Phishing Attack Pivots to Mac After Windows Browser Defenses Improve
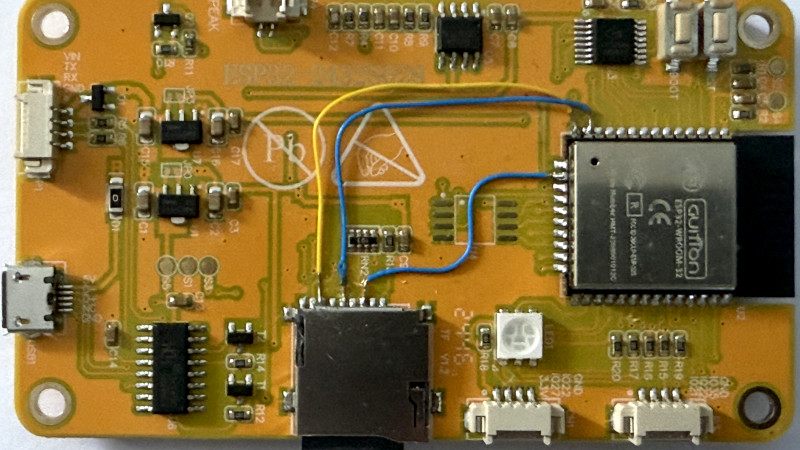
Security firm LayerX Labs has identified a sophisticated phishing campaign that recently began targeting Mac users after new browser protections rendered its Windows attacks less effective. The attackers had previously targeted Windows users with fake Microsoft security alerts, but then adapted their tactics in response to new anti-scareware features deployed in Chrome, Edge, and Firefox browsers earlier this year. According to LayerX, the original campaign relied on compromised websites that would display fake security warnings claiming the user's computer had been "compromised" and "locked." The malicious code would then freeze the webpage, creating the illusion that the computer was locked and prompting victims to enter their Windows credentials. What made the campaign particularly effective was its apparent credibility, since the phishing pages were hosted on Microsoft's Windows.net platform. The use of legitimate infrastructure also helped it bypass security tools that assess risk based on domain reputation. After browser developers implemented new anti-scareware protections in early 2025, LayerX said it observed a 90% drop in Windows-targeted attacks. Within just two weeks, the attackers had shifted their focus to Mac users, who weren't covered by the new protection measures. Phishing attack displaying fake security warning The Mac-targeted phishing pages use a similar visual design but have been tailored specifically for macOS and Safari users. However, the campaign is still using the Windows.net infrastructure. Victims typically arrive at these phishing pages through typos in URLs, which lead to compromised domain parking pages that rapidly redirect through multiple sites before landing on the malicious page. "While phishing campaigns targeting Mac users have existed before, they have rarely reached this level of sophistication," notes LayerX in their report. The security firm expects to see "a resurgent wave of attacks" as the threat actors continue to adapt their techniques to overcome new security protections. The takeaway for Mac users is that you should always verify website URLs when typing them into your browser, and consider using a security tool that can detect browser-level threats.This article, "Phishing Attack Pivots to Mac After Windows Browser Defenses Improve" first appeared on MacRumors.comDiscuss this article in our forums


