New ClickFix Attack Exploits Fake Cloudflare Human Check to Install Malware Silently
A sophisticated new social engineering attack campaign has emerged that exploits users’ familiarity with routine security checks to deliver malware through deceptive Cloudflare verification pages. The ClickFix attack technique represents a concerning evolution in phishing methodology, abandoning traditional file downloads in favor of manipulating users into executing malicious commands directly on their own systems. The […] The post New ClickFix Attack Exploits Fake Cloudflare Human Check to Install Malware Silently appeared first on Cyber Security News.

A sophisticated new social engineering attack campaign has emerged that exploits users’ familiarity with routine security checks to deliver malware through deceptive Cloudflare verification pages.
The ClickFix attack technique represents a concerning evolution in phishing methodology, abandoning traditional file downloads in favor of manipulating users into executing malicious commands directly on their own systems.
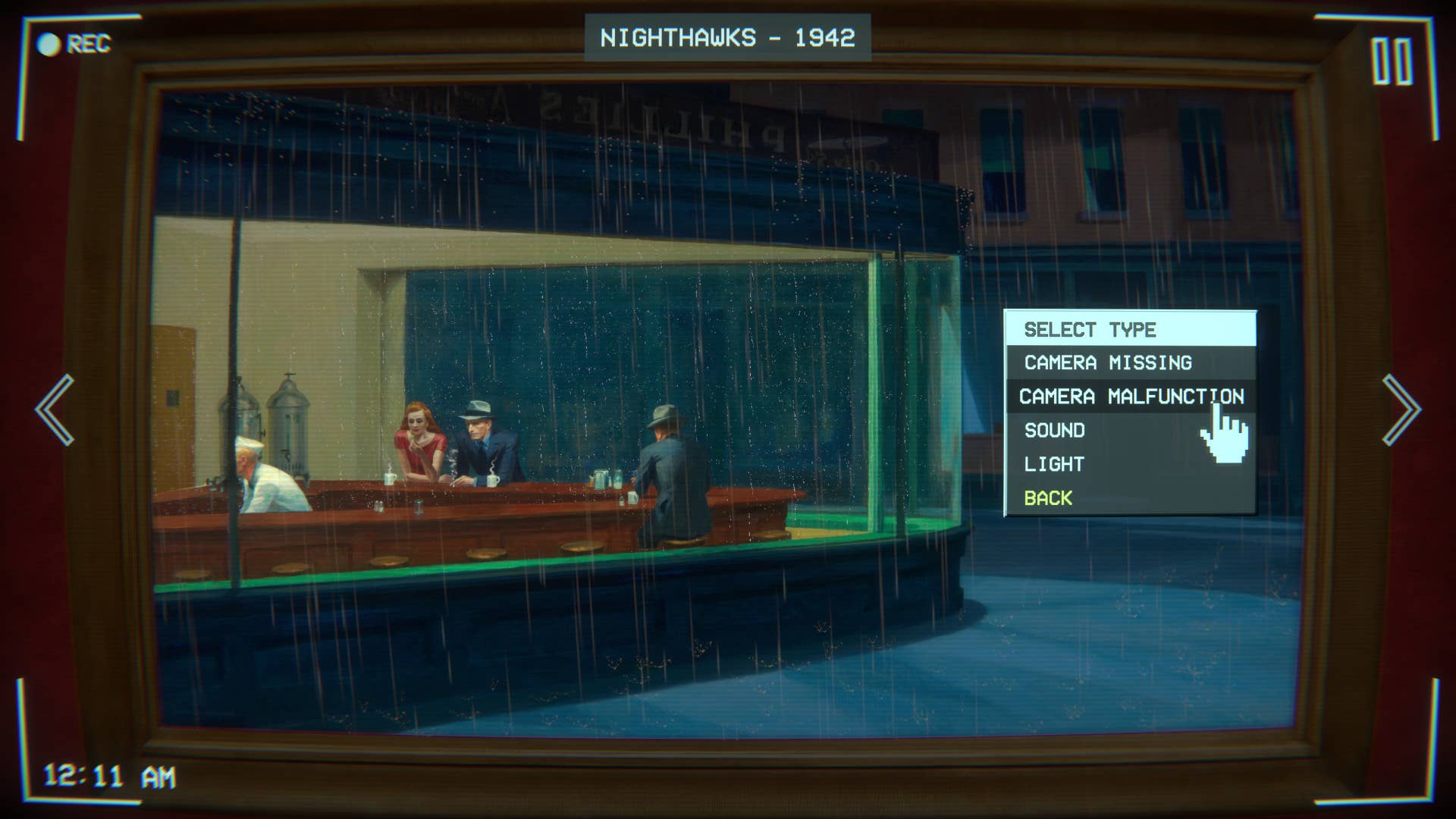
The attack operates by presenting victims with what appears to be a legitimate Cloudflare Turnstile interface, complete with official branding, authentic wording, and dynamically generated Ray IDs that reinforce the illusion of legitimacy.
When users encounter these fake verification pages, they see familiar messages such as “Checking if the site connection is secure – Verify you are human,” identical to what they would expect from genuine Cloudflare protection mechanisms.
This calculated mimicry exploits verification fatigue, a phenomenon where internet users have become conditioned to quickly click through security prompts without careful examination.
SlashNext researchers identified this emerging threat as part of their ongoing threat intelligence operations, noting the attack’s particularly insidious approach to bypassing traditional security measures.
The technique has proven remarkably effective because it leverages user trust in established security providers while requiring no sophisticated exploits or zero-day vulnerabilities.
Instead, the attack relies on convincing users to voluntarily execute malicious code under the guise of completing a routine verification process.
The campaign has been observed delivering various malware families, including information stealers like Lumma and Stealc, as well as remote access trojans such as NetSupport Manager.
The attack’s success stems from its ability to bypass traditional security filters by having users execute legitimate system utilities with malicious parameters, rather than downloading suspicious executable files.
This approach effectively circumvents many endpoint protection solutions that focus on scanning downloaded binaries.
Technical Infection Mechanism and Clipboard Exploitation
The ClickFix attack employs a sophisticated clipboard manipulation technique that occurs entirely within the victim’s browser environment.
When users interact with the fake Cloudflare verification page by clicking the “Verify you are human” checkbox, the malicious webpage’s embedded JavaScript immediately executes a hidden script that creates an invisible text element containing an obfuscated PowerShell command.
