Deploying a Static Website with AWS S3, CloudFront, and WAF Web ACL
In this post, I’ll walk through how I deployed a static website using Amazon S3 and distributed it globally with CloudFront. Then, I applied security hardening using AWS Web ACL to defend against common threats. Step 1: Build the Static Site I created a simple HTML and CSS layout: index.html CloudFront Static Site body { background-color: #0e0e0e; color: #f4f4f4; font-family: sans-serif; display: flex; justify-content: center; align-items: center; height: 100vh; margin: 0; } .container { text-align: center; } Hello, CloudFront! This site is served from an S3 bucket and distributed globally with AWS CloudFront. style.css body { background-color: #0e0e0e; color: #f4f4f4; font-family: sans-serif; display: flex; justify-content: center; align-items: center; height: 100vh; margin: 0; } .container { text-align: center; } I then uploaded both files to a new S3 bucket named: javier-static-site-2025 Step 2: Enable Static Website Hosting on S3 In the S3 bucket settings, I enabled static website hosting: Selected “Host a static website” Entered index.html as the index document Left the error document blank Step 3: Configure Bucket Policy for Public Read Access To allow CloudFront (and users) to access the files, I added a bucket policy: { "Version": "2012-10-17", "Statement": [ { "Sid": "PublicRead", "Effect": "Allow", "Principal": "*", "Action": "s3:GetObject", "Resource": "arn:aws:s3:::javier-static-site-2025/*" } ] } Step 4: Preview the Website on S3 After applying the policy, I accessed the site directly via the S3 static hosting endpoint: http://javier-static-site-2025.s3-website-ap-southeast-2.amazonaws.com The site loaded correctly, showing the custom “Hello, CloudFront!” message. Step 5: Set Up a CloudFront Distribution I created a CloudFront distribution to globally accelerate and cache content: Origin Domain: S3 website endpoint (not the default bucket domain) Origin Access: Public (since I allowed public access in the S3 bucket policy) Viewer Protocol Policy: Redirect HTTP to HTTPS Allowed Methods: GET, HEAD (default) Compression: Enabled Step 6: Link CloudFront to Web ACL (WAF) I created a Web ACL named CloudFrontWebACL and associated it with the CloudFront distribution. Adding AWS WAF Rules With the Web ACL CloudFrontWebACL created and associated with my CloudFront distribution, I added several rules to strengthen the site’s security posture. Managed Rule Sets Added AWSManagedRulesCommonRuleSet Covers a wide range of common threats like LFI, bad bots, size restrictions, and more. AWSManagedRulesAmazonIpReputationList Blocks traffic from known malicious IPs. AWSManagedRulesSQLiRuleSet Specifically targets SQL injection attempts. Custom Rate Limiting Rule – LimitRequestsByIP Blocks any IP that makes more than 10 requests in a 5-minute window. For all managed rules, I set the action override to “Block” to ensure they actively drop malicious traffic rather than just counting matches. Testing the Web ACL This is the part where studying for the eJPT certification came in handy. To validate the effectiveness of each rule, I ran several tests using curl. 1. Rate Limiting for i in {1..25}; do curl -s -o /dev/null "https://" & done wait Result: Requests beyond the 10-request threshold were blocked as expected. I confirmed this via the WAF metrics panel in CloudWatch, which showed exactly 25 blocked requests. 2. SQL Injection Attempt curl "https:///?id=1%27%3B%20DROP%20TABLE%20users--" Result: The request was blocked with a 403 error, showing that the SQLiRuleSet triggered correctly. 3. SQLMap User-Agent Fingerprint curl -A "sqlmap/1.0" https:// Result: Blocked with a 403 error. This confirmed that malicious User-Agent headers were being filtered properly by the common rule set. 4. Path-Based Recon curl https:///admin Result: Returned a 404 error from S3 (object not found), but was not blocked by WAF. This is expected — WAF only triggers on known threat patterns, not missing pages. CloudWatch Logs Verification To confirm that the WAF rules were actively blocking traffic, I reviewed the metrics and charts under the “WAF > Web ACLs > CloudFrontWebACL” section. The rate limiting rule showed 25 blocked requests at the exact timestamp of my curl loop test. SQLi and User-Agent tests were also reflected in blocked request counts under the relevant rules. Final Thoughts This project helped me understand how to: Deploy a static site via S3 and accelerate it globally with CloudFront Configure bucket permissions and static hosting Set up and customize AWS WAF rules Simulate attacks and observe real-time block metrics in CloudWatch The final result is a minimal, fast, and

