This site uses cookies. By continuing to browse the site you are agreeing to our use of cookies.
From Data to Dollars: Startup Growth Through ...
Jun 5, 2025 0
ISO Certification in India: Secure Your Compe...
Jun 4, 2025 0
Making Sense of Cybersecurity – Part 1: Seein...
May 12, 2025 0
Making Sense of Cybersecurity – Part 2: Deliv...
May 12, 2025 0
Why a SaaS Needs an Artificial Intelligence D...
Jun 13, 2025 0
Recipes
May 12, 2025 0
Miscellaneous Links #46
May 12, 2025 0
Eating Bugs
May 12, 2025 0
Miscellaneous Links #47
May 12, 2025 0
IEEE Transactions on Cognitive and Developmen...
Jun 13, 2025 0
IEEE Transactions on Fuzzy Systems, Volume 33...
Jun 13, 2025 0
Soft Computing, Volume 29, Issue 7, April 2025
Jun 11, 2025 0
IEEE Transactions on Evolutionary Computation...
Jun 10, 2025 0
How to Onboard an Artificial Intelligence Dev...
Jun 12, 2025 0
Guide to Setting Up a Business Bank Account i...
May 16, 2025 0
Unlocking Financial Freedom Early: How Young ...
May 13, 2025 0
young adults are investing
May 12, 2025 0
How to Hire a Data Scientist: A 2025 Guide fo...
Jun 4, 2025 0
How Do LLMs Think? 5 Approaches Powering the ...
May 12, 2025 0
Why a SaaS Needs an Artificial Intelligence D...
Jun 13, 2025 0
Top Portfolios from Artificial Intelligence D...
Jun 11, 2025 0
Artificial Intelligence Developer Salary Tren...
Jun 10, 2025 0
10 Must-Ask Questions For Every Artificial In...
Jun 9, 2025 0
Real-life transformer: Drone morphs mid-air
Jun 11, 2025 0
Selena Gomez Net Worth: Discover Her Financia...
Jun 3, 2025 0
Why Businesses Should Hire Data Scientists to...
Jun 2, 2025 0
Affiliate Marketing Strategies: How to Genera...
May 17, 2025 0
Cassandra + ElasticSearch VS PostgreSQL or My...
Jun 13, 2025 0
What is a suitable format for writing large a...
Jun 13, 2025 0
Clarification on MCP: Message Format vs. Comm...
Jun 12, 2025 0
Production postmorterm: The rookie server's u...
Jun 12, 2025 0
fsync()-ing a directory on Linux (and not Win...
Jun 10, 2025 0
Understanding Rule 11A: The Unsung Hero of Pr...
Jun 11, 2025 0
A67VIP: The Ultimate Gateway to Online Gaming...
Jun 12, 2025 0
- Home
- LIVE TV
-
Technology
- All
- techcrunch.com
- apple.com
- CMSWire
- torrentfreak.com
- phonearena.com
- gizchina.com
- macrumors.com
- omgubuntu.co.uk
- officialandroid.blogspot.com
- androidheadlines.com
- talkandroid.com
- droid-life.com
- ghacks.net
- techradar.com
- phandroid.com
- fossmint.com
- web.dev
- malwarebytes.com
- iclarified.com
- theregister.com
- theverge.com
- thenextweb.com
- 9to5google.com
- 9to5mac.com
- androidauthority.com
- androidcentral.com
- appleinsider.com
- arstechnica.com
- bgr.com
- digitaltrends.com
- extremetech.com
- gizmodo.com
- gsmarena.com
- hackaday.com
- makezine.com
- pcworld.com
- slashdot.org
- slashgear.com
- techmeme.com
- technologyreview.com
- gigaom.com
- zdnet.com
- anandtech.com
- dailyai.com
- enterpriseai.news
- machinelearningmastery.com
- marktechpost.com
- towardsdatascience.com
- venturebeat.com
- cybersecuritynews.com
- darkreading.com
- krebsonsecurity.com
- 9to5linux.com
- linux-magazine.com
-
AI
- All
- The Next Web
- Dale on AI
- Datumbox
- Find New AI
- Chatbots Magazine
- Microsoft AI Blog
- Appzoon Blog
- Bigly Sales Blog
- Top Marketing AI
- Great Learning AI
- Vue.ai Blog
- Data Machina
- Cogito Tech Blog
- MetaDevo
- AI Plus Info Blog
- Computational Intelligence
- USM Systems
- TechSpective AI
- AI Hub Blog
- Marek Rosa's Blog
- Robot Writers AI
- Viact.ai
- 1RedDrop
- DeepCognition
- Machine Intelligence Research Institute
- AI Weekly Blog
- Fusemachines Insights Blog
- AI Time Journal
- DLabs AI
- Artificial Lawyer
- TOPBOTS
- Marketing AI Institute
- Chatbots Life
- Isentia
- AI Summer
- Expert System
- Clarifai
- Kore.ai
- Big Data Analytics
- Becoming Human
- DataRobot
- Nanonets Blog
- AIMultiple Research
- KDnuggets
- MIT Technology Review
- RStudio AI
- SAS Blog
- O'Reilly Radar
- Qudata
- WGMimedia
- SI Corr
- Saal AI Insights
- AI Revolution
- Shaip Blog
- Yatter Blog
- The Spritle
- AI Tool Nyheter
- Daily AI
- AIParabellum
- Hanh Brown
- AI2People
- AI News Blog
- Unite AI
- DeepMind
- BAIR Blog
- MarkTechPost
- Machine Learning Mastery
-
Programming
- All
- blog.google
- stackoverflow.blog
- developers.googleblog.com
- engineering.atspotify.com
- engineering.fb.com
- github.blog
- softwareengineering
- 8thlight.com
- AyendeRahien
- blog.jetbrains.com
- changelog.com
- code.tutsplus.com
- davidwalsh.name
- dev.to
- freecodecamp.org
- herbsutter.com
- javacodegeeks.com
- javascriptweekly.com
- johnpapa.net
- martinfowler.com
- nodejs.org
- blog.ploeh.dk
- linuxjournal.com
- devblogs.microsoft.com
-
Gaming
- All
- blog.humblebundle.com
- blog.playstation.com
- engadget.com
- eurogamer.net
- gamesindustry.biz
- gamespot.com
- giantbomb.com
- gog.com
- indiegamesplus.com
- kotaku.com
- mynintendonews.com
- news.xbox.com
- nintendolife.com
- pcgamesn.com
- playstationlifestyle.net
- pocketgamer.com
- pockettactics.com
- rockpapershotgun.com
- siliconera.com
- steampowered.com
- toucharcade.com
- vg247.com
- Add your feed
- News Feed




































































