5 Ways to Connect IOCs to Real-World Threats for SOC Teams
When it comes to cyber threats, data alone isn’t enough. Security Operations Center (SOC) teams are flooded with indicators of compromise (IOCs), but without context, these signals often fall short of driving meaningful action. Data only makes a difference when it’s connected to real-world events. When it tells a story, explains the what, and guides […] The post 5 Ways to Connect IOCs to Real-World Threats for SOC Teams appeared first on Cyber Security News.

When it comes to cyber threats, data alone isn’t enough. Security Operations Center (SOC) teams are flooded with indicators of compromise (IOCs), but without context, these signals often fall short of driving meaningful action.
Data only makes a difference when it’s connected to real-world events. When it tells a story, explains the what, and guides the how.
This is where threat intelligence plays a critical role.
By enriching IOCs with information about attacker behavior and tactics, threat intelligence transforms noise into insight.
How Threat Intelligence Lookup Helps Enrich Indicators
ANY.RUN’s Threat Intelligence Lookup facilitates tasks of this kind with proficiency backed by an impressive database of malware samples analyzed by a community of malware researchers all over the world including 15,000 SOC teams.
It supports about 40 search parameters to navigate samples, indicators, malicious processes, and adversary TTPs.
Let’s see how it bridges the gap between raw IOCs and real-world threats, empowering SOC teams to act faster and smarter.
1. Using Mutexes To Overcome Information Deficit
A mutex alone is rarely a definitive sign of a threat. It must be correlated with other IOCs (e.g., network activity, process behavior, file hashes) to confirm a malware presence.
But when data is scarce, a mutex becomes a first step into investigation.
For example, Nitrogen, a recently discovered ransomware targeting finance and other key industries, hasn’t yet been deeply researched by malware analysts.
An only detailed public report cites a very limited number of IOCs, including a mutex.
Used as a TI Lookup search request, the mutexe’s name allows us to find an assortment of public malware sample analyses performed in ANY.RUN’s Interactive Sandbox.
syncObjectName:”nvxkjcv7yxctvgsdfjhv6esdvsx”
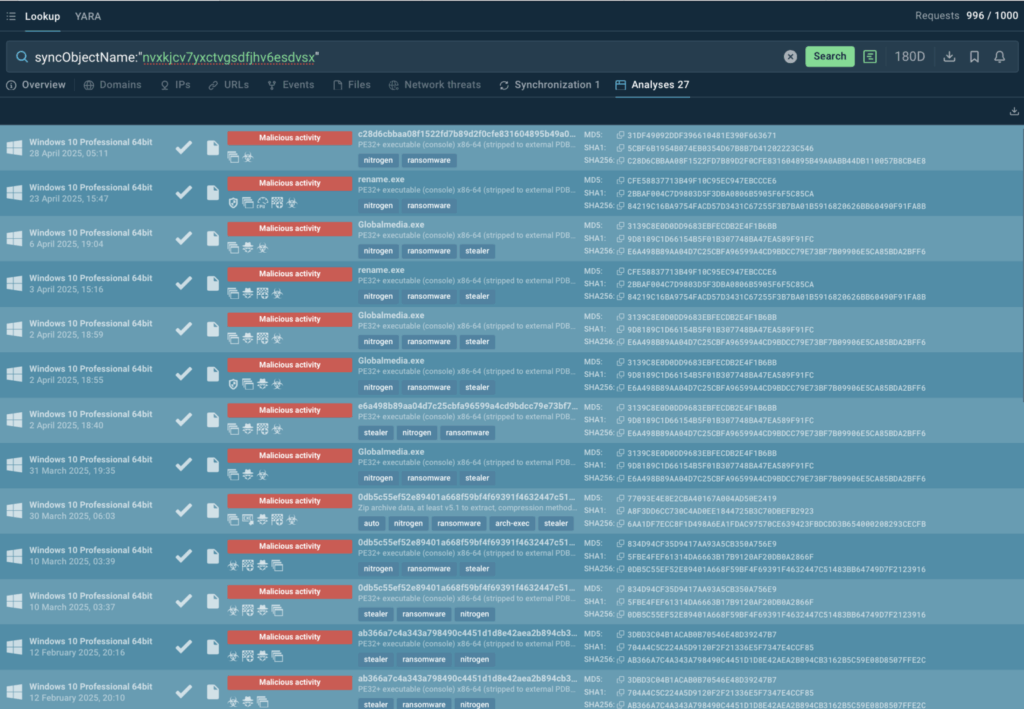
Each analysis can be explored in-depth to understand the new ransomware and gather IOCs for tuning EDR systems.
