TryHackMe: NetworkMiner
Introduction to Network Forensics Network Forensics is a specific subdomain of the Forensics domain, and it focuses on network traffic investigation. Network Forensics discipline covers the work done to access information transmitted by listening and investigating live and recorded traffic, gathering evidence/artefacts and understanding potential problems. Briefly, it is the action of recording packets of network traffic and creating investigatable sources and establishing a root–cause analysis of an event. The ultimate goal is to provide sufficient information to detect malicious activities, security breaches, policy/regulation compliance, system health and user behaviour. The investigation process identifies communicated hosts in terms of time, frequency, protocol, application and data. The investigation tries to answer the 5W; Who (Source IP and port) What (Data/payload) Where (Destination IP and port) When (Time and data) Why (How/What happened) Note that the network evidence capture and investigation process should be systematic. Having enough data and the right timeline capture for a successful network forensics investigation is crucial. Network Forensics Use Cases The most common network forensics use cases are explained below; Network discovery: Discovering the network to overview connected devices, rogue hosts and network load. Packets reassembling: Reassembling the packets to investigate the traffic flow. This use case is helpful in unencrypted traffic flows. Data leakage detection: Reviewing packet transfer rates for each host and destination address helps detect possible data leakage. **Anomaly and malicious activity detection: **Reviewing overall network load by focusing on used ports, source and destination addresses, and data helps detect possible malicious activities along with vulnerabilities. This use case covers the correlation of indicators and hypotheses as well. Policy/Regulation compliance control: Reviewing overall network behaviour helps detect policy/regulation compliance. Advantages of Network Forensics General advantages of network forensics are explained below; Availability of network-based evidence in the wild: Capturing network traffic is collecting evidence, so it is easier than other types of evidence collections such as logs and IOCs. Ease of data/evidence collection without creating noise: Capturing and working with network traffic is easier than investigating unfiltered events by EDRs, EPPs and log systems. Usually, sniffing doesn't create much noise, logs and alerts. The other thing is that network traffic is not destructible like logs and alerts generated by security systems. It is hard to destroy the network evidence, as it is the transferred data: Since the evidence is the traffic itself, it is impossible to do anything without creating network noise. Still, it is possible to hide the artefacts by encrypting, tunnelling and manipulating the packets. So, the second fact is the challenge of this advantage. Availability of log sources: Logs provide valuable information which helps to correlate the chain of events and support the investigation hypothesis. The majority of the EDRs, EPPs and network devices create logs by default. Having log files is easy if the attacker/threat/malware didn't erase/destroy them. It is possible to gather evidence for memory and non-residential malicious activities: The malware/threat might reside in the memory to avoid detection. However, the series of commands and connections live in the network. So it is possible to detect non-residential threats with network forensics tools and tactics. Challenges of Network Forensics General challenges of the network forensics are explained below; Deciding what to do: One of the most difficult challenges of network forensics is "Deciding what to do". There are several purposes of carving networks; SOC, IH/IR and Threat Hunting. Observing, trapping, catching, or stopping an anomalous activity is also possible. Sufficient data/evidence collection on the network: One of the advantages of network forensics is "Ease of collecting evidence". However, the breadth of this concept poses a challenge. There are multiple points to consider in data/evidence collection. Short data capture: One of the challenges in data/evidence collection. Capturing all network activity is not applicable and operable. So, it is hard always to have the packet captures that covers pre, during and post-event. The unavailability of full-packet capture on suspicious events: Continuously capturing, storing and processing full-packets costs time and resources. The inability to have full-packet captures for a long time creates time gaps between captures, resulting in missing a significant part of an event of interest. Sometimes NetFlow captures are used instead of full-packet captures to reduce the weight of having full-packet captures and increase the capture time. Note t

Introduction to Network Forensics
Network Forensics is a specific subdomain of the Forensics domain, and it focuses on network traffic investigation. Network Forensics discipline covers the work done to access information transmitted by listening and investigating live and recorded traffic, gathering evidence/artefacts and understanding potential problems.
Briefly, it is the action of recording packets of network traffic and creating investigatable sources and establishing a root–cause analysis of an event. The ultimate goal is to provide sufficient information to detect malicious activities, security breaches, policy/regulation compliance, system health and user behaviour.
