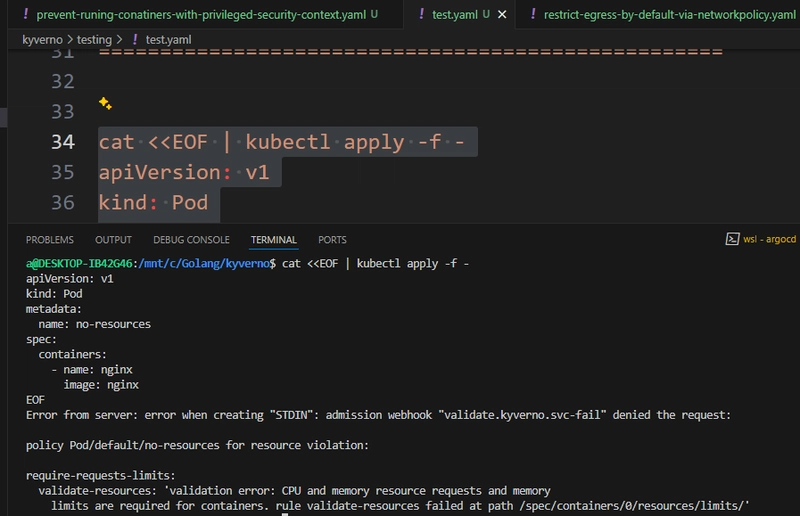
Okay, now run the below code block in your terminal to create a resource and test the policy enforcement in action.
cat <You should see an error message as shown in the above screen capture, which details the reason for the error.
Okay, now let's do this.
Now, let's add the resource limits and try the resource creation. For that, run the below code in your terminal.
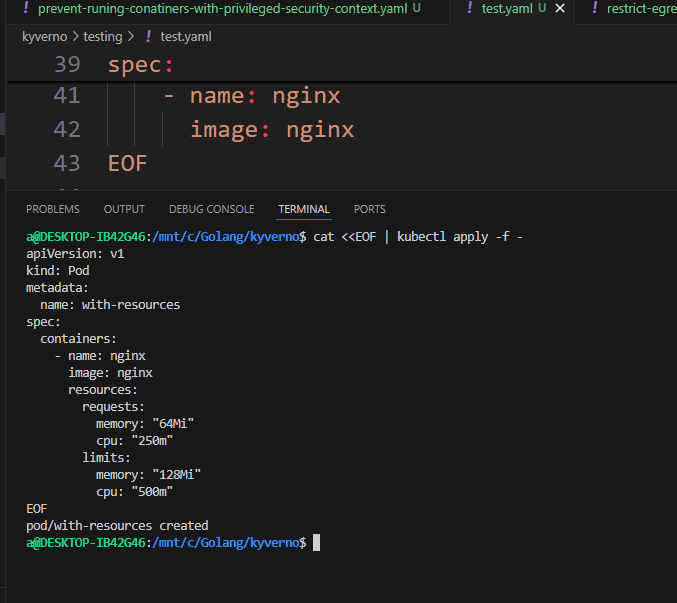
You can see the resource created message, as now the resource you have created complies with the policy requirements.
Important — validationFailureAction
The **validationFailureAction** field in Kyverno policies determines how the policy behaves when a validation rule fails:
enforce: The policy will block the resource from being created or updated if it does not comply with the policy.
audit: The policy will allow the resource to be created or updated but will log a warning or violation in the policy report.
This is just one of the many possibilities of Kyverno policy enforcement, and you can explore those also in a similar fashion.
Hope the information is useful. Thank you for your time








































































![Standalone Meta AI App Released for iPhone [Download]](https://www.iclarified.com/images/news/97157/97157/97157-640.jpg)





































































































































































































































![[The AI Show Episode 145]: OpenAI Releases o3 and o4-mini, AI Is Causing “Quiet Layoffs,” Executive Order on Youth AI Education & GPT-4o’s Controversial Update](https://www.marketingaiinstitute.com/hubfs/ep%20145%20cover.png)