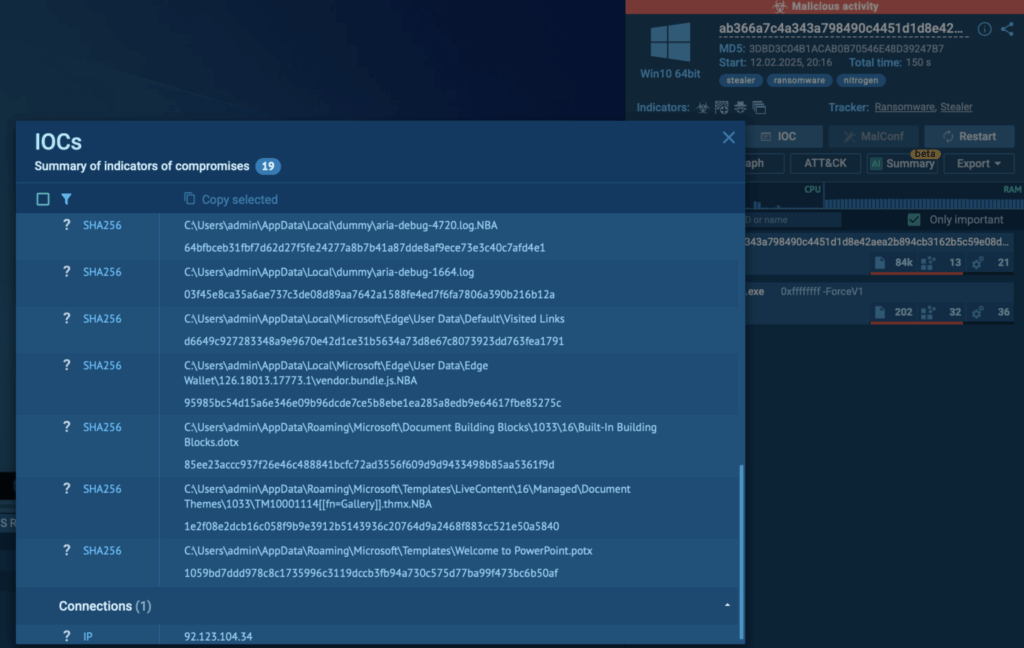
Use TI Lookup to enrich indicators with deep threat context to speed up triage and response -> Get a special offer for your team until May 31 → 2. Using Network Indicators To Pinpoint Malicious Activity
An easy way to uncover the menacing nature of a dubious domain spotted in the network is to submit it in TI Lookup.
Search results flag the domain as malicious and indicate it is part of the Lumma stealer infrastructure used for communications with the C2 server.
Besides, it is linked to fresh malware samples, and we know it has been involved in recent Lumma campaigns.
