Bybit Hack – Sophisticated Multi-Stage Attack Details Revealed
Cryptocurrency exchange Bybit detected unauthorized activity involving its Ethereum cold wallets, leading to a major security breach. The incident occurred during an ETH multisig transaction facilitated through Safe{Wallet}, when attackers intervened and manipulated the transaction, ultimately siphoning over 400,000 ETH from the exchange’s cold storage. The attack demonstrated unprecedented sophistication across multiple security domains, including […] The post Bybit Hack – Sophisticated Multi-Stage Attack Details Revealed appeared first on Cyber Security News.

Cryptocurrency exchange Bybit detected unauthorized activity involving its Ethereum cold wallets, leading to a major security breach.
The incident occurred during an ETH multisig transaction facilitated through Safe{Wallet}, when attackers intervened and manipulated the transaction, ultimately siphoning over 400,000 ETH from the exchange’s cold storage.
The attack demonstrated unprecedented sophistication across multiple security domains, including macOS malware deployment, AWS cloud infrastructure compromise, and smart contract manipulation.
The FBI has attributed the attack to ‘TradeTraitor’, also known as the Lazarus group, a threat actor linked to North Korea and responsible for numerous previous cryptocurrency heists.
Sygnia researchers identified that the earliest malicious activity began on February 4, 2025, when a Safe{Wallet} developer’s macOS workstation was compromised through social engineering.
The developer downloaded a suspicious Docker project named “MC-Based-Stock-Invest-Simulator-main” that initiated communications with a malicious domain.
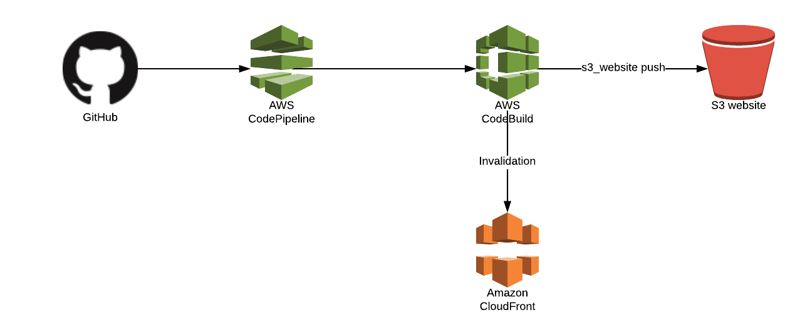
Between February 5 and February 17, the attackers operated within Safe{Wallet}’s AWS infrastructure after stealing AWS credentials from the compromised developer workstation.
The attackers leveraged ExpressVPN IP addresses and aligned their activity with the developer’s working hours to avoid detection.
On February 19, the attackers modified JavaScript resources hosted on Safe{Wallet}’s AWS S3 bucket.
.webp)
These modifications injected malicious code designed to manipulate transactions specifically from Bybit’s cold wallet address.
Technical Execution
The technical execution involved replacing legitimate transaction payloads with delegate calls to a pre-deployed malicious smart contract.
This delegate call mechanism allowed the attackers to replace the wallet’s implementation with a malicious version containing “sweepETH” and “sweepERC20” functions.
These functions enabled the transfer of funds without requiring the standard multisig approval process.
The malicious code contained an activation condition targeting specific contract addresses, along with transaction validation tampering designed to bypass security checks.
.webp)
Anchain’s reverse engineering of the exploit bytecode revealed four malicious smart contract functions implemented by the attackers.
Just two minutes after executing the heist, the attackers removed the malicious JavaScript code from Safe{Wallet}’s web interface, attempting to cover their tracks.
The Bybit case has set a new benchmark for forensic transparency, as the detailed disclosure of the investigation findings allows the industry to develop more effective defenses against similar attacks in the future.
Are you from SOC/DFIR Teams? – Analyse Malware Incidents & get live Access with ANY.RUN -> Start Now for Free.
The post Bybit Hack – Sophisticated Multi-Stage Attack Details Revealed appeared first on Cyber Security News.





























































![Apple C1 vs Qualcomm Modem Performance [Speedtest]](https://www.iclarified.com/images/news/96767/96767/96767-640.jpg)
![Apple Studio Display On Sale for $1249 [Lowest Price Ever]](https://www.iclarified.com/images/news/96770/96770/96770-640.jpg)












![[Fixed] Chromecast (2nd gen) and Audio can’t Cast in ‘Untrusted’ outage](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2019/08/chromecast_audio_1.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)


























































































































































![[The AI Show Episode 139]: The Government Knows AGI Is Coming, Superintelligence Strategy, OpenAI’s $20,000 Per Month Agents & Top 100 Gen AI Apps](https://www.marketingaiinstitute.com/hubfs/ep%20139%20cover-2.png)


![[The AI Show Episode 138]: Introducing GPT-4.5, Claude 3.7 Sonnet, Alexa+, Deep Research Now in ChatGPT Plus & How AI Is Disrupting Writing](https://www.marketingaiinstitute.com/hubfs/ep%20138%20cover.png)