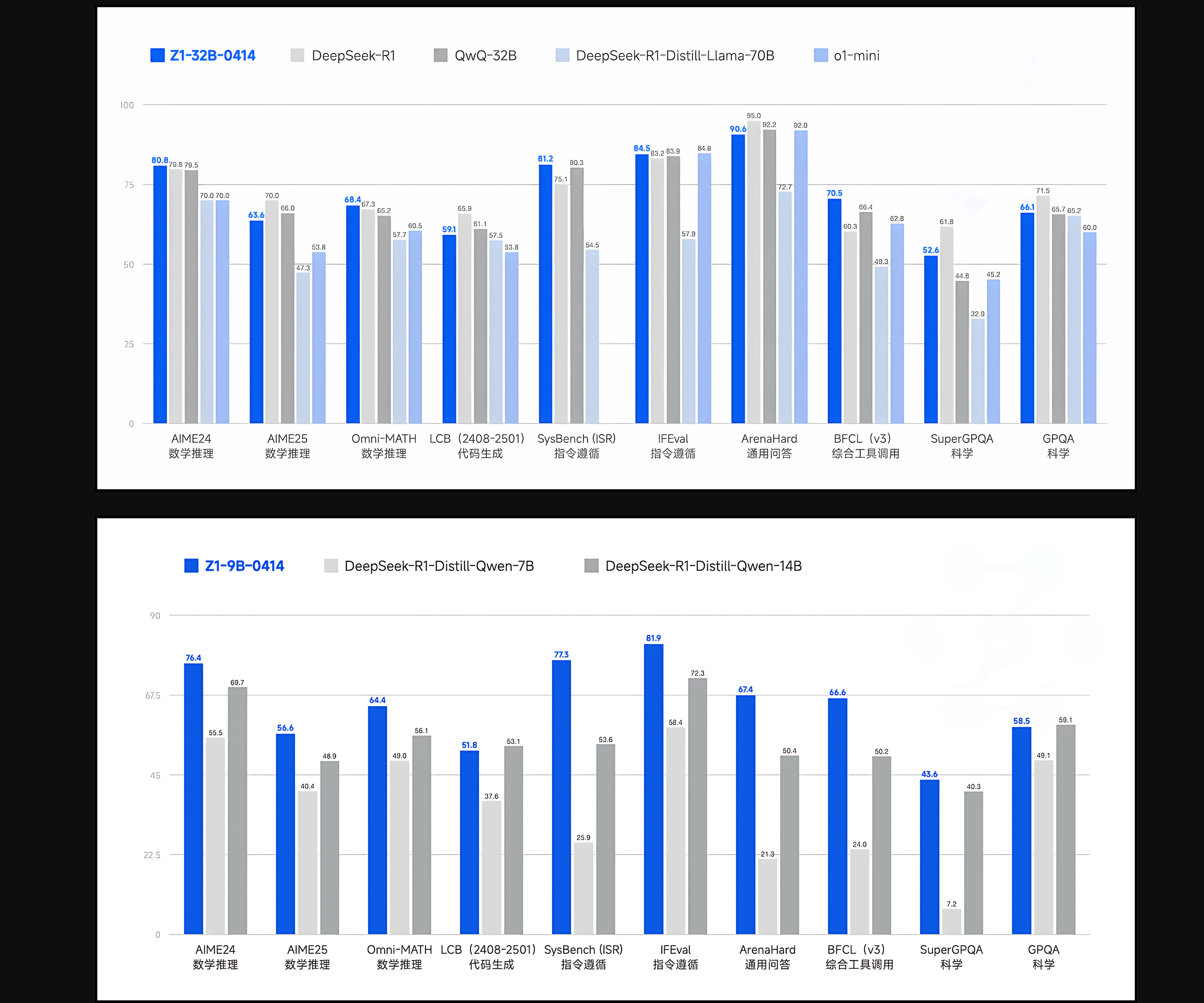
Recent Security Alerts: GitHub Actions Hijack and Kubernetes Ingress-NGINX Vulnerability
Hello friends Recently, two important security issues were brought up by Wiz. These issues affect GitHub Actions and the Kubernetes Ingress-NGINX controller. If you are working in DevOps or managing infrastructure, please take these seriously. In this blog, I will explain them in simple language and also tell you how to fix them. GitHub Actions Hijack Issue What happened? A popular GitHub Action tj-actions/changed-files was compromised Malicious code was pushed and released in a version Using @v35 or other tags may fetch compromised code What should you do? Use full commit SHA instead of version tag uses: tj-actions/changed-files@9e5e6c7f3d2b84aafc35f45d2e80b2e3a1743b70 Audit third-party actions Prefer verified sources Kubernetes Ingress-NGINX Vulnerability (CVE-2025-1974) What happened? Ingress-NGINX controller had a serious vulnerability Older versions (1.12.0 or below) allow unauthenticated command execution What should you do? Upgrade to 1.11.5 or 1.12.1 or newer Use AWS ALB Ingress Controller if on Amazon EKS Ensure ingress-nginx-controller-admission is not publicly exposed Conclusion Stay updated on security alerts Review and secure your GitHub workflows Upgrade Ingress controllers on your clusters Reach out if you need help Lakshmi Phanindra Rudra Technical Lead - DevSecOps and Cloud Engineering WinWire Technologies
Hello friends
Recently, two important security issues were brought up by Wiz. These issues affect GitHub Actions and the Kubernetes Ingress-NGINX controller. If you are working in DevOps or managing infrastructure, please take these seriously. In this blog, I will explain them in simple language and also tell you how to fix them.
GitHub Actions Hijack Issue
What happened?
- A popular GitHub Action
tj-actions/changed-fileswas compromised - Malicious code was pushed and released in a version
- Using
@v35or other tags may fetch compromised code
What should you do?
- Use full commit SHA instead of version tag
