Splunk RCE Vulnerability Let Attackers Execute Arbitrary Code Via File Upload
Splunk has released patches to address a high-severity Remote Code Execution (RCE) vulnerability affecting Splunk Enterprise and Splunk Cloud Platform. The vulnerability, identified as CVE-2025-20229, could allow a low-privileged user to execute arbitrary code by uploading malicious files. The vulnerability exists in Splunk Enterprise versions before 9.3.3, 9.2.5, and 9.1.8, as well as Splunk Cloud […] The post Splunk RCE Vulnerability Let Attackers Execute Arbitrary Code Via File Upload appeared first on Cyber Security News.
.webp?#)
Splunk has released patches to address a high-severity Remote Code Execution (RCE) vulnerability affecting Splunk Enterprise and Splunk Cloud Platform. The vulnerability, identified as CVE-2025-20229, could allow a low-privileged user to execute arbitrary code by uploading malicious files.
The vulnerability exists in Splunk Enterprise versions before 9.3.3, 9.2.5, and 9.1.8, as well as Splunk Cloud Platform versions before 9.3.2408.104, 9.2.2406.108, 9.2.2403.114, and 9.1.2312.208.
According to Splunk’s advisory, a low-privileged user without “admin” or “power” roles could exploit the vulnerability. This is achieved through uploading a file to the “$SPLUNK_HOME/var/run/splunk/apptemp” directory, bypassing necessary authorization checks.
Splunk has assigned a CVSSv3.1 score of 8.0, marking it as a high-severity issue with the vector CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:U/C:H/I:H/A:H.
Stop attacks before they start, powered by a 97% precise neural Network to Detect Cyber Attacks
To remediate the vulnerability, Splunk recommends upgrading Splunk Enterprise to versions 9.4.0, 9.3.3, 9.2.5, 9.1.8, or later. For Splunk Cloud Platform users, Splunk is actively monitoring and patching instances.
Vulnerability in Splunk Secure Gateway App
In addition to the RCE vulnerability, Splunk disclosed a separate high-severity vulnerability affecting the Splunk Secure Gateway app.
This vulnerability, identified as CVE-2025-20231, could allow a low-privileged user to search using the permissions of a higher-privileged user, potentially leading to sensitive information disclosure.
Product Affected Versions Fixed Versions Splunk Enterprise 9.3.0-9.3.2, 9.2.0-9.2.4, 9.1.0-9.1.7 9.3.3, 9.2.5, 9.1.8, 9.4.0 Splunk Cloud Platform 9.3.2408.100-9.3.2408.103, 9.2.2406.100-9.2.2406.107, Below 9.2.2403.113, Below 9.1.2312.207 9.3.2408.104, 9.2.2406.108, 9.2.2403.114, 9.1.2312.208 Splunk Secure Gateway App Below 3.8.38, Below 3.7.23 3.8.38, 3.7.23
The vulnerability impacts Splunk Enterprise versions below 9.4.1, 9.3.3, 9.2.5, and 9.1.8 and Splunk Secure Gateway app versions below 3.8.38 and 3.7.23 on Splunk Cloud Platform.
The Splunk Secure Gateway exposes user session and authorization tokens in clear text within the splunk_secure_gateway.log file when calling the /services/ssg/secrets REST endpoint.
Successful exploitation requires an attacker to trick a victim into initiating a request within their browser. Splunk has rated this vulnerability as high severity, with a CVSSv3.1 score of 7.1 and a vector of CVSS:3.1/AV:N/AC:H/PR:L/UI:R/S:U/C:H/I:H/A:H.
To address this issue, Splunk advises upgrading Splunk Enterprise to versions 9.4.1, 9.3.3, 9.2.5, and 9.1.8 or later. Splunk is also actively patching Splunk Cloud Platform instances.
Users can disable the Splunk Secure Gateway App as a workaround, though this may impact functionality for Splunk Mobile, Spacebridge, and Mission Control users.
Splunk encourages customers to stay informed about security updates and apply patches promptly to protect their systems from potential exploits.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
The post Splunk RCE Vulnerability Let Attackers Execute Arbitrary Code Via File Upload appeared first on Cyber Security News.













