The investigation process identifies communicated hosts in terms of time, frequency, protocol, application and data.
The investigation tries to answer the 5W;
- Who (Source IP and port)
- What (Data/payload)
- Where (Destination IP and port)
- When (Time and data)
- Why (How/What happened)
Note that the network evidence capture and investigation process should be systematic. Having enough data and the right timeline capture for a successful network forensics investigation is crucial.
Network Forensics Use Cases
The most common network forensics use cases are explained below;
- Network discovery: Discovering the network to overview connected devices, rogue hosts and network load.
- Packets reassembling: Reassembling the packets to investigate the traffic flow. This use case is helpful in unencrypted traffic flows.
- Data leakage detection: Reviewing packet transfer rates for each host and destination address helps detect possible data leakage.
- **Anomaly and malicious activity detection: **Reviewing overall network load by focusing on used ports, source and destination addresses, and data helps detect possible malicious activities along with vulnerabilities. This use case covers the correlation of indicators and hypotheses as well.
- Policy/Regulation compliance control: Reviewing overall network behaviour helps detect policy/regulation compliance.
Advantages of Network Forensics
General advantages of network forensics are explained below;
Availability of network-based evidence in the wild: Capturing network traffic is collecting evidence, so it is easier than other types of evidence collections such as logs and IOCs.
Ease of data/evidence collection without creating noise: Capturing and working with network traffic is easier than investigating unfiltered events by EDRs, EPPs and log systems. Usually, sniffing doesn't create much noise, logs and alerts. The other thing is that network traffic is not destructible like logs and alerts generated by security systems.
It is hard to destroy the network evidence, as it is the transferred data: Since the evidence is the traffic itself, it is impossible to do anything without creating network noise. Still, it is possible to hide the artefacts by encrypting, tunnelling and manipulating the packets. So, the second fact is the challenge of this advantage.
Availability of log sources: Logs provide valuable information which helps to correlate the chain of events and support the investigation hypothesis. The majority of the EDRs, EPPs and network devices create logs by default. Having log files is easy if the attacker/threat/malware didn't erase/destroy them.
It is possible to gather evidence for memory and non-residential malicious activities: The malware/threat might reside in the memory to avoid detection. However, the series of commands and connections live in the network. So it is possible to detect non-residential threats with network forensics tools and tactics.
Challenges of Network Forensics
General challenges of the network forensics are explained below;
Deciding what to do: One of the most difficult challenges of network forensics is "Deciding what to do". There are several purposes of carving networks; SOC, IH/IR and Threat Hunting. Observing, trapping, catching, or stopping an anomalous activity is also possible.
Sufficient data/evidence collection on the network: One of the advantages of network forensics is "Ease of collecting evidence". However, the breadth of this concept poses a challenge. There are multiple points to consider in data/evidence collection.
Short data capture: One of the challenges in data/evidence collection. Capturing all network activity is not applicable and operable. So, it is hard always to have the packet captures that covers pre, during and post-event.
The unavailability of full-packet capture on suspicious events: Continuously capturing, storing and processing full-packets costs time and resources. The inability to have full-packet captures for a long time creates time gaps between captures, resulting in missing a significant part of an event of interest. Sometimes NetFlow captures are used instead of full-packet captures to reduce the weight of having full-packet captures and increase the capture time. Note that full-packet captures provide full packet details and give the opportunity of event reconstruction, while NetFlow provides high-level summary but not data/payload details.
Encrypted traffic: Encrypted data is another challenge of network forensics. In most cases, discovering the contents of the encrypted data is not possible. However, the encrypted data still can provide valuable information for the hypothesis like source and destination address and used services.
GDPR and Privacy concerns in traffic recording: Capturing the traffic is the same as "recording everything on the wire"; therefore, this act should comply with GDPR and business-specific regulations (e.g. HIPAA, PCI DSS and FISMA ).
Nonstandard port usage: One of the popular approaches in network forensics investigations is grabbing the low-hanging fruits in the first investigation step. Looking for commonly used patterns (like known ports and services used in enumeration and exploitation) is known as grabbing the low-hanging fruits. However, sometimes attackers/threats use nonstandard ports and services to avoid detection and bypass security mechanisms. Therefore sometimes, this ends up as a challenge of network forensics.
