Critical Open Source Easyjson Library Under Full Control of Russian Company
A critical security revelation has sent shockwaves through the cybersecurity community as researchers uncovered that easyjson, a widely adopted open-source Go package central to JSON serialization processes, is under complete control of developers based in Moscow who work for VK Group, one of Russia’s largest internet conglomerates. The library serves as a foundational component for […] The post Critical Open Source Easyjson Library Under Full Control of Russian Company appeared first on Cyber Security News.

A critical security revelation has sent shockwaves through the cybersecurity community as researchers uncovered that easyjson, a widely adopted open-source Go package central to JSON serialization processes, is under complete control of developers based in Moscow who work for VK Group, one of Russia’s largest internet conglomerates.
The library serves as a foundational component for numerous high-profile cloud-native technologies including Kubernetes, Helm, and Istio, making its foreign control a matter of significant concern for organizations worldwide.
The discovery raises alarming questions about software supply chain security as easyjson is deeply embedded in critical infrastructure systems across U.S. Government networks, Fortune 500 enterprises, and cornerstone Cloud Native Computing Foundation projects.
Its specialized functionality in optimizing JSON encoding and decoding has made it an essential dependency in high-performance computing environments, particularly those requiring rapid data serialization for financial platforms and analytics systems.
Hunted Labs researchers identified this concerning ownership pattern while conducting security analysis for a U.S. Government client.
Their investigation revealed that over 85% of all commits to the easyjson repository came from Moscow-based developers affiliated with VK Group, a company currently under scrutiny for its connections to Russian state security services and subject to various international sanctions.
The situation is particularly troubling given VK’s documented history of cooperating with Kremlin directives and sharing user data with Russian authorities.
VK Group, also known as Mail.ru, is controlled by Russian state-owned entities through Gazprom Media and has leadership members who are currently subject to both U.S. and E.U. sanctions, according to multiple government sources and regulatory filings.
Security experts warn that this level of foreign control over critical infrastructure code presents a significant national security vulnerability, especially given the current geopolitical landscape and Russia’s documented history of cyber operations against Western targets.
The library’s deep integration into core systems makes it nearly impossible to quickly remove or replace without substantial disruption to dependent services.
Potential Exploitation Vectors
The controlled positioning of easyjson presents several concerning exploitation scenarios that security professionals must consider.
As a serializer implemented in the Go language, easyjson occupies a particularly sensitive position in application architectures.
While there is no evidence of current malicious activity, the strategic placement of the library creates unique security challenges.
// Example of how easyjson generates custom marshalers
// that have deep access to data structures
func (j *SensitiveData) MarshalJSON() ([]byte, error) {
// Custom generated code that processes all data fields
// with potential for subtle manipulation
return json.Marshal(&struct{
UserID string `json:"user_id"`
AuthToken string `json:"auth_token"`
PrivateData string `json:"private_data"`
}{
UserID: j.UserID,
AuthToken: j.AuthToken,
PrivateData: j.PrivateData,
})
}The serialization and deserialization processes handle sensitive data structures that often contain credentials, authentication tokens, and proprietary information.
A compromised JSON parser could selectively exfiltrate specific data fields while maintaining normal application functionality, making detection extremely difficult.
Since easyjson generates Go code that handles data marshaling at the byte level, subtle manipulations could introduce information leakage channels without triggering security alerts.
Security researchers at Hunted Labs emphasize that the risk isn’t necessarily about current code integrity but rather the continuous trusted access maintained by developers affiliated with entities under sanction.
The recommended mitigation strategies include forking and self-maintaining the library, transitioning to alternative JSON serialization tools with diverse maintenance communities, or collaborating on a community-led replacement with transparent governance mechanisms.
Are you from the SOC and DFIR Teams? – Analyse Real time Malware Incidents with ANY.RUN -> Start Now for Free.
The post Critical Open Source Easyjson Library Under Full Control of Russian Company appeared first on Cyber Security News.




