This command is automatically copied to the user’s clipboard using standard web APIs, leaving no visible indication of the clipboard compromise.
The attack page subsequently presents users with seemingly legitimate verification steps that instruct them to press specific key combinations: Windows+R to open the Run dialog box, followed by Ctrl+V to paste the clipboard contents, and finally Enter to execute the command.
By this point, the dangerous PowerShell payload is already residing in the user’s clipboard, waiting to be unknowingly executed.
The malicious command is typically structured as a one-liner that retrieves and executes second-stage malware from remote servers, often utilizing Base64 encoding or other obfuscation techniques to avoid detection.
.webp)
The initial fake Cloudflare page that users encounter at the beginning of the attack sequence.
.webp)
While this shows the step-by-step instructions that manipulate users into executing the malware payload.
.webp)
Besides this, this depicts the hidden PowerShell command that gets copied to the user’s clipboard during the verification process.
The entire attack infrastructure is contained within a single, self-contained HTML file that embeds all necessary images, styles, and scripts locally, enabling the fake page to load seamlessly on the attacker’s chosen domain without requiring external resources that might trigger security warnings.
Speed up and enrich threat investigations with Threat Intelligence Lookup! -> 50 trial search requests
The post New ClickFix Attack Exploits Fake Cloudflare Human Check to Install Malware Silently appeared first on Cyber Security News.

_sleepyfellow_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)






































































![watchOS 26 May Bring Third-Party Widgets to Control Center [Report]](https://www.iclarified.com/images/news/97520/97520/97520-640.jpg)

![AirPods Pro 2 On Sale for $169 — Save $80! [Deal]](https://www.iclarified.com/images/news/97526/97526/97526-640.jpg)










































































































_Michael_Vi_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)


















































































































![[The AI Show Episode 151]: Anthropic CEO: AI Will Destroy 50% of Entry-Level Jobs, Veo 3’s Scary Lifelike Videos, Meta Aims to Fully Automate Ads & Perplexity’s Burning Cash](https://www.marketingaiinstitute.com/hubfs/ep%20151%20cover.png)





























































































































































![From electrical engineering student to CTO with Hitesh Choudhary [Podcast #175]](https://cdn.hashnode.com/res/hashnode/image/upload/v1749158756824/3996a2ad-53e5-4a8f-ab97-2c77a6f66ba3.png?#)


![[FREE EBOOKS] Solutions Architect’s Handbook, Continuous Testing, Quality, Security, and Feedback & Four More Best Selling Titles](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)