YouTube Creators Under Attack via Brand Collaborators Requests Using Clickflix Technique
A sophisticated phishing campaign dubbed the “Clickflix Technique” has emerged targeting YouTube content creators through seemingly legitimate brand collaboration requests. This new attack vector exploits creators’ eagerness to secure sponsorship deals by disguising malware payloads as partnership documentation. Cybercriminals initiate contact via email or social media, posing as marketing representatives from established brands offering lucrative […] The post YouTube Creators Under Attack via Brand Collaborators Requests Using Clickflix Technique appeared first on Cyber Security News.

A sophisticated phishing campaign dubbed the “Clickflix Technique” has emerged targeting YouTube content creators through seemingly legitimate brand collaboration requests.
This new attack vector exploits creators’ eagerness to secure sponsorship deals by disguising malware payloads as partnership documentation.
Cybercriminals initiate contact via email or social media, posing as marketing representatives from established brands offering lucrative deals that require the creator to review “campaign materials” hosted on compromised domains or cloud storage.
The attackers typically approach creators with subscriber counts between 10,000 and 500,000, carefully crafting messages that reference the creator’s content style and previous sponsorships to establish credibility.
Upon clicking the malicious links, creators are directed to professional-looking landing pages mimicking popular file-sharing services where they’re prompted to download what appears to be a PDF contract or campaign brief.
CloudSek researchers identified this campaign in early March 2025, noting that the malware employs a multi-stage infection process designed to evade traditional security solutions.
.webp)
Their analysis revealed that over 2,300 creators have been targeted across gaming, technology review, and lifestyle niches, with approximately 18% of targets successfully compromised.
The attack leverages social engineering principles combined with technical deception, often including time-sensitive offers to pressure creators into hasty decisions.
Victims report receiving customized messages referencing specific videos they’ve produced, indicating significant reconnaissance efforts by the threat actors prior to initiating contact.
Infection Mechanism Exploits JavaScript Obfuscation
The malware’s primary infection vector employs a sophisticated JavaScript downloader that executes when victims open what appears to be a standard HTML preview page.
.webp)
The initial payload utilizes multiple layers of obfuscation, with the final stage resembling this simplified example:-
const decoderKey = navigator.userAgent.slice(0,8);
eval(function(p,a,c,k,e,d){
/* heavily obfuscated PowerShell downloader */
return p;
}('powershell -w hidden -e JGNsaWVudCA9...'))This obfuscated code ultimately triggers a PowerShell command that downloads a stealer targeting browser data with particular emphasis on YouTube Studio credentials, Google authentication tokens, and cryptocurrency wallet information.
The malware establishes persistence through Windows Registry modifications and scheduled tasks with innocuous names like “GoogleUpdateTask” to avoid detection during routine system inspections.
The attack demonstrates the growing sophistication of targeted campaigns against content creators who increasingly represent valuable targets due to their monetization potential and access to engaged audience networks.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
The post YouTube Creators Under Attack via Brand Collaborators Requests Using Clickflix Technique appeared first on Cyber Security News.





































































![Apple's M5 iPad Pro Enters Advanced Testing for 2025 Launch [Gurman]](https://www.iclarified.com/images/news/96865/96865/96865-640.jpg)
![M5 MacBook Pro Set for Late 2025, Major Redesign Waits Until 2026 [Gurman]](https://www.iclarified.com/images/news/96868/96868/96868-640.jpg)
![Apple to Revamp Health App with AI-Powered Doctor [Gurman]](https://www.iclarified.com/images/news/96870/96870/96870-640.jpg)
![Lowest Prices Ever: Apple Pencil Pro Just $79.99, USB-C Pencil Only $49.99 [Deal]](https://www.iclarified.com/images/news/96863/96863/96863-640.jpg)













![What Google Messages features are rolling out [March 2025]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2023/12/google-messages-name-cover.png?resize=1200%2C628&quality=82&strip=all&ssl=1)
































































































































































![[The AI Show Episode 141]: Road to AGI (and Beyond) #1 — The AI Timeline is Accelerating](https://www.marketingaiinstitute.com/hubfs/ep%20141.1.png)
![[The AI Show Episode 140]: New AGI Warnings, OpenAI Suggests Government Policy, Sam Altman Teases Creative Writing Model, Claude Web Search & Apple’s AI Woes](https://www.marketingaiinstitute.com/hubfs/ep%20140%20cover.png)
![[The AI Show Episode 139]: The Government Knows AGI Is Coming, Superintelligence Strategy, OpenAI’s $20,000 Per Month Agents & Top 100 Gen AI Apps](https://www.marketingaiinstitute.com/hubfs/ep%20139%20cover-2.png)





















































