Time zone issues: Using a common time zone is important for big-scale event investigation. Especially when working with multiple resources over different time zones, usage of different time zones create difficulties in event correlation.
Lack of logs: Network forensics is not limited to investigating the network traffic data. Network devices and event logs are crucial in event correlation and investigation hypotheses. This fact is known by the attackers/threats as well; therefore these logs are often erased by them, in order to make the investigation more difficult.
Sources of Network Forensics Evidence
Capturing proper network traffic requires knowledge and tools. Usually, there is a single chance of gathering the live traffic as evidence. There are multiple evidence resources to gather network forensics data.
- TAPS
- InLine Devices
- SPAN Ports
- Hubs
- Switches
- Routers
- DHCP Servers
- Name Servers
- Authentication Servers
- Firewalls
- Web Proxies
- Central Log Servers
- Logs (IDS/IPS, Application, OS, Device)
Primary Purposes of Network Forensics
There are two primary purposes in Network Forensics investigations.
Security Operations (SOC): Daily security monitoring activities on system performance and health, user behaviour, and security issues.
Incident Handling/Response and Threat Hunting: During/Post-incident investigation activities on understanding the reason for the incident, detecting malicious and suspicious activity, and investigating the data flow content.
Investigated Data Types in Network Forensics
There are three main data types investigated in Network Forensics
- Live Traffic
- Traffic Captures (full packet captures and network flows)
- Log Files
NetworkMiner is capable of processing and handling packet pictures and live traffic. Therefore, we will focus on live and captured traffic in this room. Both of these data sources are valuable for forensics investigations.
Traffic investigation actions fall under network forensics's "Traffic Analysis" subdomain. However, the main purpose of the NetworkMiner is to investigate the overall flow/condition of the limited amount of traffic, not for a long in-depth live traffic investigation. Therefore we will focus on how to use NetworkMiner for this purpose. In-depth traffic and packet analysis will be covered in the rooms below;
- Wireshark
- Tcpdump (available soon!)
- Tshark (available soon!)
What is NetworkMiner?
NetworkMiner in a Nutshell
| Capability | Description |
|---|---|
| Traffic sniffing | It can intercept the traffic, sniff it, and collect and log packets that pass through the network. |
| Parsing PCAP files | It can parse pcap files and show the content of the packets in detail. |
| Protocol analysis | It can identify the used protocols from the parsed pcap file. |
| OS fingerprinting | It can identify the used OS by reading the pcap file. This feature strongly relies on Satori and p0f. |
| File Extraction | It can extract images, HTML files, and emails from the parsed pcap file. |
| Credential grabbing | It can extract credentials from the parsed pcap file. |
| Clear text keyword parsing | It can extract cleartext keywords and strings from the parsed pcap file. |
You can see the differences between free and professional versions [here**](https://www.netresec.com/?page=NetworkMiner).**
Operating Modes
There are two main operating modes;
Sniffer Mode: Although it has a sniffing feature, it is not intended to use as a sniffer. The sniffier feature is available only on Windows. However, the rest of the features are available in Windows and Linux OS. Based on experience, the sniffing feature is not as reliable as other features. Therefore we suggest not using this tool as a primary sniffer. Even the official description of the tool mentions that this tool is a "Network Forensics Analysis Tool", but it can be used as a "sniffer". In other words, it is a Network Forensic Analysis Tool with but has a sniffer feature, but it is not a dedicated sniffer like Wireshark and tcpdump.
Packet Parsing/Processing: NetworkMiner can parse traffic captures to have a quick overview and information on the investigated capture. This operation mode is mainly suggested to grab the "low hanging fruit" before diving into a deeper investigation.
Pros and Cons
As mentioned in the previous task, NetworkMiner is mainly used to gain an overview of the network. Before starting to investigate traffic data, let's look at the pros and cons of the NetworkMiner.
Pros
- OS fingerprinting
- Easy file extraction
- Credential grabbing
- Clear text keyword parsing
- Overall overview
Cons
- Not useful in active sniffing
- Not useful for large pcap investigation
- Limited filtering
- Not built for manual traffic investigation
Differences Between Wireshark and NetworkMiner
NetworkMiner and Wireshark have similar base features, but they separate in use purpose. Although main functions are identical, some of the features are much stronger for specific use cases.