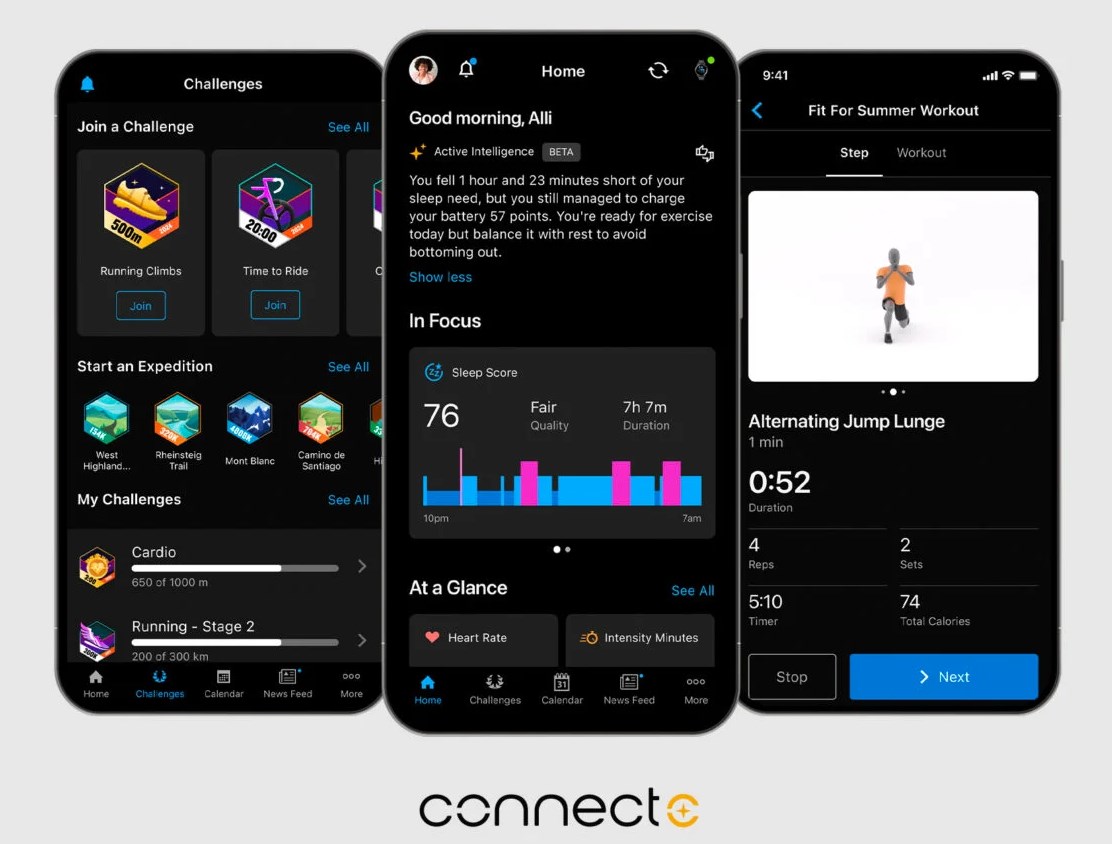
