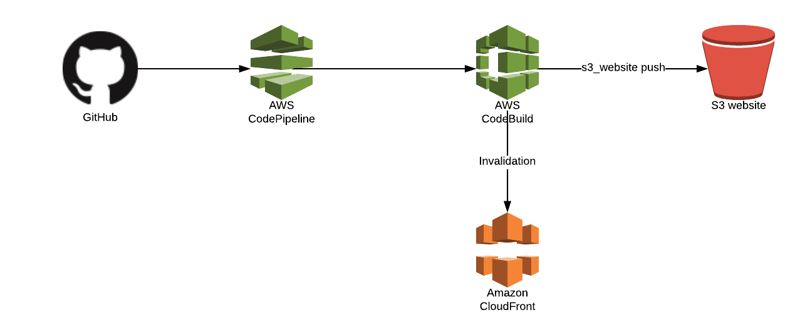
File System vs DBMS
File System: Follows a hierarchical structure for data storage. Client-Server Model (DBMS): A database management system (DBMS) operates on a client-server architecture, ensuring efficient data management and retrieval. Why DBMS? Fast Data Search: Searching in DBMS is faster due to indexing and optimized query execution. Efficient Memory Utilization: DBMS optimizes memory usage, reducing redundancy and improving performance. Location Independence: DBMS abstracts data location, making it independent of physical storage constraints. Concurrency Concurrent Access: Multiple users can access and manipulate data simultaneously. Example: Multiple customers can place orders on an e-commerce website at the same time. Concurrency Control Scenarios: Read-Read (RR): Multiple users reading the same data without conflicts. Read-Write (RW): One user reading while another writes, requiring synchronization. Write-Read (WR): A write operation followed by a read, ensuring consistency. Write-Write (WW): Two users attempting to write simultaneously, requiring conflict resolution. Security Role-Based Access Control (RBAC): Access is granted based on user roles (e.g., admin, editor, viewer). Hierarchical Security: Different levels of access permissions ensure controlled data access. Redundancy & Constraints Redundancy Reduction: DBMS minimizes data duplication using normalization. Constraints for Data Integrity: Primary Key: Ensures each record has a unique identifier. Foreign Key: Maintains referential integrity between tables. Unique & Not Null Constraints: Ensure data validity and consistency.
- File System: Follows a hierarchical structure for data storage.
- Client-Server Model (DBMS): A database management system (DBMS) operates on a client-server architecture, ensuring efficient data management and retrieval.
Why DBMS?
- Fast Data Search: Searching in DBMS is faster due to indexing and optimized query execution.
- Efficient Memory Utilization: DBMS optimizes memory usage, reducing redundancy and improving performance.
- Location Independence: DBMS abstracts data location, making it independent of physical storage constraints.
Concurrency
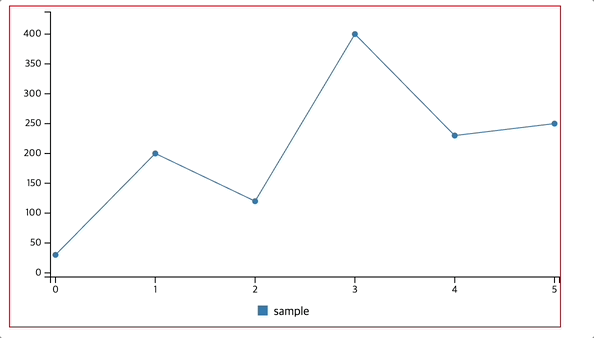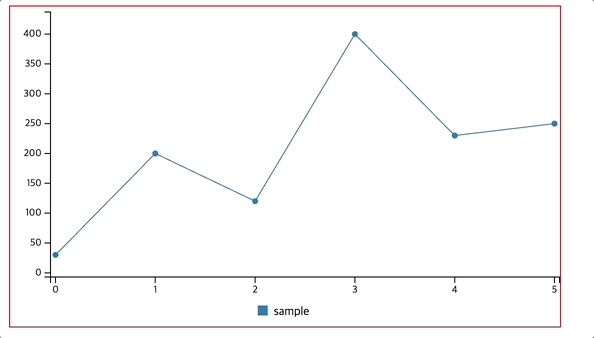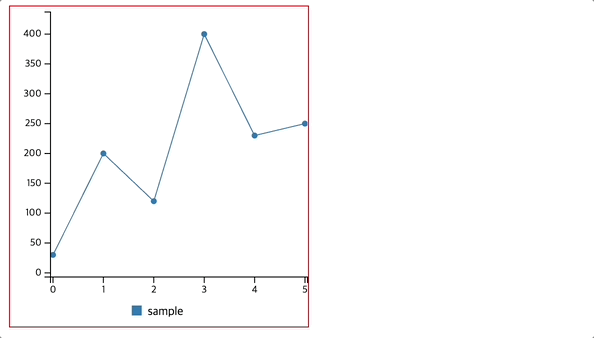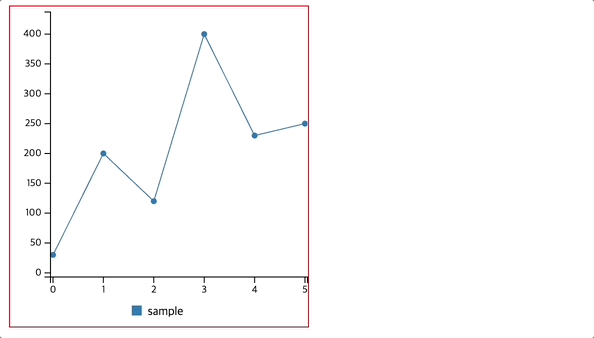
- Concurrent Access: Multiple users can access and manipulate data simultaneously.
- Example: Multiple customers can place orders on an e-commerce website at the same time.
-
Concurrency Control Scenarios:
- Read-Read (RR): Multiple users reading the same data without conflicts.
- Read-Write (RW): One user reading while another writes, requiring synchronization.
- Write-Read (WR): A write operation followed by a read, ensuring consistency.
- Write-Write (WW): Two users attempting to write simultaneously, requiring conflict resolution.
Security
- Role-Based Access Control (RBAC): Access is granted based on user roles (e.g., admin, editor, viewer).
- Hierarchical Security: Different levels of access permissions ensure controlled data access.
Redundancy & Constraints
- Redundancy Reduction: DBMS minimizes data duplication using normalization.
-
Constraints for Data Integrity:
- Primary Key: Ensures each record has a unique identifier.
- Foreign Key: Maintains referential integrity between tables.
- Unique & Not Null Constraints: Ensure data validity and consistency.





























































![Apple C1 vs Qualcomm Modem Performance [Speedtest]](https://www.iclarified.com/images/news/96767/96767/96767-640.jpg)
![Apple Studio Display On Sale for $1249 [Lowest Price Ever]](https://www.iclarified.com/images/news/96770/96770/96770-640.jpg)












![[Fixed] Chromecast (2nd gen) and Audio can’t Cast in ‘Untrusted’ outage](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2019/08/chromecast_audio_1.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)


























































































































































![[The AI Show Episode 139]: The Government Knows AGI Is Coming, Superintelligence Strategy, OpenAI’s $20,000 Per Month Agents & Top 100 Gen AI Apps](https://www.marketingaiinstitute.com/hubfs/ep%20139%20cover-2.png)


![[The AI Show Episode 138]: Introducing GPT-4.5, Claude 3.7 Sonnet, Alexa+, Deep Research Now in ChatGPT Plus & How AI Is Disrupting Writing](https://www.marketingaiinstitute.com/hubfs/ep%20138%20cover.png)