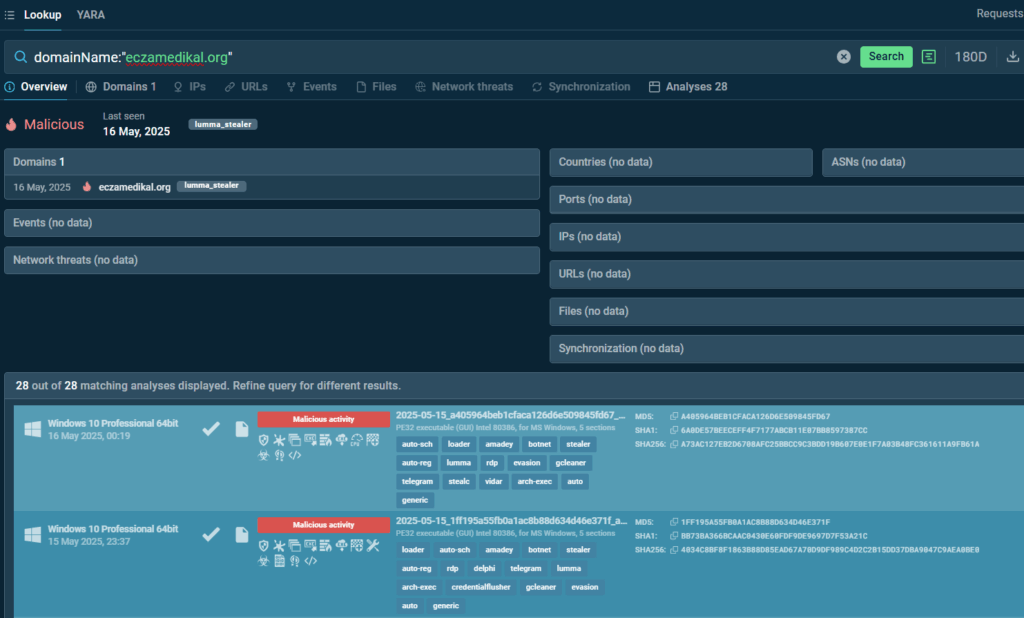
Public analyses of Lumma malware samples are also featured in the results allowing further IOC collection.
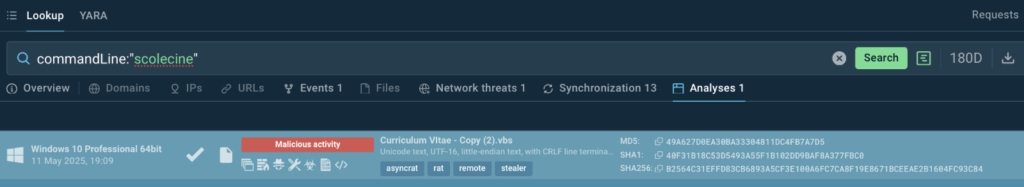
3. Tracing Command Line Back To Stealer Attack
An unfamiliar command string in the logs can point out an unnoticed threat.
We can search TI Lookup for a command run via PowerShell by a unique fragment and see how the malicious process including this command unfolded.
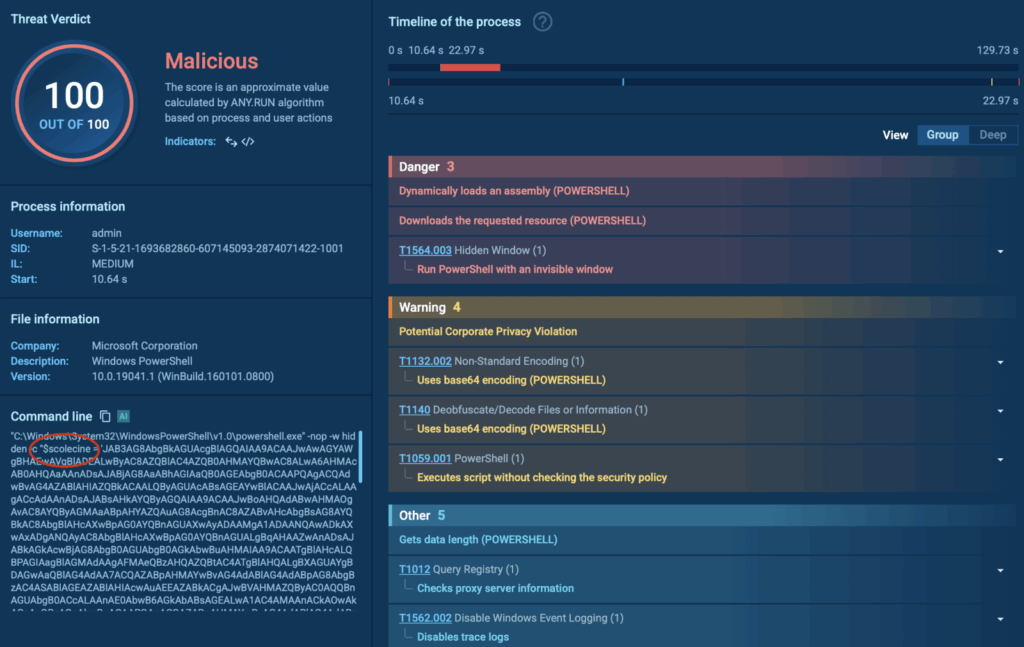
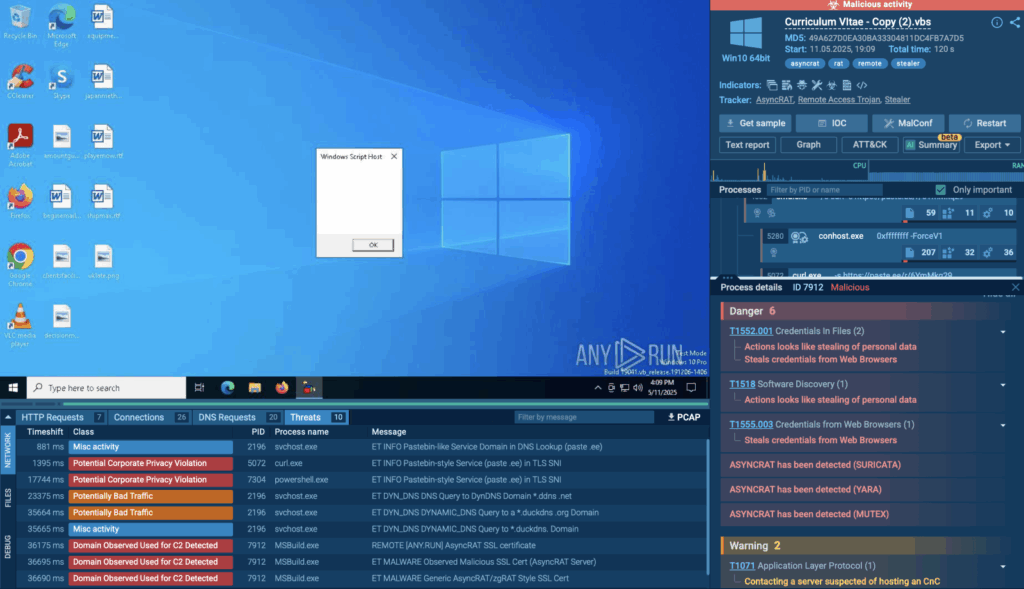