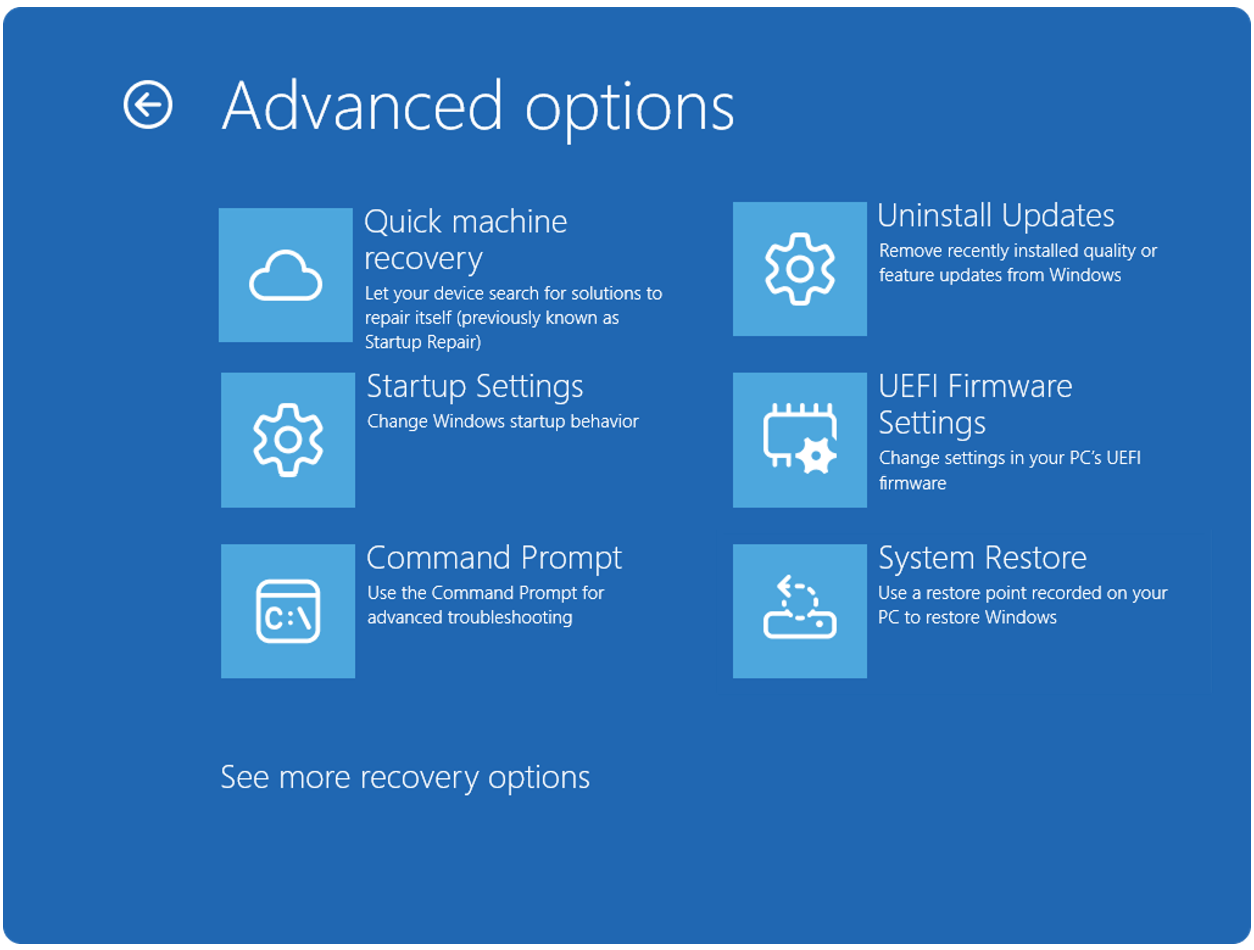