In this post, I’ll walk through how I deployed a static website using Amazon S3 and distributed it globally with CloudFront. Then, I applied security hardening using AWS Web ACL to defend against common threats.
Step 1: Build the Static Site
I created a simple HTML and CSS layout:
index.html
CloudFront Static Site
Hello, CloudFront!
This site is served from an S3 bucket and distributed globally with AWS CloudFront.
style.css
body {
background-color: #0e0e0e;
color: #f4f4f4;
font-family: sans-serif;
display: flex;
justify-content: center;
align-items: center;
height: 100vh;
margin: 0;
}
.container {
text-align: center;
}
I then uploaded both files to a new S3 bucket named:
javier-static-site-2025
Step 2: Enable Static Website Hosting on S3
In the S3 bucket settings, I enabled static website hosting:
Selected “Host a static website”
Entered index.html as the index document
Left the error document blank
Step 3: Configure Bucket Policy for Public Read Access
To allow CloudFront (and users) to access the files, I added a bucket policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "PublicRead",
"Effect": "Allow",
"Principal": "*",
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::javier-static-site-2025/*"
}
]
}
Step 4: Preview the Website on S3
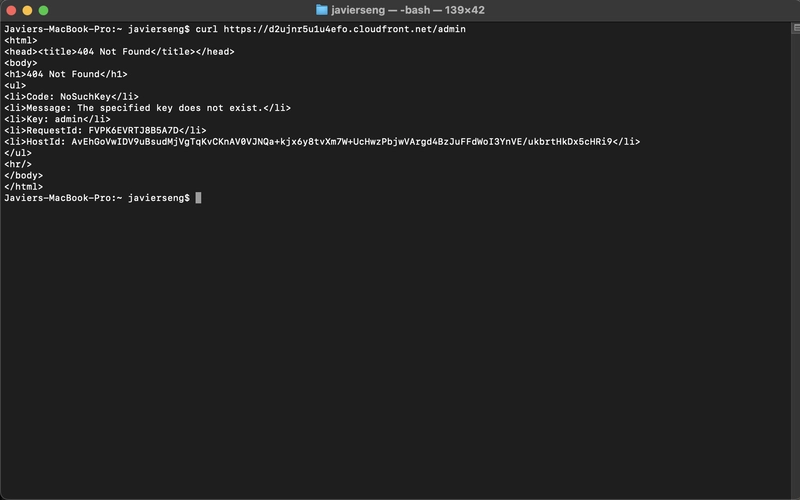
After applying the policy, I accessed the site directly via the S3 static hosting endpoint:
http://javier-static-site-2025.s3-website-ap-southeast-2.amazonaws.com
The site loaded correctly, showing the custom “Hello, CloudFront!” message.
Step 5: Set Up a CloudFront Distribution
I created a CloudFront distribution to globally accelerate and cache content:
Origin Domain: S3 website endpoint (not the default bucket domain)
Origin Access: Public (since I allowed public access in the S3 bucket policy)
Viewer Protocol Policy: Redirect HTTP to HTTPS
Allowed Methods: GET, HEAD (default)
Compression: Enabled
Step 6: Link CloudFront to Web ACL (WAF)
I created a Web ACL named CloudFrontWebACL and associated it with the CloudFront distribution.
Adding AWS WAF Rules
With the Web ACL CloudFrontWebACL created and associated with my CloudFront distribution, I added several rules to strengthen the site’s security posture.
Managed Rule Sets Added
AWSManagedRulesCommonRuleSet
Covers a wide range of common threats like LFI, bad bots, size restrictions, and more.AWSManagedRulesAmazonIpReputationList
Blocks traffic from known malicious IPs.AWSManagedRulesSQLiRuleSet
Specifically targets SQL injection attempts.Custom Rate Limiting Rule – LimitRequestsByIP
Blocks any IP that makes more than 10 requests in a 5-minute window.
For all managed rules, I set the action override to “Block” to ensure they actively drop malicious traffic rather than just counting matches.
Testing the Web ACL
This is the part where studying for the eJPT certification came in handy. To validate the effectiveness of each rule, I ran several tests using curl.
1. Rate Limiting
for i in {1..25}; do
curl -s -o /dev/null "https://" &
done
wait
Result:
Requests beyond the 10-request threshold were blocked as expected. I confirmed this via the WAF metrics panel in CloudWatch, which showed exactly 25 blocked requests.
2. SQL Injection Attempt
curl "https://
Result:
The request was blocked with a 403 error, showing that the SQLiRuleSet triggered correctly.
3. SQLMap User-Agent Fingerprint
curl -A "sqlmap/1.0" https://
Result:
Blocked with a 403 error. This confirmed that malicious User-Agent headers were being filtered properly by the common rule set.
4. Path-Based Recon
curl https://
Result:
Returned a 404 error from S3 (object not found), but was not blocked by WAF. This is expected — WAF only triggers on known threat patterns, not missing pages.
CloudWatch Logs Verification
To confirm that the WAF rules were actively blocking traffic, I reviewed the metrics and charts under the “WAF > Web ACLs > CloudFrontWebACL” section.
The rate limiting rule showed 25 blocked requests at the exact timestamp of my curl loop test.
SQLi and User-Agent tests were also reflected in blocked request counts under the relevant rules.
Final Thoughts
This project helped me understand how to:
Deploy a static site via S3 and accelerate it globally with CloudFront
Configure bucket permissions and static hosting
Set up and customize AWS WAF rules
Simulate attacks and observe real-time block metrics in CloudWatch
The final result is a minimal, fast, and well-protected static site — an ideal foundation for future personal projects.







































