uses: tj-actions/changed-files@9e5e6c7f3d2b84aafc35f45d2e80b2e3a1743b70
- Audit third-party actions
- Prefer verified sources
Kubernetes Ingress-NGINX Vulnerability (CVE-2025-1974)
What happened?
- Ingress-NGINX controller had a serious vulnerability
- Older versions (1.12.0 or below) allow unauthenticated command execution
What should you do?
- Upgrade to 1.11.5 or 1.12.1 or newer
- Use AWS ALB Ingress Controller if on Amazon EKS
- Ensure
ingress-nginx-controller-admissionis not publicly exposed
Conclusion
- Stay updated on security alerts
- Review and secure your GitHub workflows
- Upgrade Ingress controllers on your clusters
- Reach out if you need help
Lakshmi Phanindra Rudra
Technical Lead - DevSecOps and Cloud Engineering
WinWire Technologies
.webp?#)



































































![Apple Releases iOS 18.5 Beta 2 and iPadOS 18.5 Beta 2 [Download]](https://www.iclarified.com/images/news/97007/97007/97007-640.jpg)
![Apple Seeds watchOS 11.5 Beta 2 to Developers [Download]](https://www.iclarified.com/images/news/97008/97008/97008-640.jpg)
![Apple Seeds visionOS 2.5 Beta 2 to Developers [Download]](https://www.iclarified.com/images/news/97010/97010/97010-640.jpg)












![What’s new in Android’s April 2025 Google System Updates [U: 4/14]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/01/google-play-services-3.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)

![Gemini will come to Wear OS as an app update [APK Insight]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2023/01/Google-Assistant-Wear-OS-Play-Store.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)











































































































































































![[The AI Show Episode 143]: ChatGPT Revenue Surge, New AGI Timelines, Amazon’s AI Agent, Claude for Education, Model Context Protocol & LLMs Pass the Turing Test](https://www.marketingaiinstitute.com/hubfs/ep%20143%20cover.png)