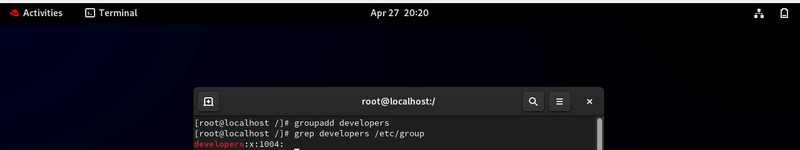
Secure Cookie Best Practices
Secure Cookie Best Practices Introduction: HTTP cookies, while essential for web applications, pose significant security risks if not handled properly. Implementing secure cookie practices is crucial for protecting user data and maintaining application integrity. This article outlines best practices for enhancing cookie security. Prerequisites: Before implementing secure cookies, ensure your server and application support HTTPS. Cookies transmitted over HTTP are easily intercepted. You'll also need to understand the Set-Cookie HTTP header and its various attributes. Features of Secure Cookies: Secure cookies leverage several key features: Secure flag: This crucial flag ensures the cookie is only transmitted over HTTPS. Without it, cookies are vulnerable even on HTTPS sites due to potential downgrade attacks. Example: Set-Cookie: sessionid=value; Secure; HttpOnly flag: This prevents client-side JavaScript from accessing the cookie, mitigating Cross-Site Scripting (XSS) attacks. Example: Set-Cookie: sessionid=value; HttpOnly; SameSite attribute: This attribute controls when cookies are sent with cross-site requests. SameSite=Strict prevents cookies from being sent with cross-site requests, while SameSite=Lax allows cookies to be sent with top-level navigations (like clicking a link) but not with other cross-site requests. SameSite=None requires the Secure attribute and allows cross-site cookies but is less common due to potential security implications. Example: Set-Cookie: sessionid=value; SameSite=Lax; Advantages: Secure cookies significantly reduce the risk of cookie theft, protecting user sessions and sensitive data from unauthorized access. They bolster application security against common web vulnerabilities. Disadvantages: Implementing secure cookies might require additional configuration and testing. The SameSite attribute, while enhancing security, can affect website functionality if not implemented carefully, particularly for third-party integrations. Conclusion: Implementing secure cookies is a non-negotiable aspect of building secure web applications. By utilizing the Secure, HttpOnly, and SameSite attributes appropriately, developers can significantly enhance the security posture of their applications and protect user data from a variety of attacks. Always prioritize security best practices when handling cookies.

Secure Cookie Best Practices
Introduction:
HTTP cookies, while essential for web applications, pose significant security risks if not handled properly. Implementing secure cookie practices is crucial for protecting user data and maintaining application integrity. This article outlines best practices for enhancing cookie security.
Prerequisites:
Before implementing secure cookies, ensure your server and application support HTTPS. Cookies transmitted over HTTP are easily intercepted. You'll also need to understand the Set-Cookie HTTP header and its various attributes.
Features of Secure Cookies:
Secure cookies leverage several key features:
Secureflag: This crucial flag ensures the cookie is only transmitted over HTTPS. Without it, cookies are vulnerable even on HTTPS sites due to potential downgrade attacks. Example:Set-Cookie: sessionid=value; Secure;HttpOnlyflag: This prevents client-side JavaScript from accessing the cookie, mitigating Cross-Site Scripting (XSS) attacks. Example:Set-Cookie: sessionid=value; HttpOnly;SameSiteattribute: This attribute controls when cookies are sent with cross-site requests.SameSite=Strictprevents cookies from being sent with cross-site requests, whileSameSite=Laxallows cookies to be sent with top-level navigations (like clicking a link) but not with other cross-site requests.SameSite=Nonerequires theSecureattribute and allows cross-site cookies but is less common due to potential security implications. Example:Set-Cookie: sessionid=value; SameSite=Lax;
Advantages:
Secure cookies significantly reduce the risk of cookie theft, protecting user sessions and sensitive data from unauthorized access. They bolster application security against common web vulnerabilities.
Disadvantages:
Implementing secure cookies might require additional configuration and testing. The SameSite attribute, while enhancing security, can affect website functionality if not implemented carefully, particularly for third-party integrations.
Conclusion:
Implementing secure cookies is a non-negotiable aspect of building secure web applications. By utilizing the Secure, HttpOnly, and SameSite attributes appropriately, developers can significantly enhance the security posture of their applications and protect user data from a variety of attacks. Always prioritize security best practices when handling cookies.







































































![Apple Developing Battery Case for iPhone 17 Air Amid Battery Life Concerns [Report]](https://www.iclarified.com/images/news/97208/97208/97208-640.jpg)
![Apple to Split iPhone Launches Across Fall and Spring in Major Shakeup [Report]](https://www.iclarified.com/images/news/97211/97211/97211-640.jpg)
![Apple to Move Camera to Top Left, Hide Face ID Under Display in iPhone 18 Pro Redesign [Report]](https://www.iclarified.com/images/news/97212/97212/97212-640.jpg)
![AirPods 4 On Sale for $99 [Lowest Price Ever]](https://www.iclarified.com/images/news/97206/97206/97206-640.jpg)








































































































_Inge_Johnsson-Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)


























































































































![[The AI Show Episode 145]: OpenAI Releases o3 and o4-mini, AI Is Causing “Quiet Layoffs,” Executive Order on Youth AI Education & GPT-4o’s Controversial Update](https://www.marketingaiinstitute.com/hubfs/ep%20145%20cover.png)
















































































































![[DEALS] Microsoft 365: 1-Year Subscription (Family/Up to 6 Users) (23% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)















































![From Art School Drop-out to Microsoft Engineer with Shashi Lo [Podcast #170]](https://cdn.hashnode.com/res/hashnode/image/upload/v1746203291209/439bf16b-c820-4fe8-b69e-94d80533b2df.png?#)