![Apple Developing Battery Case for iPhone 17 Air Amid Battery Life Concerns [Report]](https://www.iclarified.com/images/news/97208/97208/97208-640.jpg)
![Apple to Split iPhone Launches Across Fall and Spring in Major Shakeup [Report]](https://www.iclarified.com/images/news/97211/97211/97211-640.jpg)
![Apple to Move Camera to Top Left, Hide Face ID Under Display in iPhone 18 Pro Redesign [Report]](https://www.iclarified.com/images/news/97212/97212/97212-640.jpg)
![AirPods 4 On Sale for $99 [Lowest Price Ever]](https://www.iclarified.com/images/news/97206/97206/97206-640.jpg)







































































































_Inge_Johnsson-Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)



























































































































![[The AI Show Episode 145]: OpenAI Releases o3 and o4-mini, AI Is Causing “Quiet Layoffs,” Executive Order on Youth AI Education & GPT-4o’s Controversial Update](https://www.marketingaiinstitute.com/hubfs/ep%20145%20cover.png)






























































































































































![From Art School Drop-out to Microsoft Engineer with Shashi Lo [Podcast #170]](https://cdn.hashnode.com/res/hashnode/image/upload/v1746203291209/439bf16b-c820-4fe8-b69e-94d80533b2df.png?#)

![[FREE EBOOKS] Learn Computer Forensics — 2nd edition, AI and Business Rule Engines for Excel Power Users & Four More Best Selling Titles](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)