Lazarus Group is No Longer Consider a Single APT Group, But Collection of Many Sub Groups
The cybersecurity landscape is witnessing a growing complexity in the attribution of Advanced Persistent Threat (APT) actors, particularly the North Korean-linked Lazarus group. Once considered a singular entity, Lazarus has evolved into a network of specialized subgroups with overlapping tactics, techniques, and procedures (TTPs), complicating efforts to classify and counter their activities. Initially, “Lazarus” referred […] The post Lazarus Group is No Longer Consider a Single APT Group, But Collection of Many Sub Groups appeared first on Cyber Security News.

The cybersecurity landscape is witnessing a growing complexity in the attribution of Advanced Persistent Threat (APT) actors, particularly the North Korean-linked Lazarus group.
Once considered a singular entity, Lazarus has evolved into a network of specialized subgroups with overlapping tactics, techniques, and procedures (TTPs), complicating efforts to classify and counter their activities.
Initially, “Lazarus” referred to a single APT group or a small set of coordinated actors.
However, as the scale of their operations expanded, the group fragmented into multiple subunits, each with distinct objectives and operational structures.
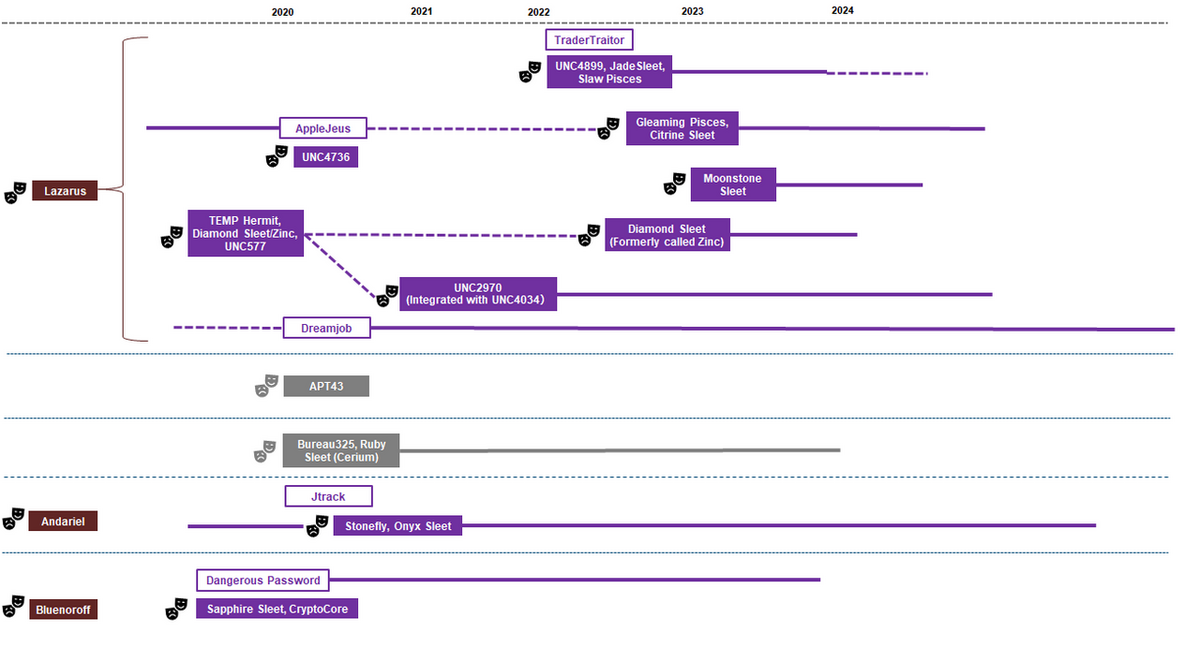
Today, Lazarus encompasses various subgroups such as Diamond Sleet, Citrine Sleet, Moonstone Sleet, and others.
This proliferation has led to inconsistent naming conventions across security vendors, further complicating attribution efforts.
Subgroups are often identified by their specific campaigns or malware usage.
For instance, campaigns like Operation Dreamjob and AppleJeus target cryptocurrency businesses, while others focus on ransomware attacks or corporate espionage.
The overlapping TTPs among these subgroups blur the lines between individual entities, making accurate attribution increasingly challenging.
Overlapping Tactics Among Subgroups
One of the most significant hurdles in attributing Lazarus activities is the overlap in their methods.
Multiple subgroups share similar initial attack vectors, command-and-control (C2) infrastructure, and malware components.
For example, several Lazarus-affiliated actors have been observed contacting targets via LinkedIn or other social platforms to persuade them to download malicious Python or npm packages hosted on PyPI or GitHub repositories.