The attackers had previously targeted Windows users with fake Microsoft security alerts, but then adapted their tactics in response to new anti-scareware features deployed in Chrome, Edge, and Firefox browsers earlier this year.
According to LayerX, the original campaign relied on compromised websites that would display fake security warnings claiming the user's computer had been "compromised" and "locked." The malicious code would then freeze the webpage, creating the illusion that the computer was locked and prompting victims to enter their Windows credentials.
What made the campaign particularly effective was its apparent credibility, since the phishing pages were hosted on Microsoft's Windows.net platform. The use of legitimate infrastructure also helped it bypass security tools that assess risk based on domain reputation.
After browser developers implemented new anti-scareware protections in early 2025, LayerX said it observed a 90% drop in Windows-targeted attacks. Within just two weeks, the attackers had shifted their focus to Mac users, who weren't covered by the new protection measures.
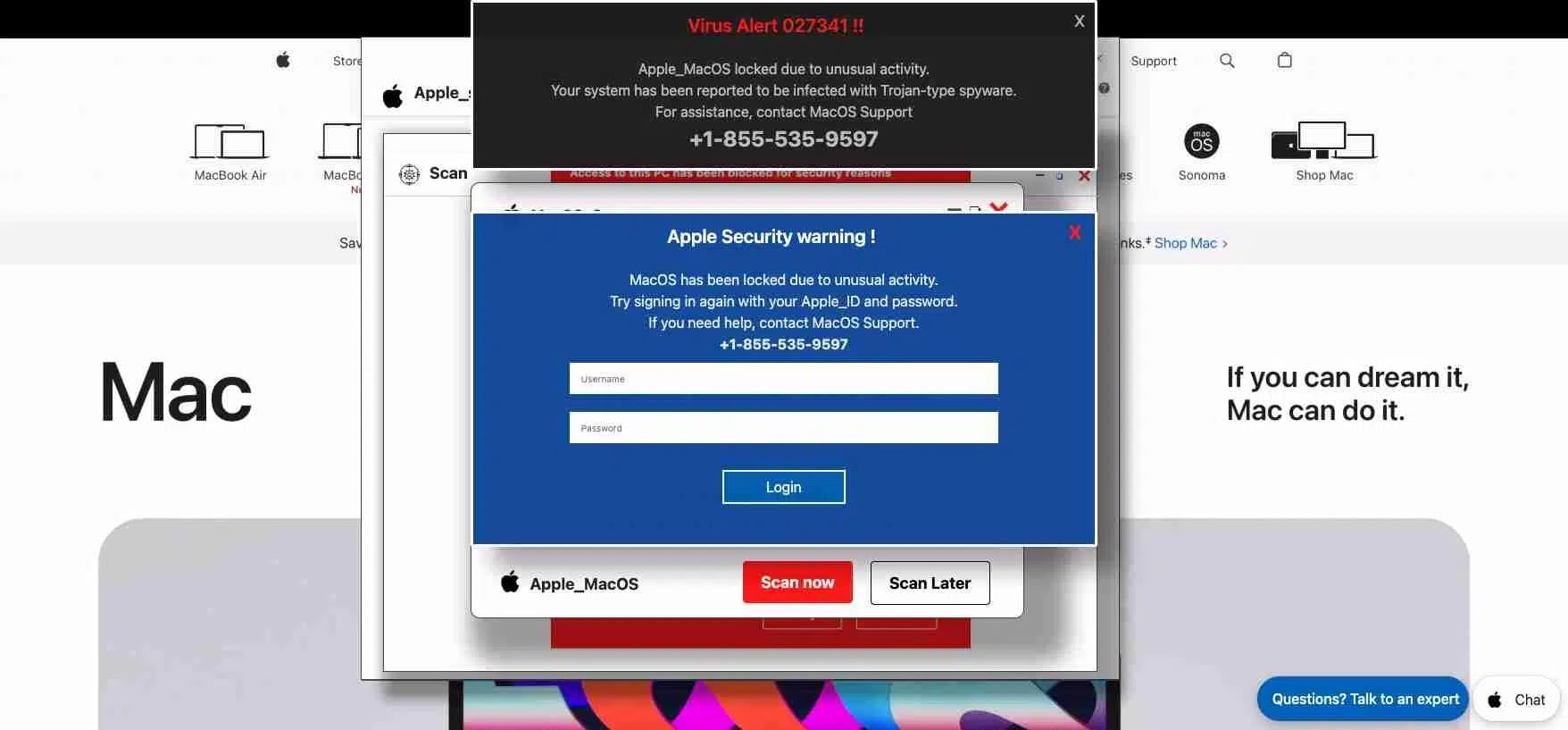
The Mac-targeted phishing pages use a similar visual design but have been tailored specifically for macOS and Safari users. However, the campaign is still using the Windows.net infrastructure. Victims typically arrive at these phishing pages through typos in URLs, which lead to compromised domain parking pages that rapidly redirect through multiple sites before landing on the malicious page.
"While phishing campaigns targeting Mac users have existed before, they have rarely reached this level of sophistication," notes LayerX in their report. The security firm expects to see "a resurgent wave of attacks" as the threat actors continue to adapt their techniques to overcome new security protections.
The takeaway for Mac users is that you should always verify website URLs when typing them into your browser, and consider using a security tool that can detect browser-level threats.
This article, "Phishing Attack Pivots to Mac After Windows Browser Defenses Improve" first appeared on MacRumors.com
Discuss this article in our forums































































![Apple Reorganizes Executive Team to Rescue Siri [Report]](https://www.iclarified.com/images/news/96777/96777/96777-640.jpg)






































































































































































![[The AI Show Episode 139]: The Government Knows AGI Is Coming, Superintelligence Strategy, OpenAI’s $20,000 Per Month Agents & Top 100 Gen AI Apps](https://www.marketingaiinstitute.com/hubfs/ep%20139%20cover-2.png)


![[The AI Show Episode 138]: Introducing GPT-4.5, Claude 3.7 Sonnet, Alexa+, Deep Research Now in ChatGPT Plus & How AI Is Disrupting Writing](https://www.marketingaiinstitute.com/hubfs/ep%20138%20cover.png)


































































































![What are good examples of 'preflight check patterns' on existing applications? [closed]](https://i.sstatic.net/yl2Tr80w.png)
























































![Release: Rendering Ranger: R² [Rewind]](https://images-3.gog-statics.com/48a9164e1467b7da3bb4ce148b93c2f92cac99bdaa9f96b00268427e797fc455.jpg)