The Linux (rm) Command: Simple, Powerful, and Dangerous
There’s a reason that Linux professionals emphasize caution when using the rm command. It’s a very simple command, only two letters, but extremely powerful. If you’re not careful, a misplaced command could wipe out critical files or even an entire system. I want to share what I’ve learned about the rm command, from the basics to best practices, because understanding this command well can save you a lot of trouble down the road. Index 1. What is the rm Command? 2. Common rm Options 3. The Dangers of the rm command 4. Best Practices for Using rm 5. Recommendations for Safe Use 6. Business Use Cases 7. Summary 1. What is the rm Command? The rm command stands for "remove." It’s used to delete files and directories in Linux. It’s a pretty straightforward command, but its power lies in the options you can use to make it more flexible. Basic Syntax rm filename.txt - This removes a specified file from your system. For example, rm filetest2.txt will delete filetest2.txt. 2. Common rm Options Here are some of the most commonly used (and most important!) options for rm: -r: Recursively delete directories and their contents. -f: Force removal without prompting for confirmation. -i: Interactive mode, asking for confirmation before every deletion (highly recommended). Example: rm -ri foldername - This will prompt you for confirmation before removing the folder and its contents. For example, rm finance will delete the finance directory. rm -rvf foldername - Recursive + Force: removes everything without asking. For example, rm -rvf inventory deletes the directory with contents without asking. Why it Matters The -r option is necessary when you need to delete directories, but combining it with -f can be risky. Always double-check your command when using these flags to avoid accidental deletions. 3. The Dangers of the rm Command Here’s where things can go wrong: Running rm * in the wrong folder can wipe out everything in that directory. Using rm -rf / can (and will!) delete your entire root filesystem. That means that the server will become inoperable, and if no backup, could be down for hours or even days. The thing to understand about the rm command is that there is no undo. Once the files are removed, they’re gone. 4. Best Practices for Using rm Always double-check your commands. Pay close attention to the paths and options you’re using. Use the -i option. This interactive flag makes rm a lot safer by prompting you before each deletion. Run a search first before deleting. If you’re using rm with search commands (like find), run the search alone first to verify what will be deleted. Example Workflow: Say you want to delete all files modified on a specific date (April 29, 2025), excluding hidden files and folders. Here’s the process: Step 1 - Search: find . -not -path '/.' -newermt "2025-04-29" ! -newermt "2025-04-30" What It Does: Searches the current directory (.). Excludes hidden files and directories (-not -path '*/.*'). Finds files modified on April 29, 2025 (-newermt flags). Step 2 - Delete (only after verifying the search): find . -not -path '/.' -newermt "2025-04-29" ! -newermt "2025-04-30" -exec rm -rf {} + What It Does: Adds -exec rm -rf to delete the matched files and directories. 5. Recommendations for Safe Use Using rm responsibly requires a little extra effort, but it’s worth it: Never combine search and delete in one step without testing. Run the search first, and only add the delete command once you’re confident. Communicate with your team. Before deleting anything in a shared environment, confirm with your team or a senior engineer. Backup first. Whether it’s a snapshot, copy, or full backup, always have a fallback in case something goes wrong. Document your actions. Log the commands you run and why, especially in production environments. Accountability is key. 6. Business Use Cases Log rotation - Remove old logs from servers to free disk space. Data retention compliance - Securely remove expired customer data after retention. Security - Delete sensitive files from servers during incident response. 7. Summary The rm command is one of the most useful tools in Linux, but it’s also one of the most dangerous. By taking the time to understand how it works and following best practices, you can avoid costly mistakes and handle deletions with confidence. Remember: double-check, backup, and think twice before you delete especially in a production environment. Using the rm command responsibly is what makes a great cloud engineer stand out. It’s all about being careful and understanding the command. Connect with me on LinkedIn to comment or share your experiences with Linux. #30DaysLinuxChallenge #RedHatEnterpriseLinux #CloudWhistler #CloudEngineer #Linux #DevOps #RedHat #OpenSource #CloudComputing #WomenInTech
There’s a reason that Linux professionals emphasize caution when using the rm command. It’s a very simple command, only two letters, but extremely powerful. If you’re not careful, a misplaced command could wipe out critical files or even an entire system. I want to share what I’ve learned about the rm command, from the basics to best practices, because understanding this command well can save you a lot of trouble down the road.