The best practice is to record the traffic for offline analysis, quickly overview the pcap with NetworkMiner and go deep with Wireshark for further investigation.
| Feature | NetworkMiner | Wireshark |
|---|---|---|
| Purpose | Quick overview, traffic mapping, and data extraction | In-Depth analysis |
| GUI | ✅ | ✅ |
| Sniffing | ✅ | ✅ |
| Handling PCAPS | ✅ | ✅ |
| OS Fingerprinting | ✅ | ❌ |
| Parameter/Keyword Discovery | ✅ | Manual |
| Credential Discovery | ✅ | ✅ |
| File Extraction | ✅ | ✅ |
| Filtering Options | Limited | ✅ |
| Packet Decoding | Limited | ✅ |
| Protocol Analysis | ❌ | ✅ |
| Payload Analysis | ❌ | ✅ |
| Statistical Analysis | ❌ | ✅ |
| Cross-Platform Support | ✅ | ✅ |
| Host Categorisation | ✅ | ❌ |
| Ease of Management | ✅ | ✅ |
Tool Overview 1
Landing Page
This is the landing page of the NetworkMiner. Once you open the application, this screen loads up.
File Menu
The file menu helps you load a Pcap file or receive Pcap over IP. You can also drag and drop pcap files as well.
NetworkMiner also can receive Pcaps over IP.
Tools Menu
The tools menu helps you clear the dashboard and remove the captured data.
Help Menu
The help menu provides information on updates and the current version.
Case Panel
The case panel shows the list of the investigated pcap files. You can reload/refresh, view metadata details and remove loaded files from this panel.
Viewing metadata of loaded files;
Hosts
The "hosts" menu shows the identified hosts in the pcap file. This section provides information on;
- IP address
- MAC address
- OS type
- Open ports
- Sent/Received packets
- Incoming/Outgoing sessions
- Host details
OS fingerprinting uses the Satori GitHub repo and p0f, and the MAC address database uses the mac-ages GitHub repo.
You can sort the identified hosts by using the sort menu. You can change the colour of the hosts as well. Some of the features (OSINT lookup) are available only in premium mode. The right-click menu also helps you to copy the selected value.
Sessions
The session menu shows detected sessions in the pcap file. This section provides information on;
- Frame number
- Client and server address
- Source and destination port
- Protocol
- Start time
You can search for keywords inside frames with the help of the filtering bar. It is possible to filter specific columns of the session menu as well. This menu accepts four types of inputs;
- "ExactPhrase"
- "AllWords"
- "AnyWord"
- "RegExe"
DNS
The DNS menu shows DNS queries with details. This section provides information on;
- Frame number
- Timestamp
- Client and server
- Source and destination port
- IP TTL
- DNS time
- Transaction ID and type
- DNS query and answer
- Alexa Top 1M
Some of the features (Alexa Top 1M) are available only in premium mode. The search bar is available here as well.
Credentials
The credentials menu shows extracted credentials and password hashes from investigated pcaps. You can use Hashcat(GitHub) and John the Ripper (GitHub) to decrypt extracted credentials. NetworkMiner can extract credentials including;
- Kerberos hashes
- NTLM hashes
- RDP cookies
- HTTP cookies
- HTTP requests
- IMAP
- FTP
- SMTP
- MS SQL
The right-click menu is helpful in this part as well. You can easily copy the username and password values.
Flag 1
Use mx-3.pcap
What is the total number of frames?
Once mx-3.pcap is loaded, navigate to the far right and right click on it, then select Metadata.
And the flag is retrieved like so.
Flag 2
How many IP addresses use the same MAC address with host 145.253.2.203?
Click on the + icon beside the IP to expand, and we see 2 MAC addresses with the same host.
Flag 3
How many packets were sent from host 65.208.228.223?
Expand the IP mentioned in the question.
Flag 4
What is the name of the webserver banner under host 65.208.228.223?
Expand on Host Details.
Flag 5
Use mx-4.pcap
What is the extracted username?
Once mx-4.pcap is loaded, navigate to Credentials tab and we can see the flag there.
Flag 6
What is the extracted password?
At the same spot as before, just extract the password. We can copy it by just right click on the row and select copy password.