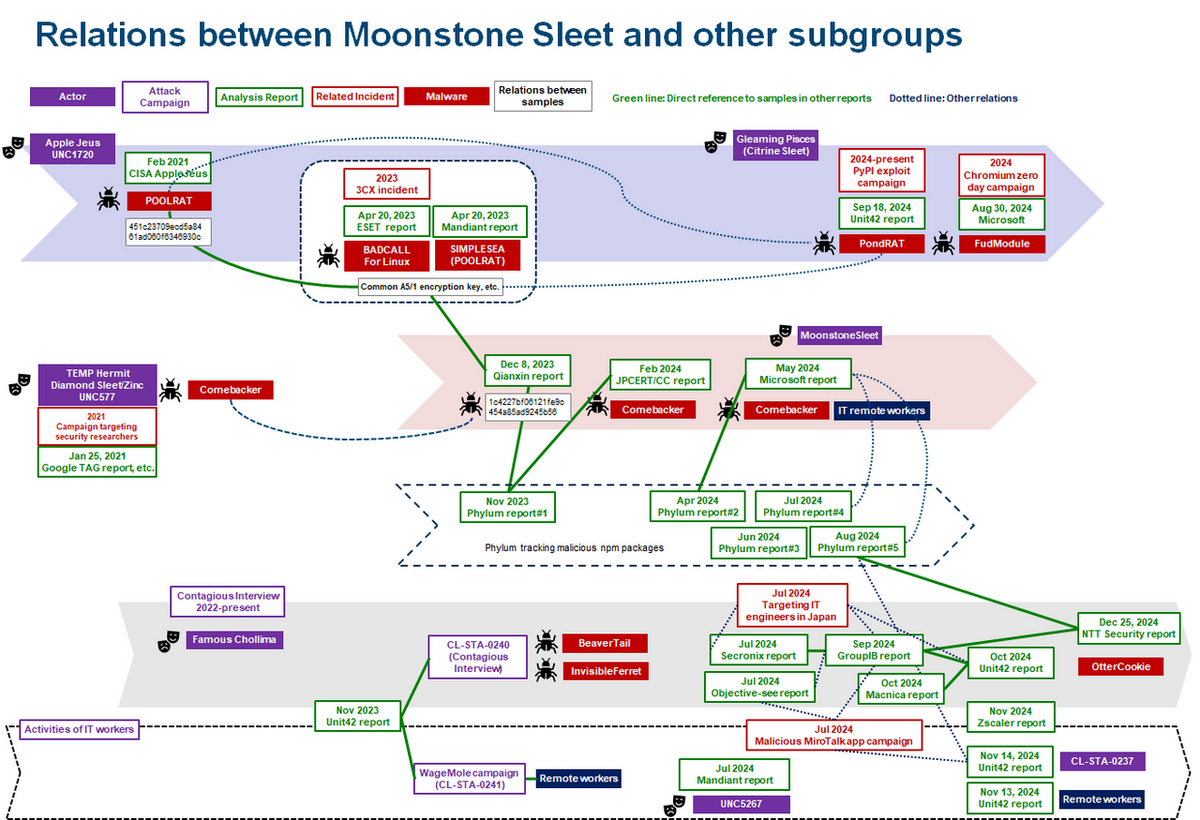
Moonstone Sleet and Citrine Sleet are two notable subgroups employing this tactic.
While they share similarities in their attack vectors and infrastructure, their objectives differ—Moonstone Sleet targets cryptocurrency theft and ransomware deployment, whereas Citrine Sleet focuses primarily on cryptocurrency businesses.
Detailed identification of Lazarus subgroups is critical for several reasons:
- Targeted Security Alerts: Each subgroup has unique objectives and target industries. Accurate profiling allows cybersecurity teams to issue specific alerts tailored to vulnerable sectors, such as cryptocurrency businesses or defense organizations.
- Effective Countermeasures: Understanding the organizational structure behind each subgroup enables more precise defensive strategies. For example, certain countermeasures may be effective against one subgroup but ineffective against another due to differences in their operational frameworks.
- Strategic Messaging: Subgroup-level attribution serves as a “message” to attackers, demonstrating the capabilities of defenders. It may also deter adversaries by making new tactics less viable or obsolete.
Recent trends indicate the emergence of task force-like groups that transcend traditional subgroup classifications.
For instance, Bureau325 and APT43 have been identified as entities that share TTPs across multiple Lazarus subgroups while utilizing tools common to other North Korean-linked actors like Kimsuky.
These developments suggest a shift toward more dynamic and flexible organizational structures within APT groups.
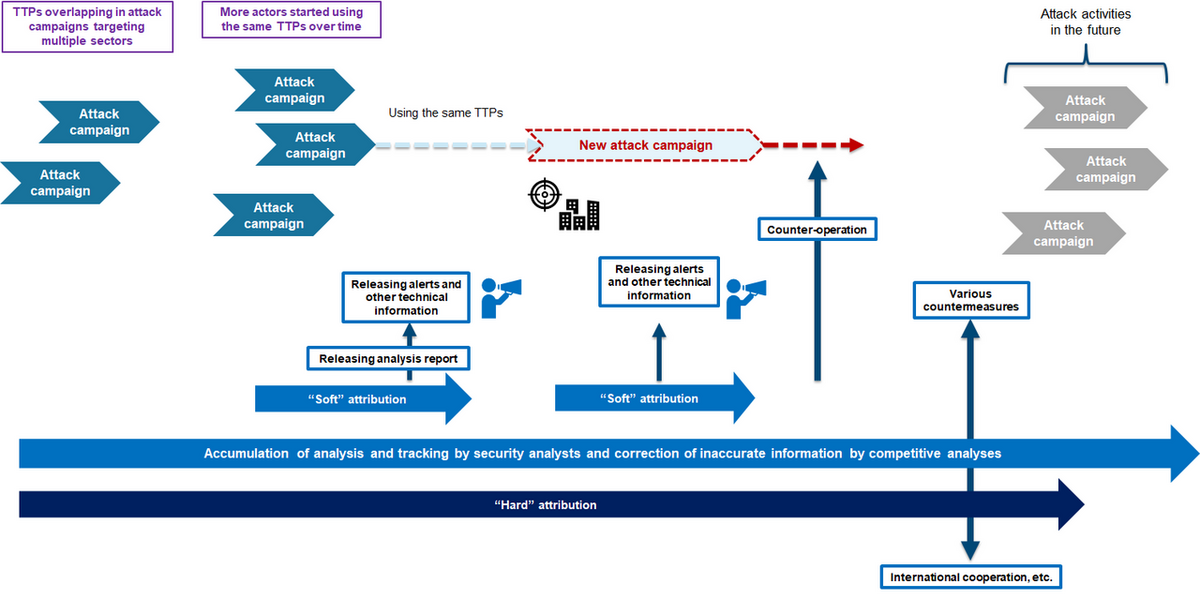
Balancing “Soft” and “Hard” Attribution
Attribution can be categorized into two types: “soft” attribution used for virtual grouping and profiling within the cybersecurity community, and “hard” attribution employed in legal contexts to identify specific individuals or organizations responsible for attacks.
While soft attribution aids in issuing timely alerts and deploying countermeasures, hard attribution is essential for long-term strategic responses.
However, achieving reliable hard attribution is often challenging due to insufficient evidence linking specific actors to state-sponsored activities.
