Threat Actor Allegedly Selling FortiGate API Exploit Tool Targeting FortiOS
A threat actor has reportedly put up for sale a sophisticated FortiGate API exploit tool on a dark web marketplace, igniting significant concern within the cybersecurity community. The tool, which is being marketed for a price of $12,000 and comes with escrow services to facilitate transactions, is claimed to target Fortinet’s FortiOS systems by exploiting […] The post Threat Actor Allegedly Selling FortiGate API Exploit Tool Targeting FortiOS appeared first on Cyber Security News.

A threat actor has reportedly put up for sale a sophisticated FortiGate API exploit tool on a dark web marketplace, igniting significant concern within the cybersecurity community.
The tool, which is being marketed for a price of $12,000 and comes with escrow services to facilitate transactions, is claimed to target Fortinet’s FortiOS systems by exploiting over 170 unsecured API endpoints, giving attackers the means to harvest a wealth of sensitive information from affected devices.
Details regarding the tool’s capabilities have emerged through leaked advertisements and image postings on underground forums.
Alleged API Exploit Tool Claim
According to those disclosures, the exploit features an automated module capable of scanning and extracting data from a broad range of FortiGate firewall appliances running vulnerable FortiOS versions, specifically 7.2 and below, but also confirmed to affect earlier releases in the 6.x family.
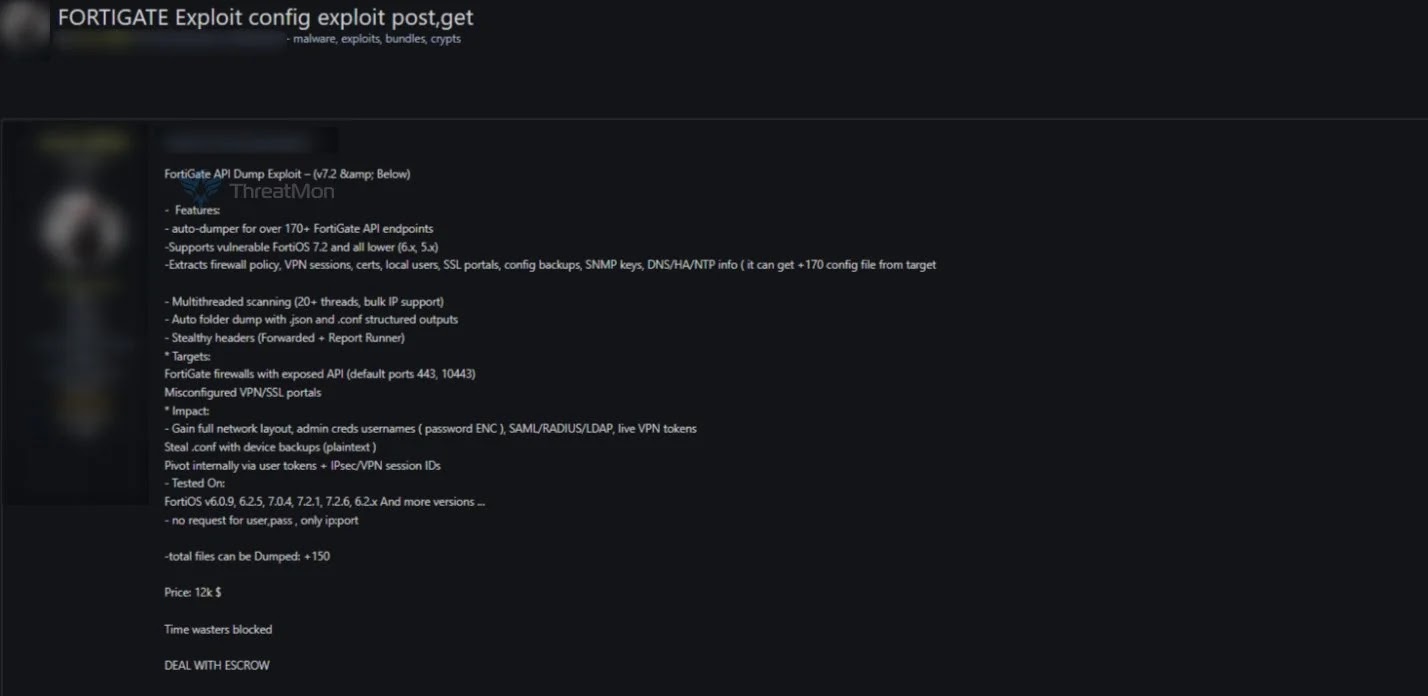
It utilizes multi-threaded techniques for rapid, bulk data extraction, enabling attackers to hit multiple targets simultaneously and dump over 150 unique configuration files in a single operation.
The exploit purportedly provides access to highly sensitive and mission-critical configuration data. Among the types of information allegedly retrievable are firewall policies, VPN session logs, user account credentials, SSL portal setups, SNMP community and encryption keys, and more esoteric network settings, including DNS, high-availability clustering, and NTP server details.
Notably, the tool claims to bypass traditional authentication, requiring only knowledge of the device’s IP address and API port typically exposed at 443 or 10443 without needing a username or password.
The impact of such unauthorized access could be severe, exposing organizational network layouts, administrator password hashes, backup configuration files, and even live authentication tokens for SAML, LDAP, RADIUS, or VPN sessions, paving the way for lateral movement or privilege escalation within enterprise environments.
Security analysts warn that the emergence of such an exploit does not merely increase the risk of opportunistic attacks but also lowers the technical barrier for less experienced malicious actors to pursue enterprise-scale breaches.
The tool’s automation, coupled with support for structured data output and stealthy HTTP header manipulation, would allow both mass exploitation campaigns and targeted espionage efforts with relative ease.
There is currently no confirmation from Fortinet as to the veracity of the exploit, but organizations running affected FortiOS versions are urged to review their security posture, restrict unauthorized API access, and apply firmware patches immediately where available.
The revelations underscore the growing risk posed by the commoditization of advanced exploitation tools in cybercriminal marketplaces, driving home the importance of constant vigilance, robust vulnerability management, and the rapid deployment of security updates in enterprise defense strategies.
Are you from SOC/DFIR Teams! - Interact with malware in the sandbox and find related IOCs. - Request 14-day free trial
The post Threat Actor Allegedly Selling FortiGate API Exploit Tool Targeting FortiOS appeared first on Cyber Security News.




































































![Apple Weighs Acquisition of AI Startup Perplexity in Internal Talks [Report]](https://www.iclarified.com/images/news/97674/97674/97674-640.jpg)

![Oakley and Meta Launch Smart Glasses for Athletes With AI, 3K Camera, More [Video]](https://www.iclarified.com/images/news/97665/97665/97665-640.jpg)


















![Apple tells students ‘how to convince your parents to get you a Mac’ [Update: Removed]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2025/06/screenshot-2025-06-20-at-09.14.21.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)
























































































_Paul_Markillie_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)















































































































![[The AI Show Episode 154]: AI Answers: The Future of AI Agents at Work, Building an AI Roadmap, Choosing the Right Tools, & Responsible AI Use](https://www.marketingaiinstitute.com/hubfs/ep%20154%20cover.png)
![[The AI Show Episode 153]: OpenAI Releases o3-Pro, Disney Sues Midjourney, Altman: “Gentle Singularity” Is Here, AI and Jobs & News Sites Getting Crushed by AI Search](https://www.marketingaiinstitute.com/hubfs/ep%20153%20cover.png)



































































































![[FREE EBOOKS] The Chief AI Officer’s Handbook, Natural Language Processing with Python & Four More Best Selling Titles](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)














































































































































.webp?#)