Tool Overview 2
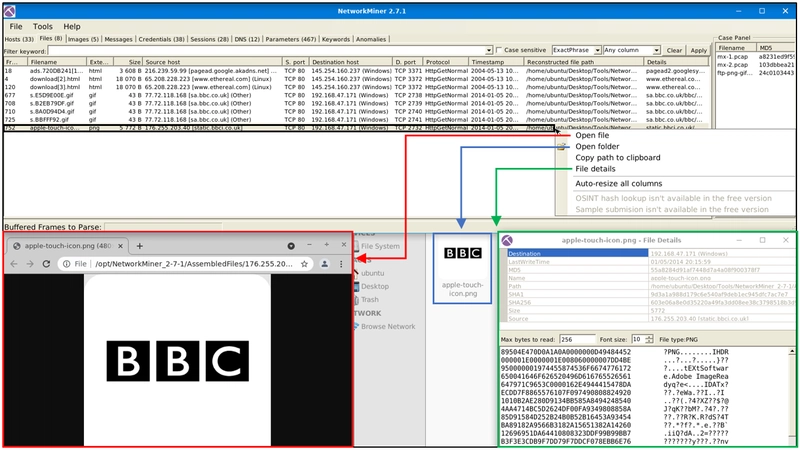
Files
The file menu shows extracted files from investigated pcaps. This section provides information on;
- Frame number
- Filename
- Extension
- Size
- Source and destination address
- Source and destination port
- Protocol
- Timestamp
- Reconstructed path
- Details
Some features (OSINT hash lookup and sample submission) are available only in premium mode. The search bar is available here as well. The right-click menu is helpful in this part as well. You can easily open files and folders and view the file details in-depth.
Images
The file menu shows extracted images from investigated pcaps. The right-click menu is helpful in this part as well. You can open files and zoom in & out easily.
Once you hover over the image, it shows the file's detailed information (source & destination address and file path).
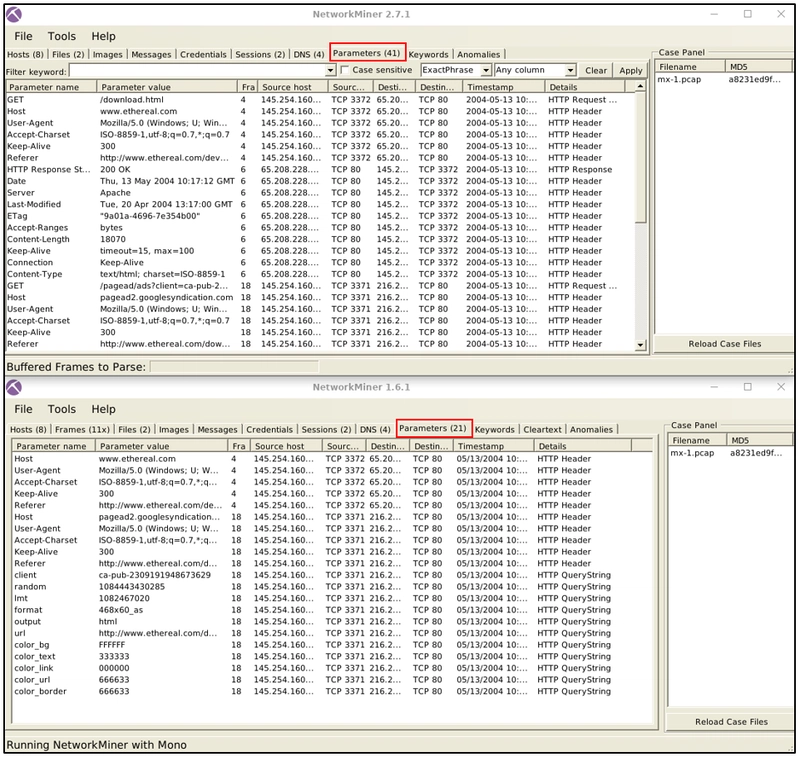
Parameters
The file menu shows extracted parameters from investigated pcaps. This section provides information on;
- Parameter name
- Parameter value
- Frame number
- Source and destination host
- Source and destination port
- Timestamp
- Details
The right-click menu is helpful in this part as well. You can copy the parameters and values easily.