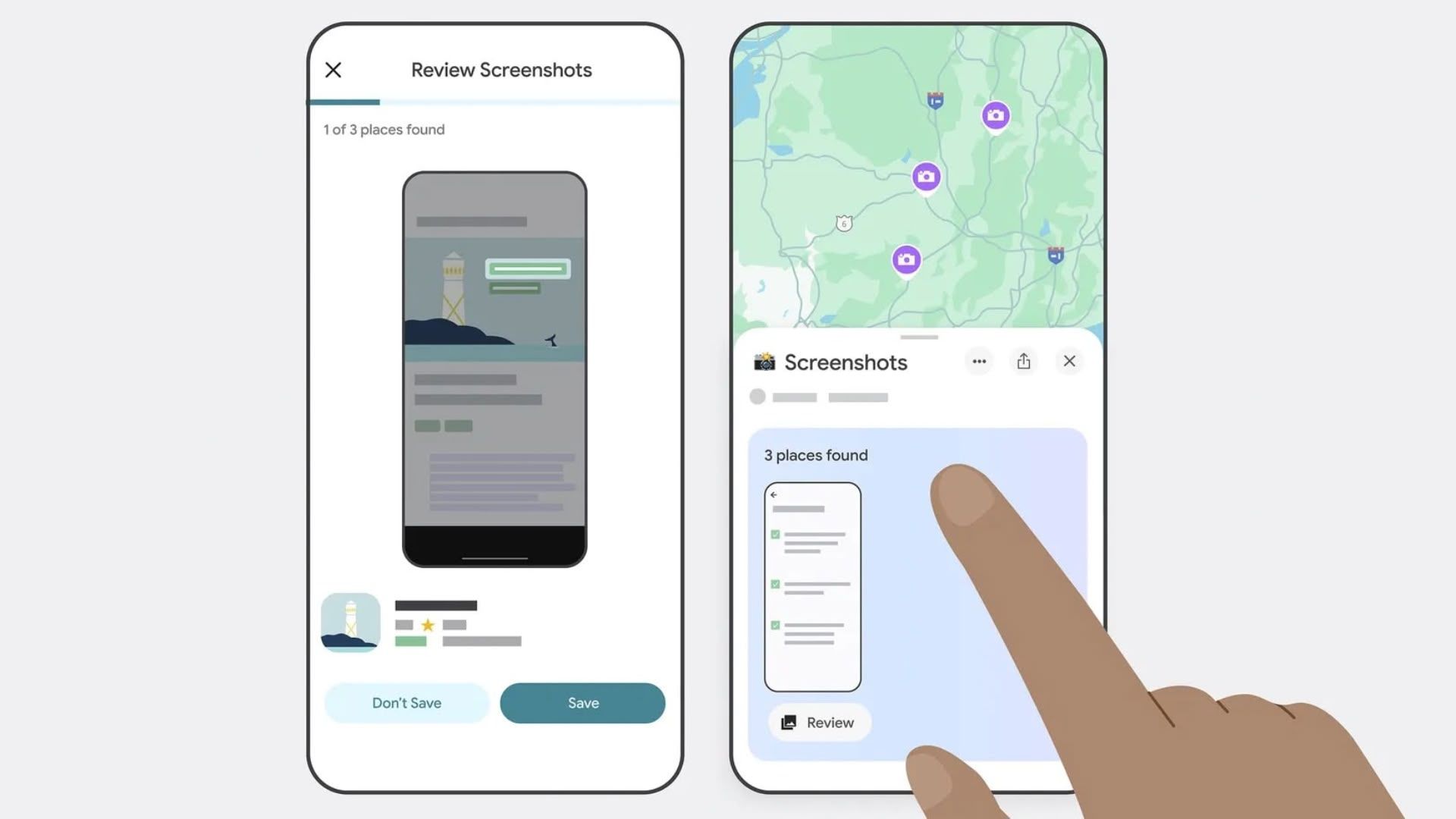









































![Beats Studio Pro Wireless Headphones Now Just $169.95 - Save 51%! [Deal]](https://www.iclarified.com/images/news/97258/97258/97258-640.jpg)















![Honor 400 series officially launching on May 22 as design is revealed [Video]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/05/honor-400-series-announcement-1.png?resize=1200%2C628&quality=82&strip=all&ssl=1)































































































































































































































![[The AI Show Episode 146]: Rise of “AI-First” Companies, AI Job Disruption, GPT-4o Update Gets Rolled Back, How Big Consulting Firms Use AI, and Meta AI App](https://www.marketingaiinstitute.com/hubfs/ep%20146%20cover.png)
















































































































![[DEALS] The Premium Python Programming PCEP Certification Prep Bundle (67% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)













































































































































.webp?#)