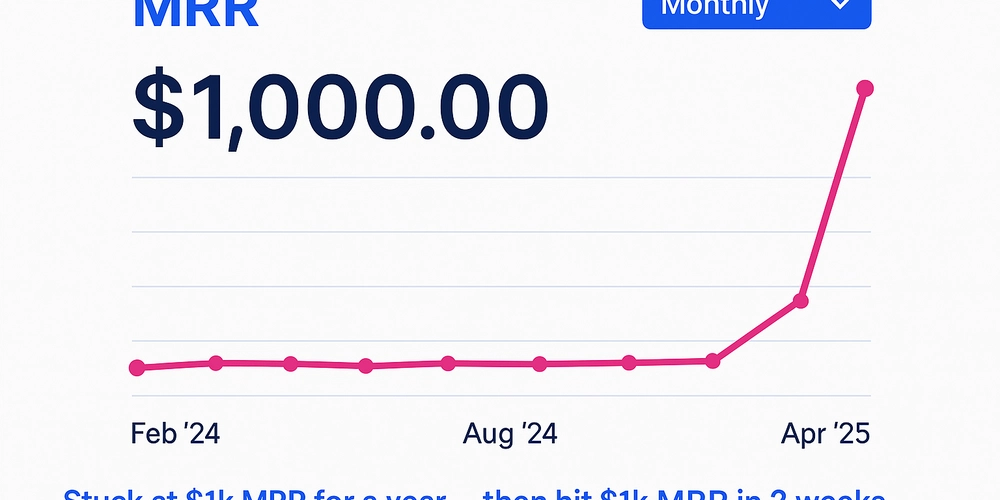




































![From broke musician to working dev. How college drop-out Ryan Furrer taught himself to code [Podcast #166]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743189826063/2080cde4-6fc0-46fb-b98d-b3d59841e8c4.png?#)



![[FREE EBOOKS] The Ultimate Linux Shell Scripting Guide, Artificial Intelligence for Cybersecurity & Four More Best Selling Titles](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)



























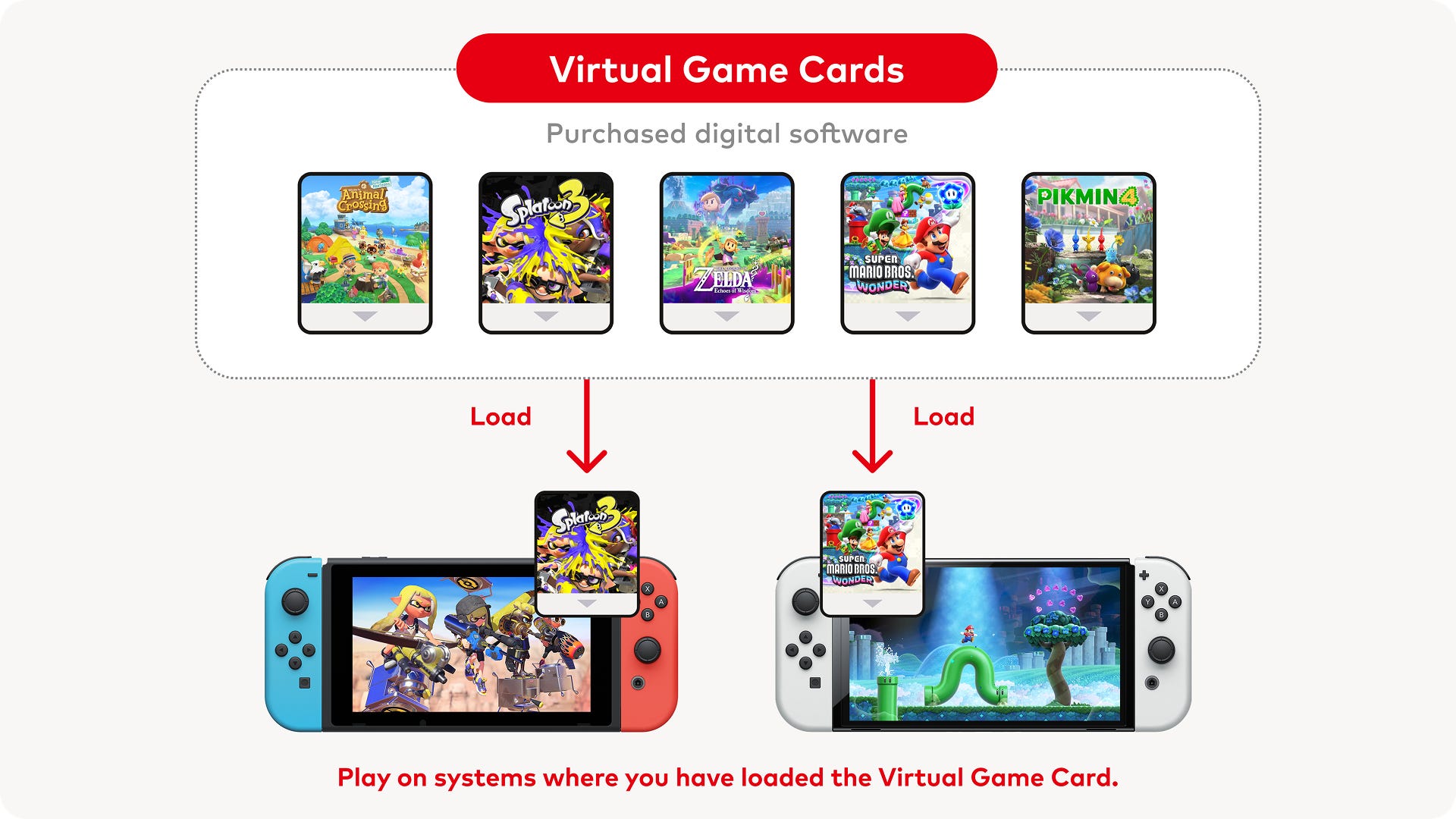






.png?#)






















