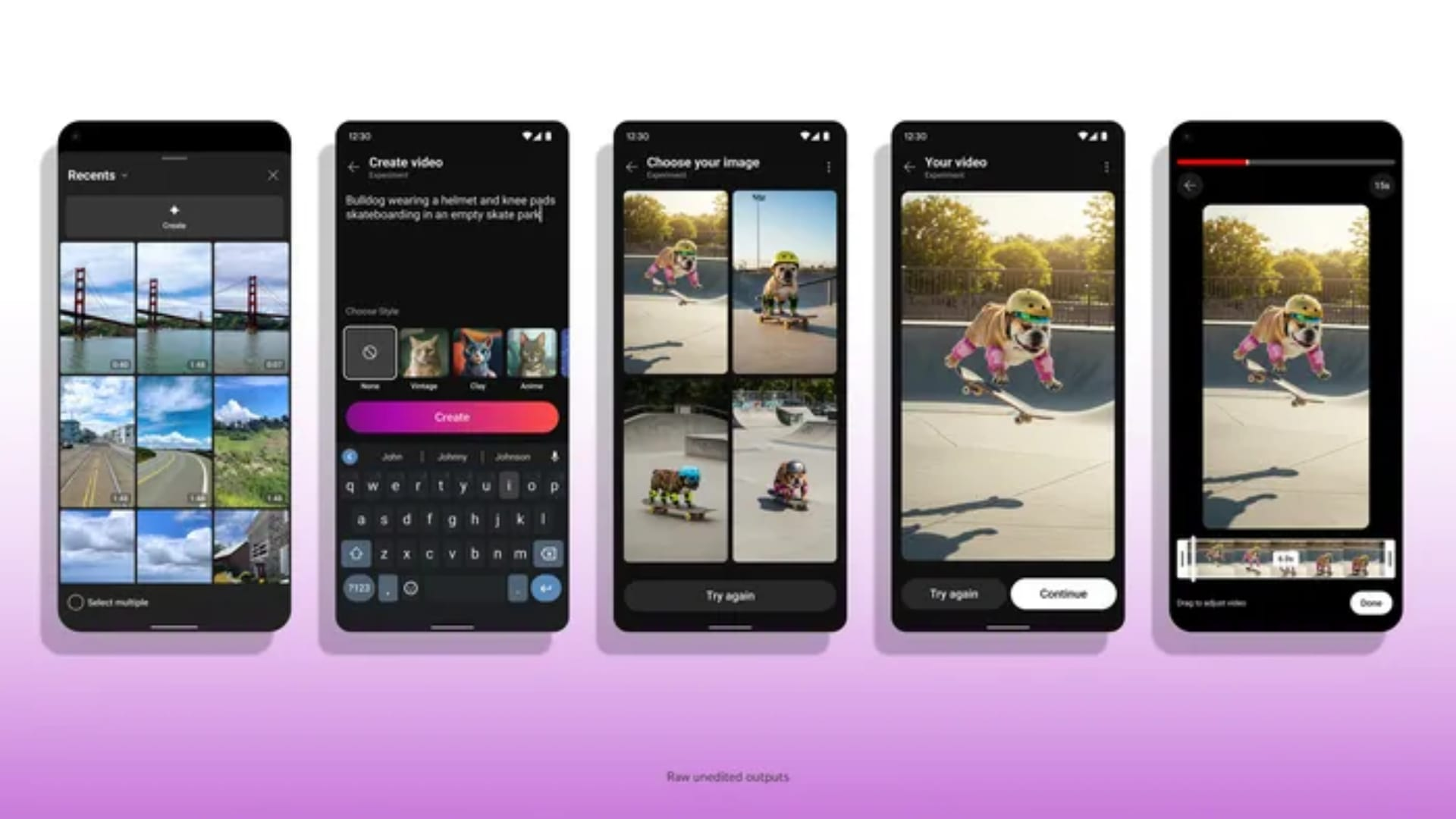

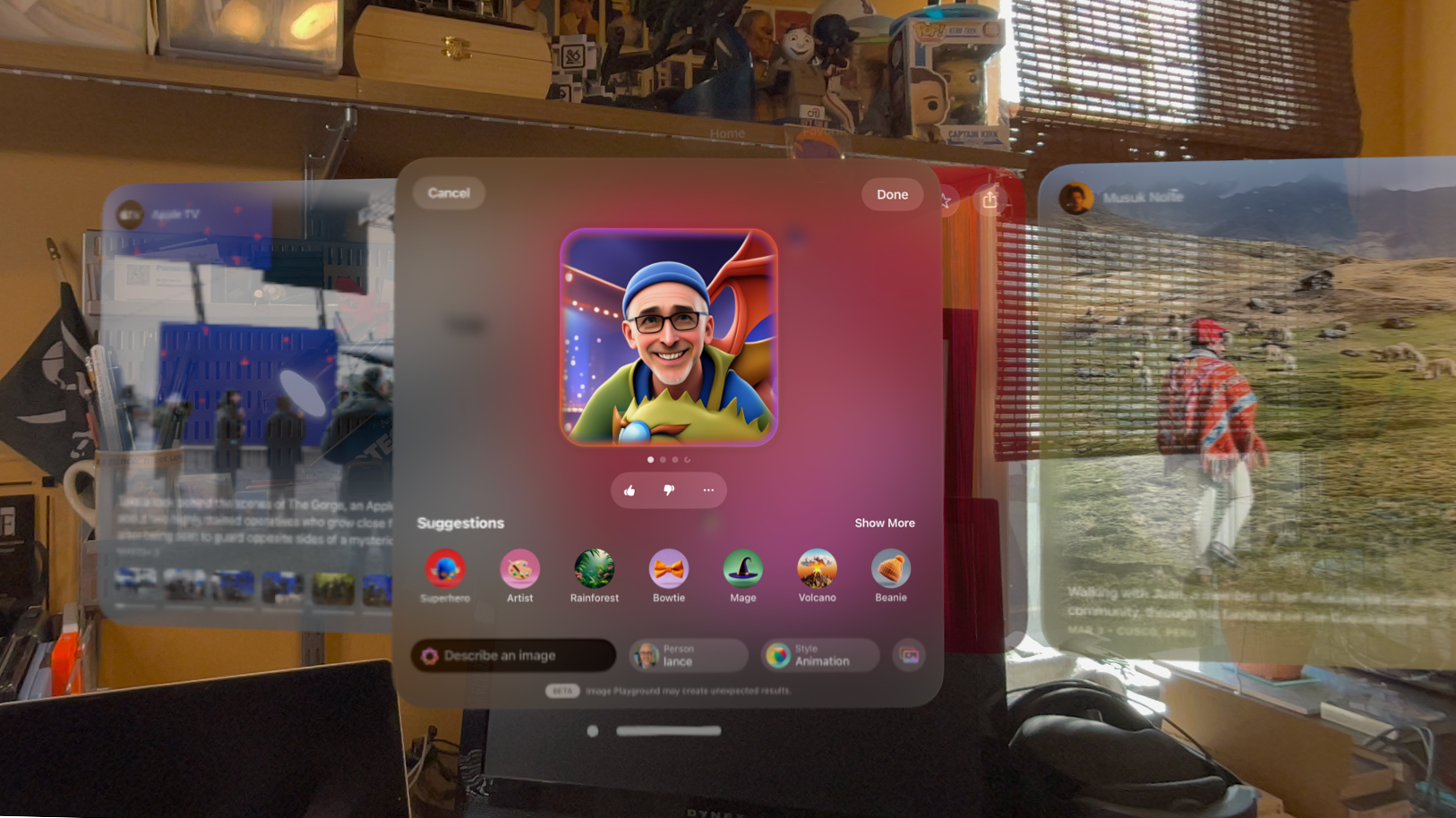











![Apple Watch Series 10 Prototype with Mystery Sensor Surfaces [Images]](https://www.iclarified.com/images/news/96892/96892/96892-640.jpg)

![Get Up to 69% Off Anker and Eufy Products on Final Day of Amazon's Big Spring Sale [Deal]](https://www.iclarified.com/images/news/96888/96888/96888-640.jpg)
![Apple Officially Releases macOS Sequoia 15.4 [Download]](https://www.iclarified.com/images/news/96887/96887/96887-640.jpg)












![What’s new in Android’s March 2025 Google System Updates [U: 3/31]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/01/google-play-services-1.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)














-xl-xl.jpg)















































































































































![[The AI Show Episode 141]: Road to AGI (and Beyond) #1 — The AI Timeline is Accelerating](https://www.marketingaiinstitute.com/hubfs/ep%20141.1.png)
![[The AI Show Episode 140]: New AGI Warnings, OpenAI Suggests Government Policy, Sam Altman Teases Creative Writing Model, Claude Web Search & Apple’s AI Woes](https://www.marketingaiinstitute.com/hubfs/ep%20140%20cover.png)
![[The AI Show Episode 139]: The Government Knows AGI Is Coming, Superintelligence Strategy, OpenAI’s $20,000 Per Month Agents & Top 100 Gen AI Apps](https://www.marketingaiinstitute.com/hubfs/ep%20139%20cover-2.png)



































































































































![From broke musician to working dev. How college drop-out Ryan Furrer taught himself to code [Podcast #166]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743189826063/2080cde4-6fc0-46fb-b98d-b3d59841e8c4.png?#)

























-1280x720.jpg?width=1920&height=1920&fit=bounds&quality=80&format=jpg&auto=webp#)





















































.webp?#)




