Qodana 2025.1 Release
As we continue improving Qodana, we’re excited to introduce a set of powerful updates that enhance performance, improve security analysis, and offer better integration opportunities for you and your team. Let’s take a look at some of the most exciting changes with the Qodana 2025.1 release! Try Qodana OWASP Top 10: covering even more categories […]

![New OWASP Security Inspections, Better Azure and GitLab Integrations, Pro C++ Linter [EAP], Switching To Kotlin K2 Mode, and More!](https://blog.jetbrains.com/wp-content/uploads/2025/05/qd-featured_blog_1280x720_en-1.png)
As we continue improving Qodana, we’re excited to introduce a set of powerful updates that enhance performance, improve security analysis, and offer better integration opportunities for you and your team. Let’s take a look at some of the most exciting changes with the Qodana 2025.1 release!
OWASP Top 10: covering even more categories
At Qodana, we take security very seriously, and recently discussed inspections that commonly make it to the OWASP Top 10.
We also know that configuring taint rules for the security analyzers can be a difficult and time-consuming task, often requiring manual effort to detect rules and correctly configure it.
To simplify this process, we provide predefined taint configuration, built on various benchmarks and external providers, automatically covering common sources and sinks.
Qodana now includes predefined taint rules for the most common categories of OWASP Top 10:2021 vulnerabilities: (A01, A03, A07, A08, A10). This significantly improves issue detection out of the box, minimizing user effort while ensuring broad security coverage.
To address issues with the problem’s trace reconstruction, we had to rethink the way issue propagation being shown to the user. Now we’re capable of showing even more complex cases including tricky aliasing.

Feedback received and addressed: for those who need deeper customization, taint rules can be configured using KTS files, allowing users to define both library and user codes as sources or sinks. This flexibility ensures that security analysis adapts to project-specific needs without unnecessary complexity.
TL;DR
- Automatic detection for common security flaws.
- 700+ new configuration entries covering common frameworks and libraries.
- The ability to add configuration on your own: customize via KTS files to define sources and sinks.
Enhanced Azure & GitLab CI/CD Integrations
To improve adoption beyond GitHub, we’ve made major enhancements to Azure and GitLab integrations. These changes streamline workflows and enable better visibility into analysis results.
Azure improvements
In Azure, it’s now possible to reduce the time spent on PR analysis by only analyzing files that were changed using pr-mode. Also, instead of getting results in the build log, the Qodana extension provides you with a summary in the Extensions tab.
This release also integrates the powerful Qodana Quick Fix feature into your analysis. This allows you to fix some problems in your code and apply them to the branch you’ve analyzed or create a pull request with suggested fixes. To use this feature you will need to update the Qodana pipeline configuration.
TL;DR
- Get faster PR analysis by checking only modified files.
- Results now appear in the Extensions tab instead of cluttering the build log.
- Auto-apply fixes to the analyzed branch or create a PR with suggested changes.



GitLab enhancements
Now you can use the new Qodana component to perform analysis in your repository. This means that instead of using the linter container directly, you can configure Qodana with a predefined set of needed arguments (there is no need to understand all the steps to launch Qodana; the component does it for you).
The new component supports mr-mode (the same as pr-mode in Azure) for fast analysis in merge requests, which analyses only the changed files, summary comments in merge requests and quick fixes. To use it you’ll need to include the Qodana component in your pipeline configuration file.
TL;DR
- Use the new Qodana component for simplified configuration.
- It supports merge request (MR) mode to analyze only changed files.
- it provides summary comments and quick fixes.