What is more important, Threat Intelligence Lookup provides the malware sample analysis which shows the whole kill chain and attack scenario and detects the notorious AsyncRat stealer as the vehicle of this attack.
This AsyncRat’s attack can be viewed in the Interactive Sandbox.
4. Checking File’s Threat Level By Hash
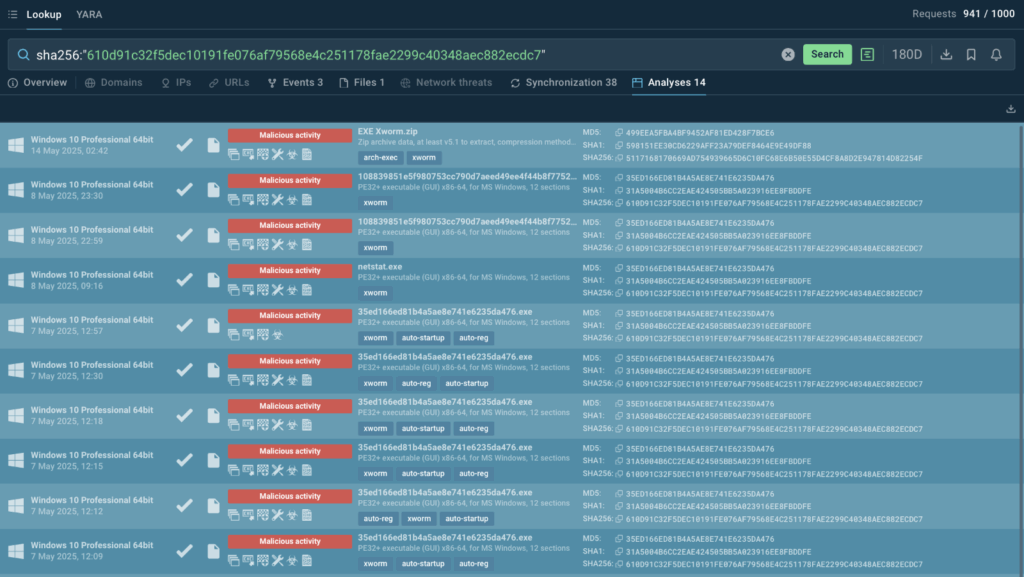
TI Lookup supports several hash type searches: sha256, sha1, md5. A file hash is a promising IOC that helps detect malware that utilizes a known malicious document in its campaigns.
