Chip Glitching 101 with [Hash]
Ever want to get into reverse engineering but don’t know where to start? You’re in luck — [Hash] just dropped a case study in chip glitching that should get you …read more
![Chip Glitching 101 with [Hash]](https://hackaday.com/wp-content/uploads/2025/03/glitching.jpeg?#)
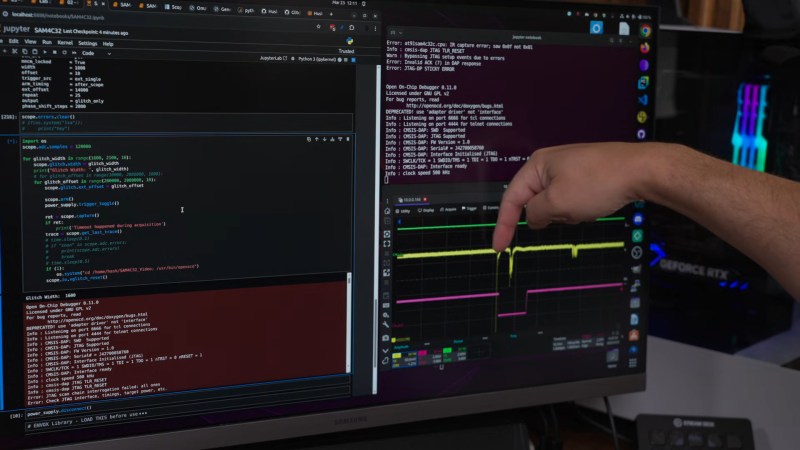
Ever want to get into reverse engineering but don’t know where to start? You’re in luck — [Hash] just dropped a case study in chip glitching that should get you off on the right foot.
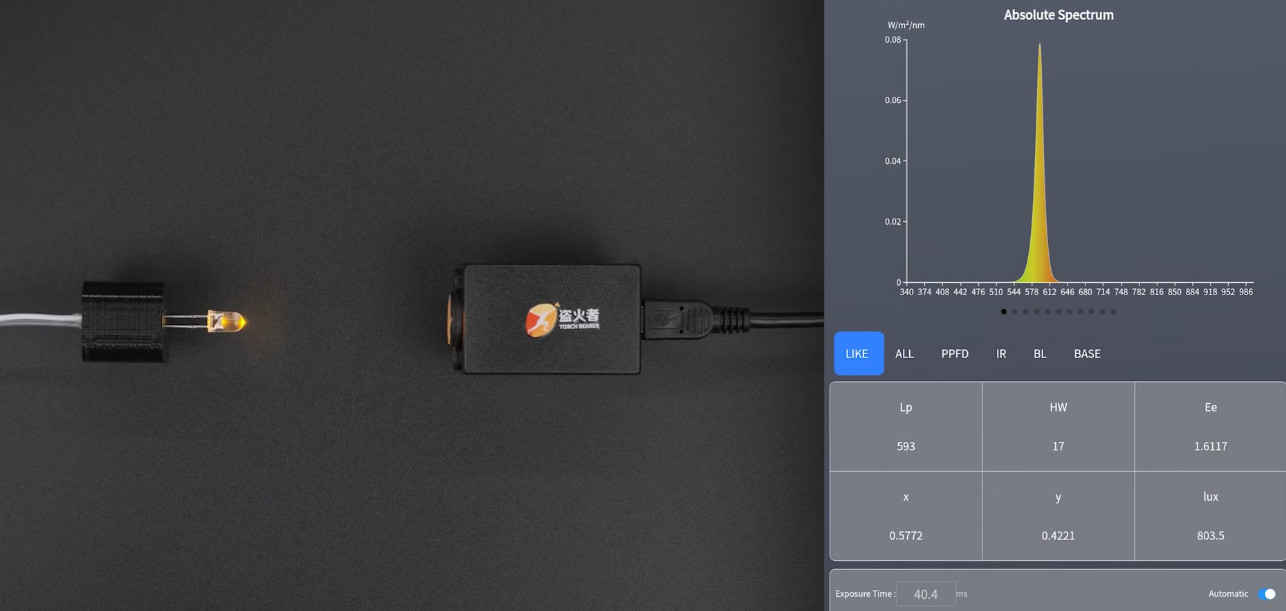
The object of this reverse engineering effort in the video below is a Microchip SAM4C32C, removed from one of the many smart electrical meters [Hash] loves to tear into. This microcontroller was supposed to be locked to prevent anyone from sniffing around in the code, but after soldering the chip to a target board and plugging it into a Chip Whisperer, [Hash] was able to find some odd-looking traces on the oscilloscope. Of particular interest was an unusual pattern on the scope while resetting the chip, which led him to an AI-assisted search for potential vulnerabilities. This allowed him to narrow down the target time for a power glitch, and in only a few seconds, the chip was forced to bypass its security bit and drop into its boot loader. With the keys to the kingdom, [Hash] was able to read the firmware and find all sorts of interesting tidbits.
Obviously, chip glitching isn’t always as easy as this, and even when a manufacturer leaves a vector like this in the chip, exploiting it does take some experience and finesse. But, if you’re going to get started glitching, it makes sense to start with the low-hanging fruit, and having [Hash] along for the ride doesn’t hurt either.













