Index
1. What is the rm Command?
2. Common rm Options
3. The Dangers of the rm command
4. Best Practices for Using rm
5. Recommendations for Safe Use
6. Business Use Cases
7. Summary
1. What is the rm Command?
The rm command stands for "remove." It’s used to delete files and directories in Linux. It’s a pretty straightforward command, but its power lies in the options you can use to make it more flexible.
Basic Syntax
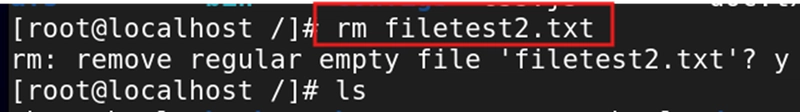
rm filename.txt - This removes a specified file from your system. For example, rm filetest2.txt will delete filetest2.txt.
2. Common rm Options
Here are some of the most commonly used (and most important!) options for rm:
-
-r: Recursively delete directories and their contents. -
-f: Force removal without prompting for confirmation. -
-i: Interactive mode, asking for confirmation before every deletion (highly recommended).
Example:
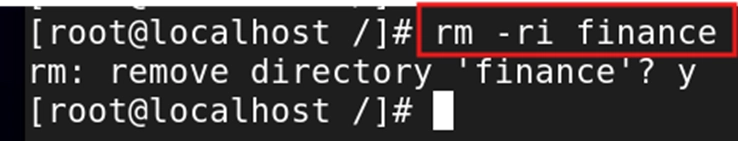
rm -ri foldername - This will prompt you for confirmation before removing the folder and its contents. For example, rm finance will delete the finance directory.
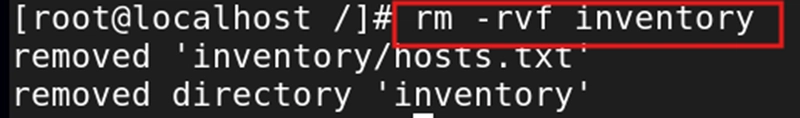
rm -rvf foldername - Recursive + Force: removes everything without asking. For example, rm -rvf inventory deletes the directory with contents without asking.
Why it Matters
The -r option is necessary when you need to delete directories, but combining it with -f can be risky. Always double-check your command when using these flags to avoid accidental deletions.
3. The Dangers of the rm Command
Here’s where things can go wrong:
- Running
rm *in the wrong folder can wipe out everything in that directory. - Using
rm -rf /can (and will!) delete your entire root filesystem. That means that the server will become inoperable, and if no backup, could be down for hours or even days. The thing to understand about the rm command is that there is no undo. Once the files are removed, they’re gone.
4. Best Practices for Using rm
- Always double-check your commands. Pay close attention to the paths and options you’re using.
-
Use the
-ioption. This interactive flag makesrma lot safer by prompting you before each deletion. -
Run a search first before deleting. If you’re using
rmwith search commands (likefind), run the search alone first to verify what will be deleted.
Example Workflow:
Say you want to delete all files modified on a specific date (April 29, 2025), excluding hidden files and folders. Here’s the process:
Step 1 - Search:
find . -not -path '/.' -newermt "2025-04-29" ! -newermt "2025-04-30"
What It Does:
- Searches the current directory (
.). - Excludes hidden files and directories (
-not -path '*/.*'). - Finds files modified on April 29, 2025 (
-newermtflags).
Step 2 - Delete (only after verifying the search):
find . -not -path '/.' -newermt "2025-04-29" ! -newermt "2025-04-30" -exec rm -rf {} +
What It Does:
- Adds
-exec rm -rfto delete the matched files and directories.
5. Recommendations for Safe Use
Using rm responsibly requires a little extra effort, but it’s worth it:
- Never combine search and delete in one step without testing. Run the search first, and only add the delete command once you’re confident.
- Communicate with your team. Before deleting anything in a shared environment, confirm with your team or a senior engineer.
- Backup first. Whether it’s a snapshot, copy, or full backup, always have a fallback in case something goes wrong.
- Document your actions. Log the commands you run and why, especially in production environments. Accountability is key.
6. Business Use Cases
- Log rotation - Remove old logs from servers to free disk space.
- Data retention compliance - Securely remove expired customer data after retention.
- Security - Delete sensitive files from servers during incident response.
7. Summary
The rm command is one of the most useful tools in Linux, but it’s also one of the most dangerous. By taking the time to understand how it works and following best practices, you can avoid costly mistakes and handle deletions with confidence. Remember: double-check, backup, and think twice before you delete especially in a production environment.
Using the rm command responsibly is what makes a great cloud engineer stand out. It’s all about being careful and understanding the command.
Connect with me on LinkedIn to comment or share your experiences with Linux.
#30DaysLinuxChallenge #RedHatEnterpriseLinux
#CloudWhistler #CloudEngineer #Linux
#DevOps #RedHat #OpenSource
#CloudComputing #WomenInTech





































































![New Beats USB-C Charging Cables Now Available on Amazon [Video]](https://www.iclarified.com/images/news/97060/97060/97060-640.jpg)
![Apple M4 13-inch iPad Pro On Sale for $200 Off [Deal]](https://www.iclarified.com/images/news/97056/97056/97056-640.jpg)































































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)






























































































































































.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)