In our case, a certain hash belongs to Xworm remote access trojan’s infrastructure.
5. Collecting Samples Belonging To The Same Campaign
Names of the files routinely employed in a certain malware campaign, unlike their hashes, can vary still identifying the same threat.
The support of wildcards like the asterisk (*) in TI Lookup enables the search by a part of a file’s name.
Such searches may help to gather more file names linked to the same campaign or malware strain and add to the IOCs collection.
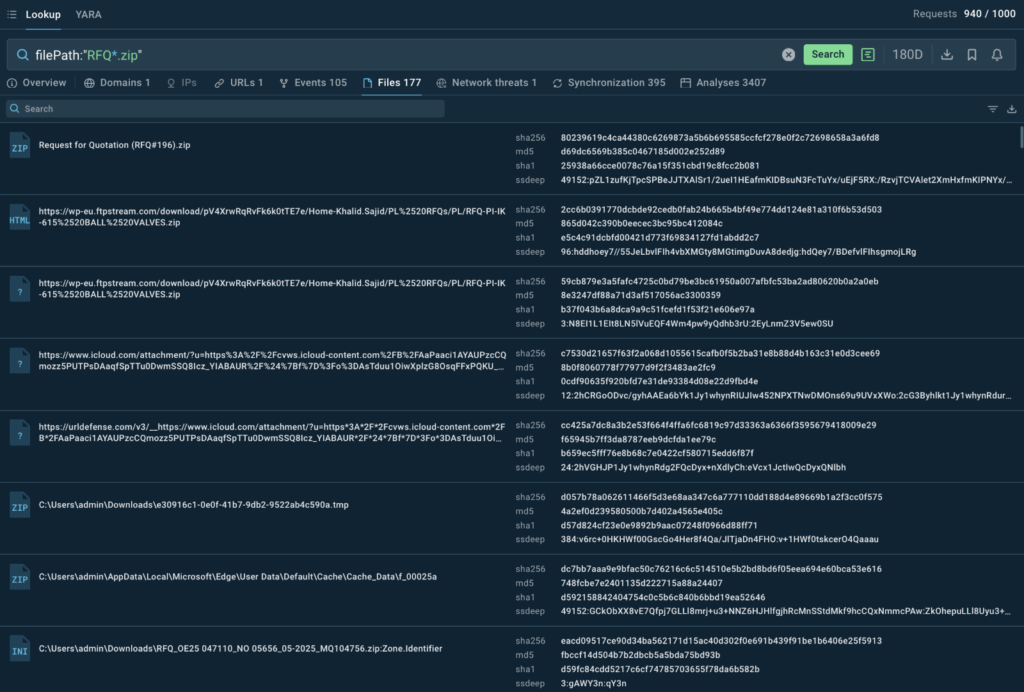
Proceeding to the “Analyses” tab in the search results, we instantly understand that the files belong to WannaCry attacks.