Keywords
The file menu shows extracted keywords from investigated pcaps. This section provides information on;
- Frame number
- Timestamp
- Keyword
- Context
- Source and destination host
- source and destination port
How to filter keywords;
- Add keywords
- Reload case files!
**Note: **You can filter multiple keywords in this section; however, you must reload the case files after updating the search keywords. Keyword search investigates all possible data in the processed pcaps.
Messages
The messages menu shows extracted emails, chats and messages from investigated pcaps. This section provides information on;
- Frame number
- Source and destination host
- Protocol
- Sender (From)
- Receiver (To)
- Timestamp
- Size
Once you filter the traffic and get a hit, you will discover additional details like attachments and attributes on the selected message. Note that the search bar is available here as well. The right-click menu is available here. You can use the built-in viewer to investigate overall information and the "open file" option to explore attachments.
Anomalies
The anomalies menu shows detected anomalies in the processed pcap. Note that NetworkMiner isn't designated as an IDS. However, developers added some detections for EternalBlue exploit and spoofing attempts.
Flag 1
Use mx-7 pcap
What is the name of the Linux distro mentioned in the file associated with frame 63075?
Once mx-7.pcap is loaded, we navigate to Files and filter using 63075, which returns the Linux distro for us.
Flag 2
What is the header of the page associated with frame 75942?
Navigate to Files and search for the frame.
Double click on the matched result and the flag can be retrieved from there.
Flag 3
What is the source address of the image "ads.bmp.2E5F0FD9.bmp"?
Search for the image under the Files tab.
Flag 4
What is the frame number of the possible TLS anomaly?
Navigate to Anomalies tab.
Flag 5
Use mx-9 file
Look at the messages. Which platform sent a password reset email?
Navigate to Messages.
Flag 6
What is the email address of Branson Matheson?
We can see Branson's email while going through the rest of the messages.
Verson Differences
As always, it wouldn't be surprising to see a feature improvement as the version goes up. Unsurprisingly version upgrades provide stability, security fixes and features. Here the feature part is quite tricky. Feature upgrades can represent implementing new features and updating the existing feature (optimisation, alteration or operation mode modification). You can always check the changelog here.
Since there are some significant differences between the versions, the given VM has both of the major versions (v1.6 and v2.7).
Of course, as the program version increases, it is expected to increase feature increase and scope. Here are the significant differences between versions 1.6 and 2.7. Here are the differences;
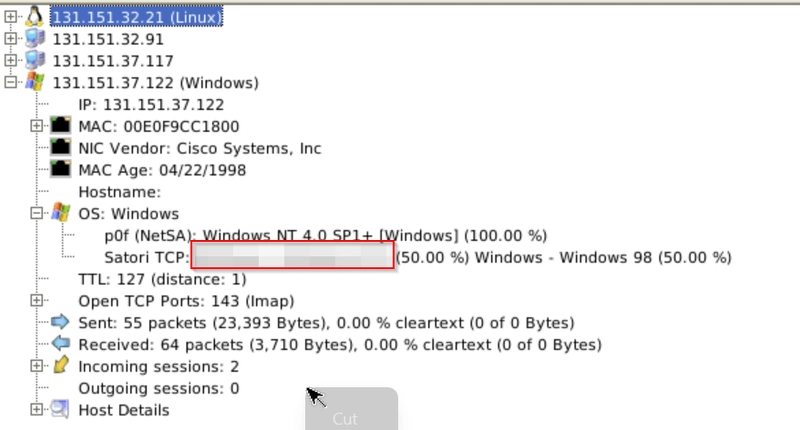
Mac Address Processing
NetworkMiner versions after version 2 can process MAC address specific correlation as shown in the picture below. This option will help you identify if there is a MAC Address conflict. This feature is not available before version 2.
