Ultimate Guide for API key management in Flutter Projects
Slide: Introduction of Topic News on API Keys Government - US Treasure hacked by filtered API keyunauthorized entities Exploits BeyondTrust API Key to Access U.S. Treasury Systems and Documents BeyondTrust customers hit by wave of attacks linked to compromised API key AI - Deepseek API keys filtered LLM Hijackers Quickly Incorporate DeepSeek API Keys Money/ Coinbase security issues / Not Rotating your keys / legacy API Keys - Coinbase Security Issues: The Risks of Exposed Legacy API Keys $25 million stolen Hacker Uses Compromised API Keys to Steal $25M from Kronos Research Section 2 - Understanding API Keys Common Pitfalls and How to Avoid Them Slide: Common Pitfalls and How to Avoid Them / best practices Some common mistakes include hardcoding API keys in the source code and not rotating them regularly. Managing API keys effectively is crucial for maintaining the security and functionality of your applications. Here are some best practices to follow: Secure Storage: Store API keys securely to prevent unauthorized access. Avoid hardcoding them in your source code. Instead, use environment variables, encrypted databases, or dedicated secrets management services A. Access Control: Limit access to API keys within your organization. Implement the principle of least privilege, ensuring that only authorized personnel can retrieve and use the keys A. Usage Monitoring: Keep track of how and where API keys are used. Monitoring helps identify unusual patterns that might indicate a security issue or a breach A. Rotation and Renewal: Regularly update or rotate API keys, especially if there's a suspicion of compromise or as a routine security practice. This minimizes the window of opportunity for any misuse if a key is compromised A. Encryption: Always encrypt API keys, both at rest and in transit. This ensures that even if the keys are intercepted, they cannot be easily used A. Auditing and Monitoring: Conduct regular audits and monitoring of API key usage to detect and respond to any unauthorized access or anomalies A. Key Generation: Generate API keys that are unique, random, and non-guessable. Use alphanumeric and special characters to enhance security B. User Education: Educate users about the importance of API key security and the best practices for handling them. Inform them that API keys should be treated like passwords and stored securely B. Section 3 - API Key Management in Development Slide: DO NOT EVER Committing a secret key to version control, making it visible to everyone on the Internet

Slide: Introduction of Topic
News on API Keys
-
Government - US Treasure hacked by filtered API keyunauthorized entities Exploits BeyondTrust API Key to Access U.S. Treasury Systems and Documents
AI - Deepseek API keys filtered LLM Hijackers Quickly Incorporate DeepSeek API Keys
-
Money/ Coinbase security issues / Not Rotating your keys / legacy API Keys - Coinbase Security Issues: The Risks of Exposed Legacy API Keys
- $25 million stolen Hacker Uses Compromised API Keys to Steal $25M from Kronos Research
Section 2 - Understanding API Keys Common Pitfalls and How to Avoid Them
Slide: Common Pitfalls and How to Avoid Them / best practices
Some common mistakes include hardcoding API keys in the source code and not rotating them regularly.
Managing API keys effectively is crucial for maintaining the security and functionality of your applications. Here are some best practices to follow:
Secure Storage: Store API keys securely to prevent unauthorized access. Avoid hardcoding them in your source code. Instead, use environment variables, encrypted databases, or dedicated secrets management services A.
Access Control: Limit access to API keys within your organization. Implement the principle of least privilege, ensuring that only authorized personnel can retrieve and use the keys A.
Usage Monitoring: Keep track of how and where API keys are used. Monitoring helps identify unusual patterns that might indicate a security issue or a breach A.
Rotation and Renewal: Regularly update or rotate API keys, especially if there's a suspicion of compromise or as a routine security practice. This minimizes the window of opportunity for any misuse if a key is compromised A.
Encryption: Always encrypt API keys, both at rest and in transit. This ensures that even if the keys are intercepted, they cannot be easily used A.
Auditing and Monitoring: Conduct regular audits and monitoring of API key usage to detect and respond to any unauthorized access or anomalies A.
Key Generation: Generate API keys that are unique, random, and non-guessable. Use alphanumeric and special characters to enhance security B.
User Education: Educate users about the importance of API key security and the best practices for handling them. Inform them that API keys should be treated like passwords and stored securely B.
Section 3 - API Key Management in Development
Slide: DO NOT EVER
- Committing a secret key to version control, making it visible to everyone on the Internet
































































