VMware ESXi & vCenter Vulnerability Let Attackers Run Arbitrary Commands
Broadcom’s VMware division has disclosed critical security vulnerabilities in its virtualization products, including a high-severity flaw that could allow authenticated users to execute arbitrary commands on affected systems. Today’s security advisory addresses four distinct vulnerabilities affecting multiple VMware products with severity ratings ranging from Moderate to Important. Critical Command Execution Vulnerability The most severe vulnerability, […] The post VMware ESXi & vCenter Vulnerability Let Attackers Run Arbitrary Commands appeared first on Cyber Security News.

Broadcom’s VMware division has disclosed critical security vulnerabilities in its virtualization products, including a high-severity flaw that could allow authenticated users to execute arbitrary commands on affected systems.
Today’s security advisory addresses four distinct vulnerabilities affecting multiple VMware products with severity ratings ranging from Moderate to Important.
Critical Command Execution Vulnerability
The most severe vulnerability, CVE-2025-41225, affects VMware vCenter Server and carries a CVSS score of 8.8. This authenticated command-execution vulnerability allows malicious actors with privileges to create or modify alarms and run script actions to execute arbitrary commands on the vCenter Server.
Security experts consider this vulnerability particularly dangerous as it provides attackers with a direct path to compromise core virtualization management infrastructure.
“This vulnerability represents a significant risk to enterprise environments where vCenter Server manages critical workloads,” said a spokesperson from the VMware security team. “Organizations should prioritize patching immediately to prevent potential exploitation.”
Other Vulnerabilities Patched
The advisory also addresses three other security flaws:
- CVE-2025-41226: A denial-of-service vulnerability in ESXi when performing guest operations (CVSS score of 6.8). This vulnerability allows attackers with guest operating privileges to create denial-of-service conditions affecting virtual machines running VMware Tools.
- CVE-2025-41227: A denial-of-service vulnerability in Workstation, Fusion, and ESXi due to certain guest options (CVSS score of 5.5). Non-administrative users within a guest operating system can exploit this issue by exhausting memory resources of the host process.
- CVE-2025-41228: A reflected cross-site scripting vulnerability in ESXi and vCenter Server login pages (CVSS score of 4.3). Attackers with network access to specific URL paths can exploit this issue to steal cookies or redirect users to malicious websites.
The vulnerabilities impact a wide range of VMware products, including ESXi 7.0 and 8.0, vCenter Server 7.0 and 8.0, and Workstation 17.x, Fusion 13.x, VMware Cloud Foundation, Telco Cloud Platform, and Telco Cloud Infrastructure.
VMware has released updates to address these vulnerabilities. For vCenter Server, users should update to version 8.0 U3e or 7.0 U3v, depending on their current version.
ESXi customers should apply patches ESXi80U3se-24659227 (for version 8.0) or ESXi70U3sv-24723868 (for version 7.0). VMware Workstation and Fusion users should update to versions 17.6.3 and 13.6.3, respectively.
This advisory comes amid increasing attention on VMware product security. Earlier this month, Broadcom addressed three other significant vulnerabilities in the VMware Cloud Foundation platform that allowed attackers to gain unauthorized access to sensitive information and internal services.
In March, Broadcom issued an advisory addressing three critical exploited vulnerabilities in VMware ESXi that, when chained together, allowed attackers to access hypervisors by running virtual machines.
All organizations running affected VMware products should implement the provided patches immediately, as no workarounds are available for these vulnerabilities.
Given VMware’s dominant position in enterprise virtualization, these vulnerabilities represent significant risks to organizational security postures.
Equip your SOC team with deep threat analysis for faster response -> Get Extra Sandbox Licenses for Free
The post VMware ESXi & vCenter Vulnerability Let Attackers Run Arbitrary Commands appeared first on Cyber Security News.

_Prostock-studio_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)



















































































![What’s new in Android’s May 2025 Google System Updates [U: 5/19]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/01/google-play-services-1.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)




































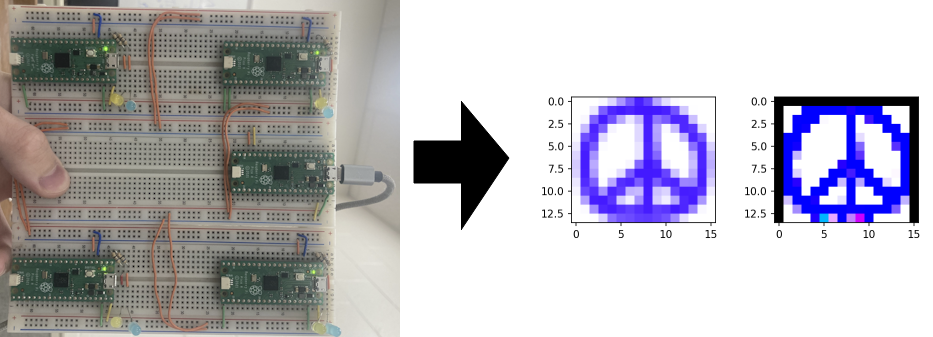


















































.webp?#)






















































































































![[The AI Show Episode 147]: OpenAI Abandons For-Profit Plan, AI College Cheating Epidemic, Apple Says AI Will Replace Search Engines & HubSpot’s AI-First Scorecard](https://www.marketingaiinstitute.com/hubfs/ep%20147%20cover.png)





























































































































































![How to make Developer Friends When You Don't Live in Silicon Valley, with Iraqi Engineer Code;Life [Podcast #172]](https://cdn.hashnode.com/res/hashnode/image/upload/v1747360508340/f07040cd-3eeb-443c-b4fb-370f6a4a14da.png?#)































































































