Google says hackers used app specific passwords to bypass MFA in a targeted attack
Google has published an article that confirms hackers bypassed Gmail's multifactor authentication (MFA) to breach an individual's account. No, it probably won't happen to you, because this was a targeted attack. The […] Thank you for being a Ghacks reader. The post Google says hackers used app specific passwords to bypass MFA in a targeted attack appeared first on gHacks Technology News.
Google has published an article that confirms hackers bypassed Gmail's multifactor authentication (MFA) to breach an individual's account. No, it probably won't happen to you, because this was a targeted attack.
The Google Threat Intelligence Group (GTIG) has explained what happened on Google's blog. It worked with Citizen Lab, which is known for its investigative reports, to probe the incident.
GITG had observed that hackers had crafted a sophisticated, personal, social engineering attack to target Keir Giles, a prominent British researcher on Russia. Google's team has labeled the threat actor as UNC6293, a likely Russia state-sponsored cyber actor, and links them with low confidence to APT29 / ICECAP (also called Cozy Bear), which has ties to Russia's Foreign Intelligence Service (SVR).
We have seen phishing attacks that involved messaging apps, and mercenary spyware such as Pegasus, but these hackers used a new technique. They had taken precautions to prevent Mr. Giles from getting suspicious. On May 22, 2025, the attackers impersonated a U.S. State Department official, "Claudie S. Weber", in an email that invited Mr. Giles for a private online consultation to discuss something in his field of expertise. The hacker simply used a Gmail address, but had CC-ed 4 @state.gov email addresses, likely to pose as a legitimate sender, and they had sent the email during Washington D.C. working hours too. In reality, the .gov addresses likely do not exist. Citizen Lab says that the language and grammar seems to suggest that the hackers had used a large language model or some similar AI tools to craft the emails.
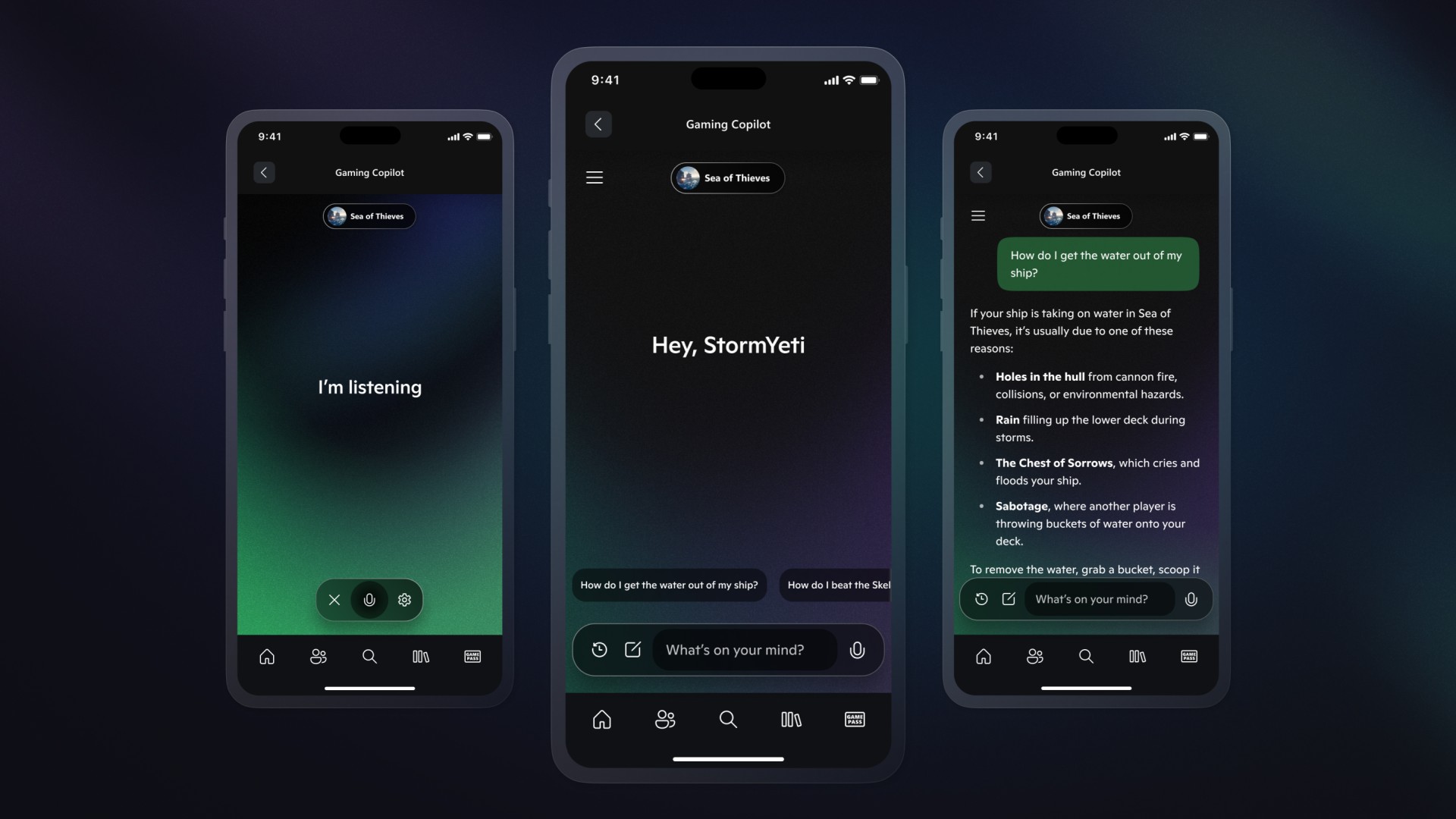
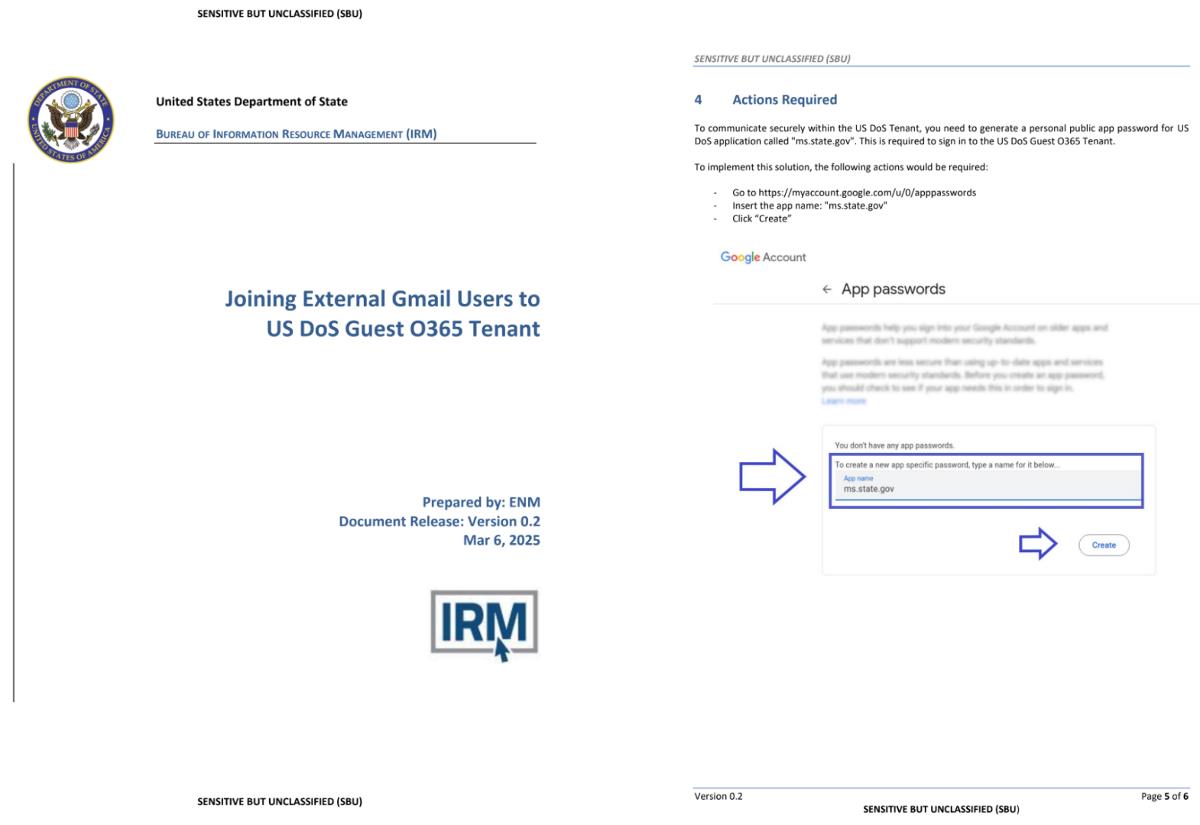
Mr. Giles replied that the date may not work for him, to which the attacker replied inviting him to register for an account the State Department’s “MS DoS Guest Tenant” platform, where he would be able to attend future meetings with ease, wherever they take place. About 10 email exchanges later, the hacker sent the victim a PDF file with details on how to register for the said account. The PDF in question was carefully crafted to look like an official document and contained markings, revision history.