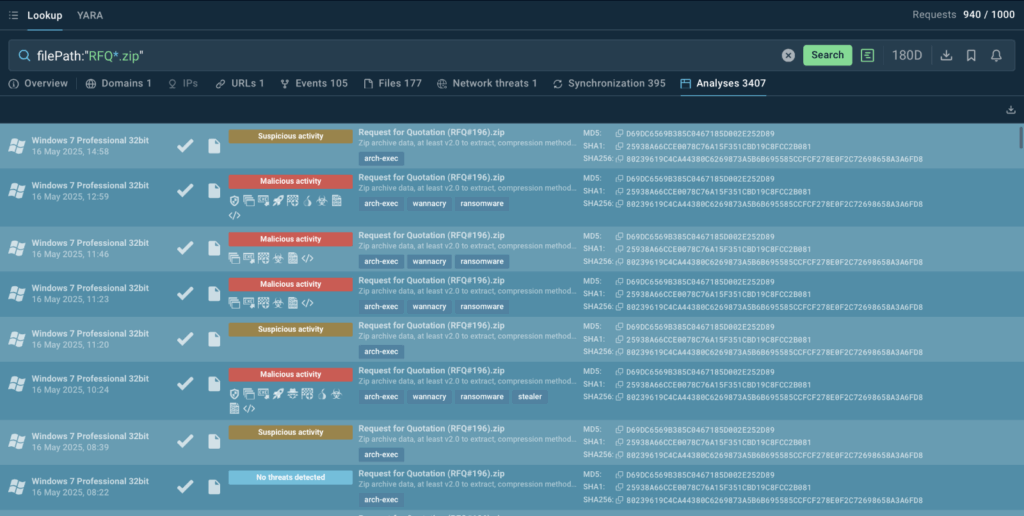
Get A Special TI Lookup Offer For Your Team Until May 31
TI Lookup streamlines your SOC teams’ workflow, letting analysts quickly connect indicators to threats, investigate incidents, and process alerts with confidence and speed.
The result is strong security for your company, proactive defense, and prevention of costly attacks: Take advantage of ANY.RUN’s Birthday offers.- TI Lookup: Get a plan with 100 more search requests and ANY.RUN will double your request quota for free.
- Interactive Sandbox: Grab extra licenses as a gift.
With additional search requests, your SOC team will triage more alerts, uncover more threats, and contain more incidents.
Conclusion
Connecting IOCs to real-world threats isn’t just about improving detection or response— it’s about aligning security efforts with business objectives.
When SOC teams understand the why behind the data, they can prioritize threats that matter most to the organization.
TI Lookup enables this prioritization, helping teams filter out irrelevant signals and focus on high-impact threats.
Context-driven intelligence helps allocate resources effectively, protect critical assets, and communicate risk in terms the business understands.
By turning isolated indicators into actionable intelligence, security leaders can ensure their operations are not only reactive, but strategically driven.
The post 5 Ways to Connect IOCs to Real-World Threats for SOC Teams appeared first on Cyber Security News.

_Prostock-studio_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)



















































































![What’s new in Android’s May 2025 Google System Updates [U: 5/19]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/01/google-play-services-1.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)






















































































.webp?#)






















































































































![[The AI Show Episode 147]: OpenAI Abandons For-Profit Plan, AI College Cheating Epidemic, Apple Says AI Will Replace Search Engines & HubSpot’s AI-First Scorecard](https://www.marketingaiinstitute.com/hubfs/ep%20147%20cover.png)





























































































































































![How to make Developer Friends When You Don't Live in Silicon Valley, with Iraqi Engineer Code;Life [Podcast #172]](https://cdn.hashnode.com/res/hashnode/image/upload/v1747360508340/f07040cd-3eeb-443c-b4fb-370f6a4a14da.png?#)
































































































