Zoom attack tricks victims into allowing remote access to install malware and steal money
Attachers are luring victims into a Zoom call and then taking over their PC to install malware, infiltrate their accounts, and steal their assets.

Be careful when talking to people you’ve not met with before over the Zoom video conferencing system; you might get more than you bargained for. Two CEOs were recently targeted by a Zoom-based attack. One spotted it in time – and sadly, one did not.
The attack is by a crime group that the Security Alliance call ELUSIVE COMET in a warning about the threat last month. ELUSIVE COMET targets its victims by luring them into a Zoom video call and then taking over their PC to install malware, infiltrate their accounts, and steal their assets.
The group typically approaches victims with a supposed media opportunity to get them interested, and then sets up an introductory Zoom call. During that video meeting, the attacker keeps their screen switched off, but sends a remote control request to the victim.
Remote control is a feature in the Zoom app that allows someone else to take control of your PC. It’s great if, for example, you’re not very tech-savvy and you want your grandchild to fix your computer from the other side of the country. It’s less good if you agree to a remote control request from someone you don’t know – especially if you don’t know you’re doing so.
That’s what happens to victims during their fraudulent call from ELUSIVE COMET. When the remote control request comes through to the victim, the notification says “ Some rushed or distracted people might assume that’s a valid request from the app, perhaps as a precursor to recording a call or displaying new content. If the victim accepts, it’s game over, and the attacker can take full control of the victim’s system.
ELUSIVE COMET tried this trick on the CEO of cybersecurity consulting company Trail of Bits, but it didn’t work on him. After receiving an invitation to appear on “Bloomberg Crypto,” he suspected something was amiss.
The attackers approached him via the X social media network and refused to switch to email when asked. Then they used a third-party booking system called Calendly to arrange the call. While Calendly is a legitimate service, the attackers hadn’t branded their Calendly pages with Bloomberg’s logo, which the CEO felt was suspicious. After checking into some of the data gathered on the group in the Security Alliance advisory, the CEO realized what was happening.
Sadly, that wasn’t the case for Jake Gallen, who owns a cryptocurrency company called Emblem Vault. As he describes in a postmortem thread on X earler this month, he also got a media invitation from an X account, this time called @tacticalinvest_, to appear on a podcast. He took the bait.
“While the interview was ongoing @tacticalinvest_ was downloading malware on my computer known as goopdate,” he reports, “which was powerful enough to steal >$100k in digital assets from my Bitcoin and Ethereum wallets, as well as log into my twitter, gmail, and other accounts.”
Gallen did his due diligence. Before he took the meeting, he did some research and found that the account had a large audience, with a history of consistent posts and videos. There was also a YouTube account. This illustrates just how sneaky some of these attackers can be, and how even tech-savvy people can be duped.
While you might not be a business owner or influencer looking for exposure, it’s worth paying attention to who you let into Zoom meetings, and who you give control of the meeting to. Let’s not also forget that there’s an ongoing trend of people ‘Zoombombing’ by infiltrating others’ meetings.
One of the easiest approaches is to avoid installing Zoom’s app and simply use it in the browser where possible. Running Zoom in the browser limits its functionality, including not allowing remote control of your system. Zoom gives you this option when you attempt to join a meeting without opening the app.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today. Zoom takeovers in action
How to stay safe


































































![Apple Shares New Ad for iPhone 16: 'Trust Issues' [Video]](https://www.iclarified.com/images/news/97125/97125/97125-640.jpg)


![At Least Three iPhone 17 Models to Feature 12GB RAM [Kuo]](https://www.iclarified.com/images/news/97122/97122/97122-640.jpg)













![Hands-on: Motorola’s new trio of Razr phones are beautiful, if familiar vessels for AI [Gallery]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/04/motorola-razr-2025-family-9.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)
![The big yearly Android upgrade doesn’t matter all that much now [Video]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/04/Android-versions-1.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)



![Apple appealing $570M EU fine, White House says it won’t be tolerated [U]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2025/04/Apple-says-570M-EU-fine-is-unfair-White-House-says-it-wont-be-tolerated.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)





















































































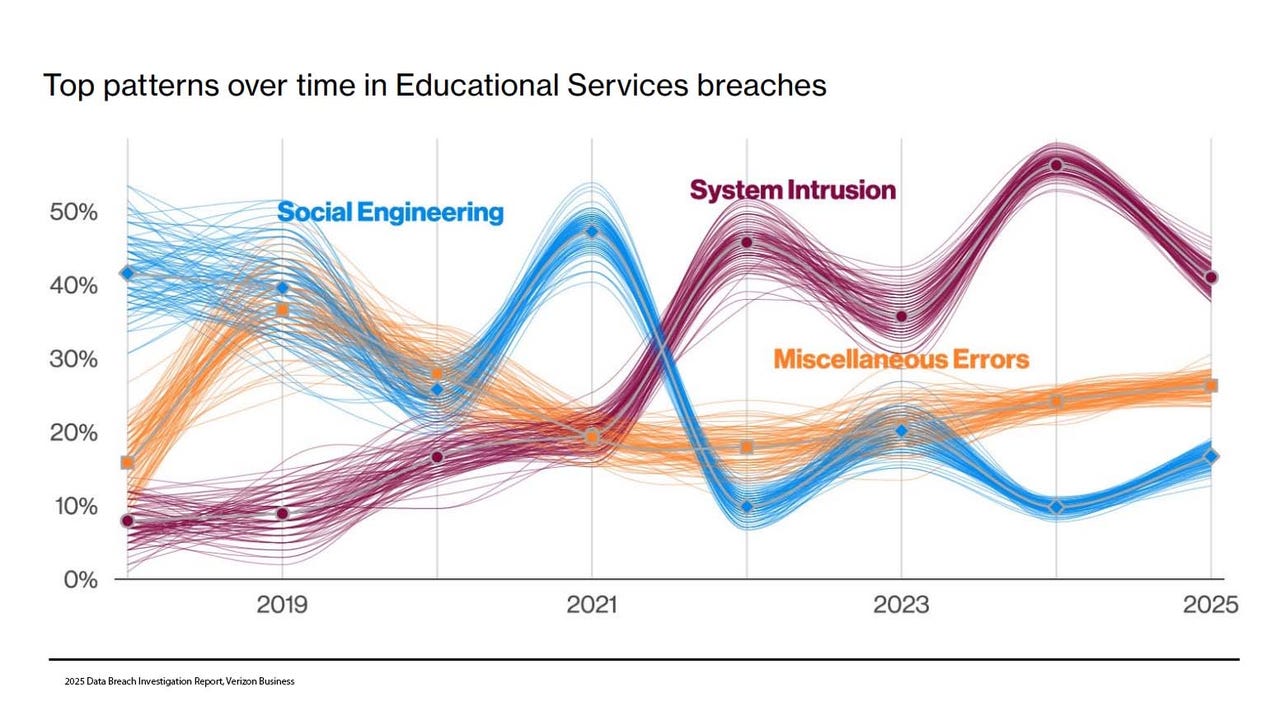
_NicoElNino_Alamy.png?width=1280&auto=webp&quality=80&disable=upscale#)



















































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)














































































































































![[DEALS] Sterling Stock Picker: Lifetime Subscription (85% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)





























































