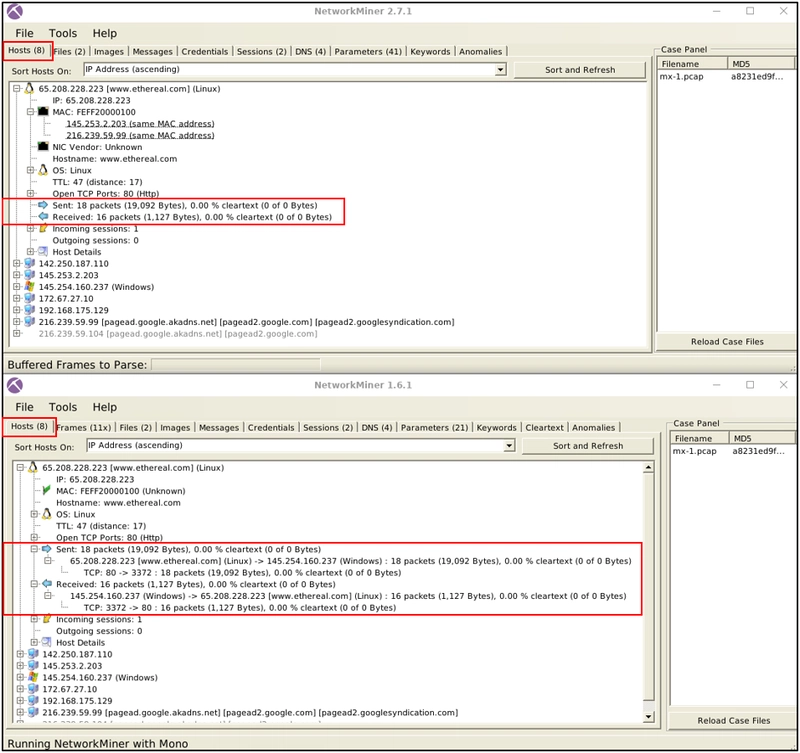
Sent/Received Packet Processing
NetwrokMiner versions up to version 1.6. can handle packets in much detail. These options will help you investigate the sent/received
packets in a more detailed format. This feature is not available after version 1.6.
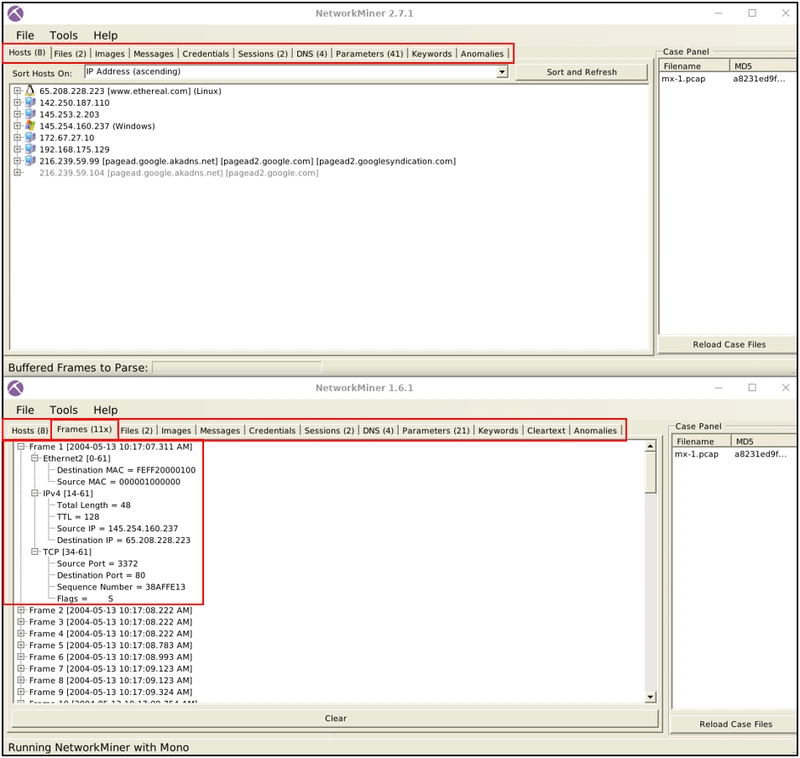
Frame Processing
NetworkMiner versions up to version 1.6. can handle frames. This option provides the number of frames and essential details about the frames. This feature is not available after version 1.6.
Parameter Processing
NetworkMiner versions after version 2 can handle parameters in a much more extensive form. Therefore version 1.6.xx catches fewer parameters than version 2.
Cleartext Processing
NetworkMiner versions up to version 1.6. can handle cleartext data. This option provides all extracted cleartext data in a single tab; it is beneficial to investigate cleartext data about the traffic data. However, it is impossible to match the cleartext data and packets. This feature is not available after version 1.6.