![Apple Shares Teaser Trailer for 'The Lost Bus' Starring Matthew McConaughey [Video]](https://www.iclarified.com/images/news/97582/97582/97582-640.jpg)


























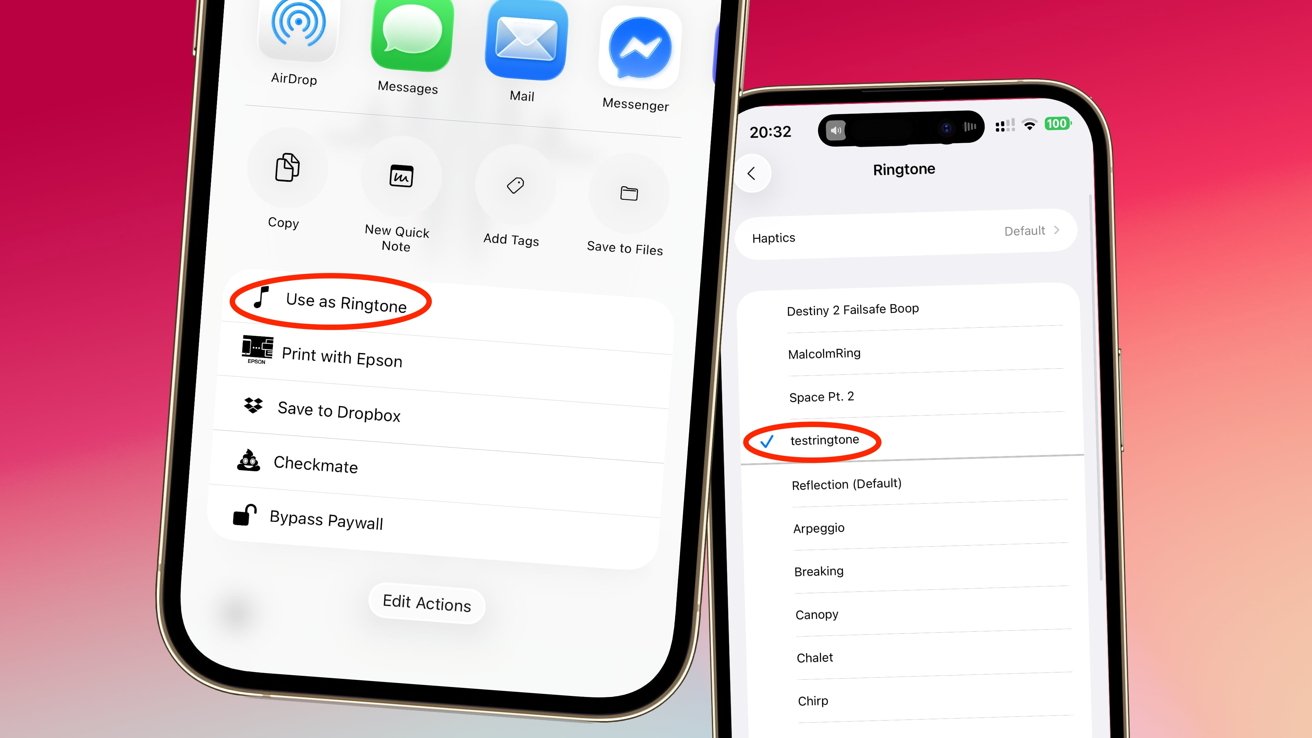




















































































_Marek_Uliasz_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)























































































![Top Features of Vision-Based Workplace Safety Tools [2025]](https://static.wixstatic.com/media/379e66_7e75a4bcefe14e4fbc100abdff83bed3~mv2.jpg/v1/fit/w_1000,h_884,al_c,q_80/file.png?#)



























![[The AI Show Episode 152]: ChatGPT Connectors, AI-Human Relationships, New AI Job Data, OpenAI Court-Ordered to Keep ChatGPT Logs & WPP’s Large Marketing Model](https://www.marketingaiinstitute.com/hubfs/ep%20152%20cover.png)


































































































![[DEALS] Microsoft Visual Studio Professional 2022 + The Premium Learn to Code Certification Bundle (97% off) & Other Deals Up To 98% Off](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)
































































.jpg?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)






-35-45-screenshot.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)

-30-7-screenshot_0FxoE4J.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)
































































_incamerastock_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)








_sleepyfellow_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)