Pro C++ Linter [EAP]
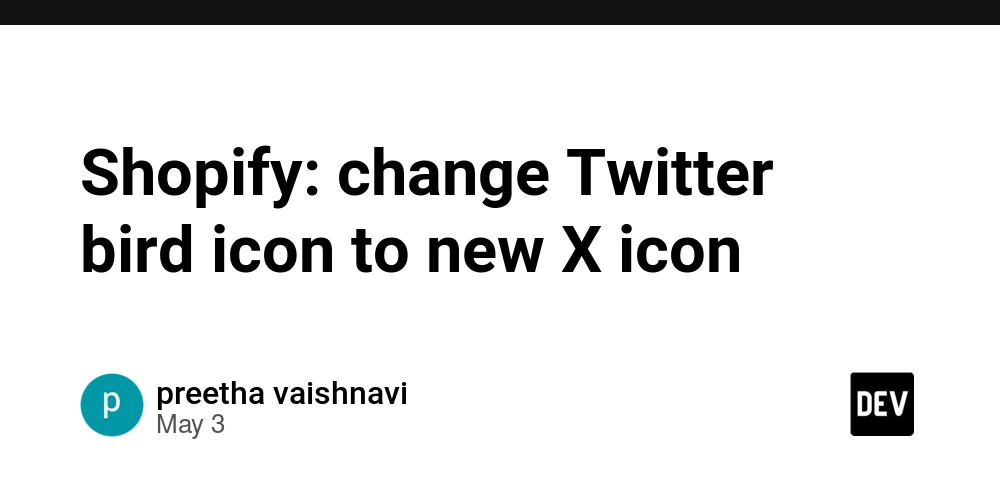
Based on demand, especially from our .NET, and Rider communities, we’re introducing Qodana for C/C++. This advanced linter goes beyond Clang-Tidy to detect critical issues like memory leaks, null dereferences, and uninitialized memory usage to name a few.
The old community-licensed linter that was previously known under this name is now called “Qodana Community for C/C++”.
Why upgrade?
The new C++ paid linter for professional teams:
- Includes MISRA, and Data Flow Analysis for error tracking during value propagation.
- Is a more powerful option than Clang-Tidy for bug detection.
- Has easy integration with Qodana CLI and Docker.
Would you have caught this in a normal code review?


What are DFA inspections?
DFA (or data flow) inspections are based on a more thorough code analysis, such as tracking possible variable states through possible execution paths. Such introspection allows DFA to catch some of the more sneaky errors in your code. For example, these inspections are capable of finding nullptr dereferences, memory leaks, out of bounds memory accesses, and more.
You can try this new linter using Qodana CLI or by manually running the jetbrains/qodana-cpp docker image with a token from Qodana Cloud.
Switching to Kotlin K2 Mode
We’ve enabled K2 mode for qodana-jvm and qodana-jvm-community linters. This update aligns with JetBrains’ move towards K2 in IntelliJ IDEA 2025.1 and offers improved performance and stability, along with support for new Kotlin 2.1 features.
Potential issues to be aware of:
- Third-party plugins might not support K2 yet.
- Some inspections are still being implemented (see details).
Need to switch back?
There are a number of way to do this depending on the way linter is configured. But you could simply set the property “idea.kotlin.plugin.use.k2” to “false” in your linter configuration.
What to do next
If you’re using the latest tag, you don’t need to do anything to enjoy the benefits of our new Qodana 2025.1 release. If not, please change from 2024.4 to 2025.1 to update. Users of GitHub Actions, Azure DevOps, and Circle CI can find the latest version of the extension here.
With these new enhancements, you have greater potential to substantially improve your coding experience. For further information, including detailed setup instructions for each feature, please refer to our official documentation.
We’re continuously improving Qodana to provide better inspections, integrations, and security features. Stay tuned for more updates in upcoming releasesYou can also stay up to date with Qodana by joining our communities on Reddit, LinkedIn, and X.
Other Qodana releases this month
Insights Dashboard
Native Mode
Visual Studio Plugin
SSO
Qodana On-Prem Lite



































































![Apple Developing AI 'Vibe-Coding' Assistant for Xcode With Anthropic [Report]](https://www.iclarified.com/images/news/97200/97200/97200-640.jpg)
![Apple's New Ads Spotlight Apple Watch for Kids [Video]](https://www.iclarified.com/images/news/97197/97197/97197-640.jpg)









































































































_Inge_Johnsson-Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)



























































































































![[The AI Show Episode 145]: OpenAI Releases o3 and o4-mini, AI Is Causing “Quiet Layoffs,” Executive Order on Youth AI Education & GPT-4o’s Controversial Update](https://www.marketingaiinstitute.com/hubfs/ep%20145%20cover.png)


























































































































































![From Art School Drop-out to Microsoft Engineer with Shashi Lo [Podcast #170]](https://cdn.hashnode.com/res/hashnode/image/upload/v1746203291209/439bf16b-c820-4fe8-b69e-94d80533b2df.png?#)