A Tactical Overview of Penetration Testing: From Recon to Reporting
Penetration testing — or pentesting — is not just an ethical hack. It's a structured simulation of real-world attacks, conducted to uncover vulnerabilities before adversaries do. This post outlines the lifecycle of a typical pentest engagement, along with tools and tactics at each stage. 1. Reconnaissance (Passive & Active) Objective: Gather intel without alerting the target. Passive: WHOIS, DNS records, public repos, social profiles Active: Port scanning, service enumeration Tools: whois example.com nmap -sV -p- target.ip 2. Scanning & Enumeration Map the attack surface and identify open services, software versions, and potential misconfigurations. nmap -A -T4 target.ip nikto -h http://target 3. Exploitation Leverage known vulnerabilities to gain access. Targets can include web apps, network services, weak credentials, or outdated software. Example: CVE exploitation via Metasploit msfconsole use exploit/windows/smb/ms17_010_eternalblue Or custom scripts for targeted payloads. 4. Privilege Escalation Once inside, escalate to root or admin to access sensitive data or full control. Check for misconfigured sudoers Inspect running services Scan for known kernel exploits Toolkits: LinPEAS winPEAS GTFOBins 5. Persistence & Lateral Movement Simulate real-world adversaries by maintaining access and pivoting across systems. Add new users, cronjobs SSH keys Tunneling via SSH or reverse shells 6. Reporting Deliver a clear, actionable, and technically precise report. Sections: Executive summary Vulnerability breakdown (CVSS) Proof-of-concept evidence Mitigation strategies Final Thoughts Pentesting is a blend of engineering, psychology, and discipline. It’s not about chaos — it's about clarity. Know your tools, document your steps, and always respect the scope. In future posts, we’ll deep-dive into each stage with real-world examples and lab exercises.
Penetration testing — or pentesting — is not just an ethical hack.
It's a structured simulation of real-world attacks, conducted to uncover vulnerabilities before adversaries do.
This post outlines the lifecycle of a typical pentest engagement, along with tools and tactics at each stage.
1. Reconnaissance (Passive & Active)
Objective: Gather intel without alerting the target.
- Passive: WHOIS, DNS records, public repos, social profiles
- Active: Port scanning, service enumeration
Tools:
whois example.com
nmap -sV -p- target.ip
2. Scanning & Enumeration
Map the attack surface and identify open services, software versions, and potential misconfigurations.
nmap -A -T4 target.ip
nikto -h http://target
3. Exploitation
Leverage known vulnerabilities to gain access.
Targets can include web apps, network services, weak credentials, or outdated software.
Example: CVE exploitation via Metasploit
msfconsole
use exploit/windows/smb/ms17_010_eternalblue
Or custom scripts for targeted payloads.
4. Privilege Escalation
Once inside, escalate to root or admin to access sensitive data or full control.
- Check for misconfigured sudoers
- Inspect running services
- Scan for known kernel exploits
Toolkits:
- LinPEAS
- winPEAS
- GTFOBins
5. Persistence & Lateral Movement
Simulate real-world adversaries by maintaining access and pivoting across systems.
- Add new users, cronjobs
- SSH keys
- Tunneling via SSH or reverse shells
6. Reporting
Deliver a clear, actionable, and technically precise report.
Sections:
- Executive summary
- Vulnerability breakdown (CVSS)
- Proof-of-concept evidence
- Mitigation strategies
Final Thoughts
Pentesting is a blend of engineering, psychology, and discipline.
It’s not about chaos — it's about clarity.
Know your tools, document your steps, and always respect the scope.
In future posts, we’ll deep-dive into each stage with real-world examples and lab exercises.











































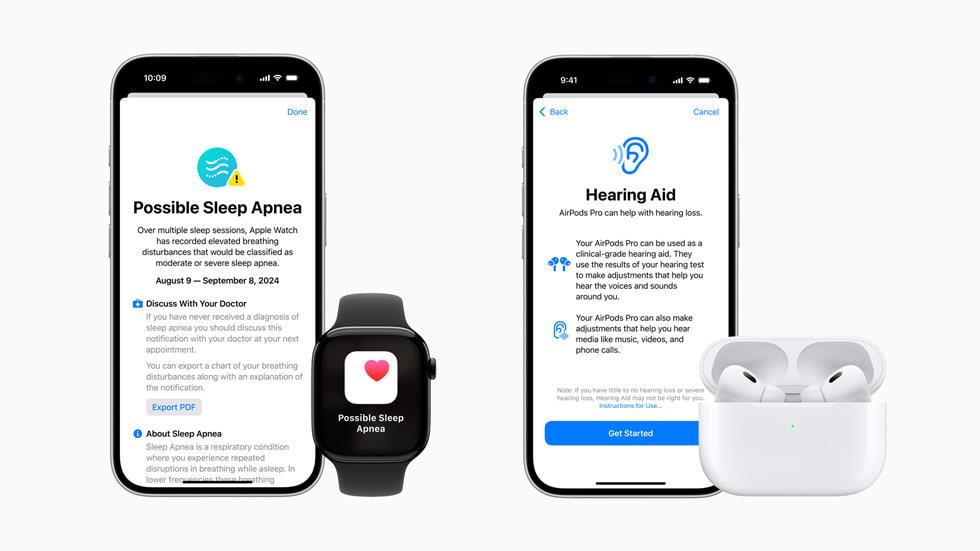















![Apple Watch Series 10 Prototype with Mystery Sensor Surfaces [Images]](https://www.iclarified.com/images/news/96892/96892/96892-640.jpg)

![Get Up to 69% Off Anker and Eufy Products on Final Day of Amazon's Big Spring Sale [Deal]](https://www.iclarified.com/images/news/96888/96888/96888-640.jpg)
![Apple Officially Releases macOS Sequoia 15.4 [Download]](https://www.iclarified.com/images/news/96887/96887/96887-640.jpg)













![What’s new in Android’s March 2025 Google System Updates [U: 3/31]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/01/google-play-services-1.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)













-xl-xl.jpg)

















































































































































![[The AI Show Episode 141]: Road to AGI (and Beyond) #1 — The AI Timeline is Accelerating](https://www.marketingaiinstitute.com/hubfs/ep%20141.1.png)
![[The AI Show Episode 140]: New AGI Warnings, OpenAI Suggests Government Policy, Sam Altman Teases Creative Writing Model, Claude Web Search & Apple’s AI Woes](https://www.marketingaiinstitute.com/hubfs/ep%20140%20cover.png)
![[The AI Show Episode 139]: The Government Knows AGI Is Coming, Superintelligence Strategy, OpenAI’s $20,000 Per Month Agents & Top 100 Gen AI Apps](https://www.marketingaiinstitute.com/hubfs/ep%20139%20cover-2.png)















































































































![Is this a suitable approach to architect a flutter app? [closed]](https://i.sstatic.net/4hMHGb1L.png)

















![From broke musician to working dev. How college drop-out Ryan Furrer taught himself to code [Podcast #166]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743189826063/2080cde4-6fc0-46fb-b98d-b3d59841e8c4.png?#)





























-1280x720.jpg?width=1920&height=1920&fit=bounds&quality=80&format=jpg&auto=webp#)


























