The evolution of Lazarus from a singular entity into a network of interconnected subgroups underscores the growing complexity of modern cyber threats.
Accurate subgroup-level identification is not merely an academic exercise; it is vital for crafting effective defense strategies, issuing targeted alerts, and demonstrating cybersecurity capabilities to both allies and adversaries.
As threat actors continue to adapt their operations, cybersecurity analysts must refine their methodologies for tracking APT groups while addressing unresolved issues surrounding attribution and information disclosure.
The dynamic nature of Lazarus highlights the need for continuous vigilance and innovation in the field of cybersecurity.
Are You from SOC/DFIR Team? - Try Free Malware Research with ANY.RUN - Start Now
The post Lazarus Group is No Longer Consider a Single APT Group, But Collection of Many Sub Groups appeared first on Cyber Security News.




















![T-Mobile says it didn't compromise its values to get FCC to approve fiber deal [UPDATED]](https://m-cdn.phonearena.com/images/article/169088-two/T-Mobile-says-it-didnt-compromise-its-values-to-get-FCC-to-approve-fiber-deal-UPDATED.jpg?#)












































![Nomad Goods Launches 15% Sitewide Sale for 48 Hours Only [Deal]](https://www.iclarified.com/images/news/96899/96899/96899-640.jpg)


![Apple Watch Series 10 Prototype with Mystery Sensor Surfaces [Images]](https://www.iclarified.com/images/news/96892/96892/96892-640.jpg)

















































































































































































![[The AI Show Episode 142]: ChatGPT’s New Image Generator, Studio Ghibli Craze and Backlash, Gemini 2.5, OpenAI Academy, 4o Updates, Vibe Marketing & xAI Acquires X](https://www.marketingaiinstitute.com/hubfs/ep%20142%20cover.png)









































































































![Is this a suitable approach to architect a flutter app? [closed]](https://i.sstatic.net/4hMHGb1L.png)


















![From broke musician to working dev. How college drop-out Ryan Furrer taught himself to code [Podcast #166]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743189826063/2080cde4-6fc0-46fb-b98d-b3d59841e8c4.png?#)