![Apple M4 Mac Mini on Sale for $499 [Lowest Price Ever]](https://www.iclarified.com/images/news/96788/96788/96788-640.jpg)
![Apple Shares First Look and Premiere Date for 'The Buccaneers' Season Two [Video]](https://www.iclarified.com/images/news/96786/96786/96786-640.jpg)
![Apple to Craft Key Foldable iPhone Components From Liquid Metal [Kuo]](https://www.iclarified.com/images/news/96784/96784/96784-640.jpg)







































































































_Federico_Caputo_Alamy.jpg?#)

































































![[The AI Show Episode 139]: The Government Knows AGI Is Coming, Superintelligence Strategy, OpenAI’s $20,000 Per Month Agents & Top 100 Gen AI Apps](https://www.marketingaiinstitute.com/hubfs/ep%20139%20cover-2.png)


![[The AI Show Episode 138]: Introducing GPT-4.5, Claude 3.7 Sonnet, Alexa+, Deep Research Now in ChatGPT Plus & How AI Is Disrupting Writing](https://www.marketingaiinstitute.com/hubfs/ep%20138%20cover.png)



















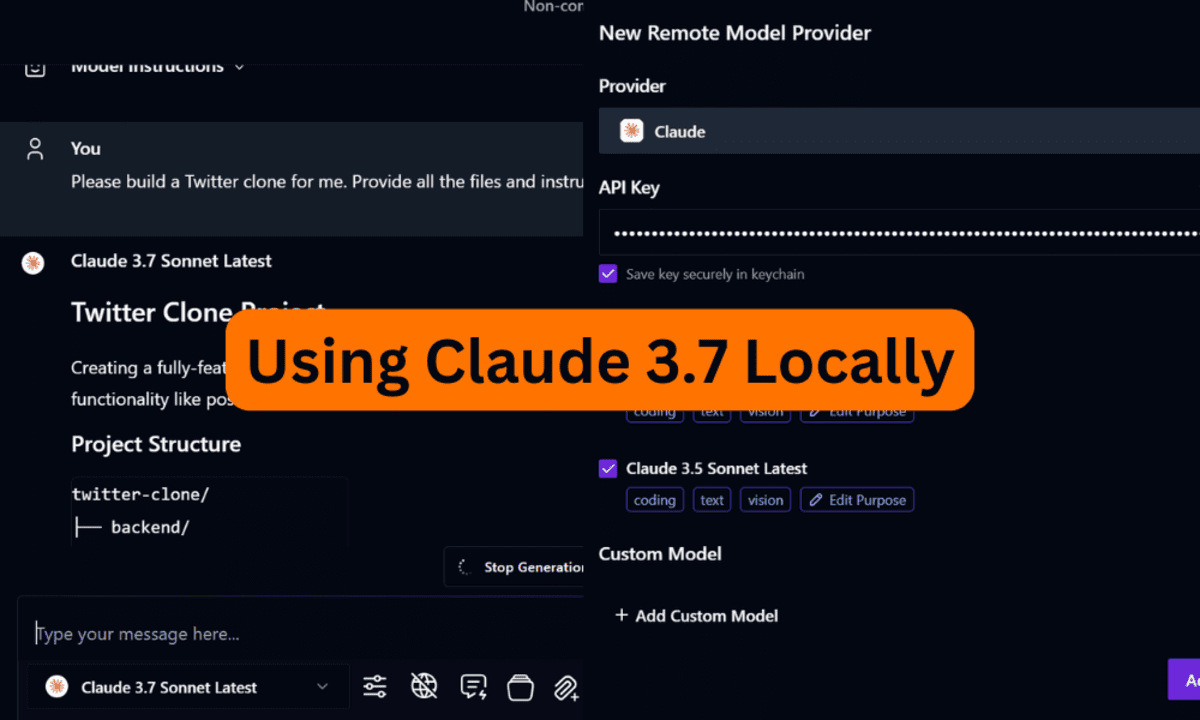





















































![[DEALS] The All-in-One CompTIA Certification Prep Courses Bundle (90% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)
































![From hating coding to programming satellites at age 37 with Francesco Ciulla [Podcast #165]](https://cdn.hashnode.com/res/hashnode/image/upload/v1742585568977/09b25b8e-8c92-4f4b-853f-64b7f7915980.png?#)






























.jpg?width=1920&height=1920&fit=bounds&quality=80&format=jpg&auto=webp#)






.png?#)