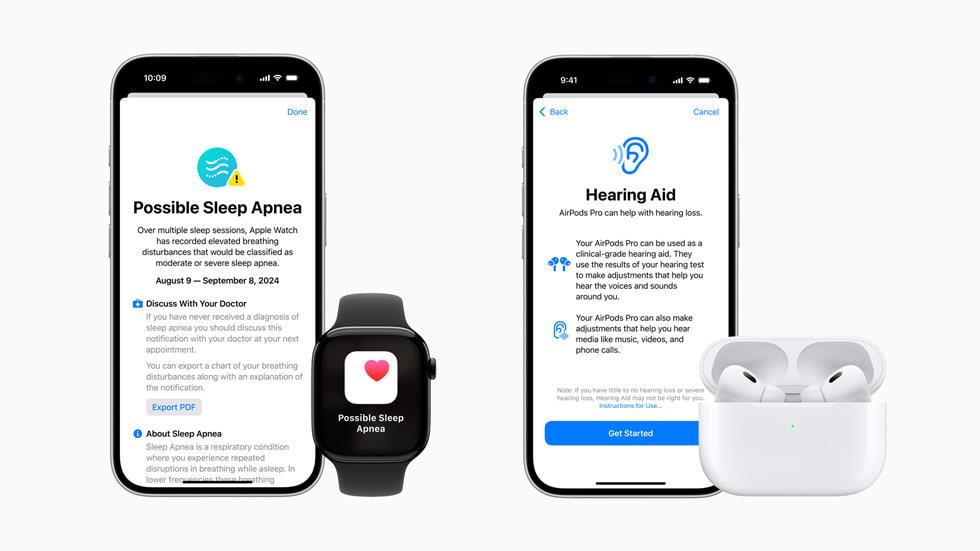














![Apple Watch Series 10 Prototype with Mystery Sensor Surfaces [Images]](https://www.iclarified.com/images/news/96892/96892/96892-640.jpg)

![Get Up to 69% Off Anker and Eufy Products on Final Day of Amazon's Big Spring Sale [Deal]](https://www.iclarified.com/images/news/96888/96888/96888-640.jpg)
![Apple Officially Releases macOS Sequoia 15.4 [Download]](https://www.iclarified.com/images/news/96887/96887/96887-640.jpg)












![What’s new in Android’s March 2025 Google System Updates [U: 3/31]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/01/google-play-services-1.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)














-xl-xl.jpg)















































































































































![[The AI Show Episode 141]: Road to AGI (and Beyond) #1 — The AI Timeline is Accelerating](https://www.marketingaiinstitute.com/hubfs/ep%20141.1.png)
![[The AI Show Episode 140]: New AGI Warnings, OpenAI Suggests Government Policy, Sam Altman Teases Creative Writing Model, Claude Web Search & Apple’s AI Woes](https://www.marketingaiinstitute.com/hubfs/ep%20140%20cover.png)
![[The AI Show Episode 139]: The Government Knows AGI Is Coming, Superintelligence Strategy, OpenAI’s $20,000 Per Month Agents & Top 100 Gen AI Apps](https://www.marketingaiinstitute.com/hubfs/ep%20139%20cover-2.png)



































































































































![From broke musician to working dev. How college drop-out Ryan Furrer taught himself to code [Podcast #166]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743189826063/2080cde4-6fc0-46fb-b98d-b3d59841e8c4.png?#)

























-1280x720.jpg?width=1920&height=1920&fit=bounds&quality=80&format=jpg&auto=webp#)


























