This is where the mystery unfolded, as the PDF contained instructions to create an app-specific password for his Gmail account. Google says that this threat actor had targeted prominent academics and critics of Russia from early April to June 2025, building rapport, luring them to set up app specific passwords (ASPs), which they then exploit to gain persistent access to the victim's mailbox. Unfortunately, Mr. Giles was tricked by the patient, clever hackers, into creating ASPs for his accounts.
Google says it identified the attack and managed to lock down the impacted accounts, while blocking the attacker's emails. This is when Mr. Giles had discovered that a suspicious login attempt had been made in early June. An extensive report of the incident has been published by the security researches at Citizen Lab.
GITG says there was a similar-crafted attack that involved a campaign with a Ukrainian theme and a Microsoft ASP, where the attackers directed the target to share the app specific password with them, to set up a mail client and spy on their email correspondence.
This is a rare case scenario in which attackers targeted a person of interest. I'm not saying this won't happen to us commoners, but the fact that app specific passwords were used to hack the account is concerning. Just be careful which app you're signing in to using ASPs, or avoid them altogether and use OAuth to sign in to apps with your Google account, or Apple's, etc. In case you fear being state sponsored attacks, you can enable Lockdown Mode on your iPhone, or Advanced Protection Mode on Android.
While we are on the topic of security, there are reports circling around which state that 16 Billion passwords were exposed in a data breach, and that this data includes user credentials for Google, Facebook, Apple, etc. Bleeping Computer says this wasn't a breach at all, rather this is just a dataset, i.e. a collection of previous data breaches.
Google recently advised users to stop using passwords in favor of passkeys, and social sign-ins. I think this story provides some better context to its recommendation.
Thank you for being a Ghacks reader. The post Google says hackers used app specific passwords to bypass MFA in a targeted attack appeared first on gHacks Technology News.



































































![Apple Seeds tvOS 26 Beta 2 to Developers [Download]](https://www.iclarified.com/images/news/97691/97691/97691-640.jpg)
![Apple Seeds watchOS 26 Beta 2 to Developers [Download]](https://www.iclarified.com/images/news/97688/97688/97688-640.jpg)
![Apple Releases iOS 26 Beta 2 and iPadOS 26 Beta 2 [Download]](https://www.iclarified.com/images/news/97685/97685/97685-640.jpg)
![Apple Seeds visionOS 26 Beta 2 to Developers [Download]](https://www.iclarified.com/images/news/97693/97693/97693-640.jpg)










































































































_marcos_alvarado_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)



















































































































![[The AI Show Episode 154]: AI Answers: The Future of AI Agents at Work, Building an AI Roadmap, Choosing the Right Tools, & Responsible AI Use](https://www.marketingaiinstitute.com/hubfs/ep%20154%20cover.png)
![[The AI Show Episode 153]: OpenAI Releases o3-Pro, Disney Sues Midjourney, Altman: “Gentle Singularity” Is Here, AI and Jobs & News Sites Getting Crushed by AI Search](https://www.marketingaiinstitute.com/hubfs/ep%20153%20cover.png)



















































































































































































.png?#)