Flag 1
Which version can detect duplicate MAC addresses?
2.7
Flag 2
Which version can handle frames?
1.6
Flag 3
Which version can provide more details on packet details?
1.6
Exercises
Flag 1
Use case1.pcap
What is the OS name of the host 131.151.37.122?
Flag 2
Investigate the hosts 131.151.37.122 and 131.151.32.91.
How many data bytes were received from host 131.151.32.91 to host 131.151.37.122 through port 1065?
Flag 3
Investigate the hosts 131.151.37.122 and 131.151.32.21.
How many data bytes were received from host 131.151.37.122 to host 131.151.32.21 through port 143?
Flag 4
What is the sequence number of frame 9?
Load case1.pcap at NetworkMiner 1.6. Naviagte to Frames -> Frame 9 -> TCP
Flag 5
What is the number of the detected "content types"?
Navigating back tp NetworkMiner 2.7 -> Parameters and search content-type.
We only see 2 conten-type parameter values, being text/plain or multipart/mixed.
With this in mind, out flag is 2.
Flag 6
Use case2.pcap
Investigate the files.
What is the USB product's brand name?
Navigate to Files and search for usb.
Flag 7
What is the name of the phone model?
As we go through the images, we see Lumia, which is a phone naming convention for Nokia. Kind of like Galaxy to Samsung.
We just navigate to Files and search Lumia and retrieve the flag.
Flag 8
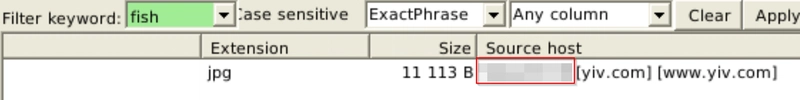
What is the source IP of the fish image?
Search fish under Files.
We then scroll to the right to reveal the IP.
Flag 9
What is the password of the "homer.pwned.se@gmx.com"?
We navigate to Credentials and the flag is there.
Flag 10
What is the DNS Query of frame 62001?
Go to DNS and search for 620001.
The flag can be retrieved when we scroll right until we see the DNS Query tab.







































































![Apple Reports Q2 FY25 Earnings: $95.4 Billion in Revenue, $24.8 Billion in Net Income [Chart]](https://www.iclarified.com/images/news/97188/97188/97188-640.jpg)












![Google reveals NotebookLM app for Android & iPhone, coming at I/O 2025 [Gallery]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/05/NotebookLM-Android-iPhone-6-cover.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)

























































































































































































































![[The AI Show Episode 145]: OpenAI Releases o3 and o4-mini, AI Is Causing “Quiet Layoffs,” Executive Order on Youth AI Education & GPT-4o’s Controversial Update](https://www.marketingaiinstitute.com/hubfs/ep%20145%20cover.png)


















































































































![[REPOST] Installing Genymotion for Android App Pentesting: The Definitive Guide](https://media2.dev.to/dynamic/image/width=800%2Cheight=%2Cfit=scale-down%2Cgravity=auto%2Cformat=auto/https%3A%2F%2Fdev-to-uploads.s3.amazonaws.com%2Fuploads%2Farticles%2F7zx2oyrfun6gecomzwf2.png)