How to Prevent Data Loss in Cloud Storage: A Developer’s Checklist
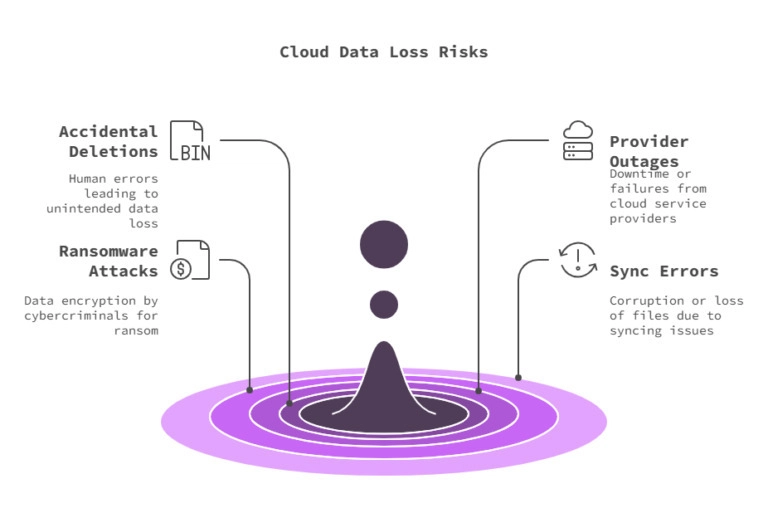
Understanding Cloud Storage Data Loss Risks Cloud storage offers convenience, scalability, and accessibility, but it’s not immune to data loss. Many developers assume that storing data in the cloud is inherently safe, yet without proper backup and security measures, critical files can be lost due to human error, cyberattacks, or provider failures. Why Data Loss Happens in Cloud Storage Even the most reliable cloud storage services can fail. Understanding the main causes of data loss helps developers implement preventive strategies before issues arise. Accidental Deletions and Overwrites Human errors, such as deleting the wrong file or overwriting important data, are among the most common causes of cloud data loss. Many cloud providers do not offer built-in versioning or recovery options unless explicitly configured. Cloud Provider Outages and Failures Even top providers like AWS, Google Cloud, and Microsoft Azure experience downtime or data center failures. Without geo-redundancy or external backups, businesses risk losing access to their critical application data. Ransomware and Cyberattacks Ransomware attacks encrypt cloud-stored files, making them inaccessible unless a ransom is paid. Cybercriminals can also exploit weak authentication or misconfigured access permissions to delete or steal sensitive information. Sync Errors and Corruption Syncing issues between cloud storage and local devices can overwrite valid files with corrupted or outdated versions. If a file is incorrectly synced, it may be lost across all connected devices. The Importance of a Robust Data Protection Strategy To mitigate the risks of data loss in cloud storage, developers must implement a multi-layered data protection strategy that includes: Proactive Backup and Security Measures Automated backups ensure that even if a file is lost or corrupted, a previous version is available for recovery. End-to-end encryption prevents unauthorized access to sensitive files. Compliance with GDPR, HIPAA, and SOC 2 Regulations like GDPR and HIPAA require strict data security, retention, and access control policies. Implementing audit logs, role-based access control (RBAC), and data retention policies ensures compliance with industry standards. Implementing Multi-Layered Protection Versioning and geo-redundancy protect against accidental deletions and provider failures. Zero-knowledge encryption ensures that only authorized users can access cloud-stored data. Real-time monitoring detects suspicious activity or unauthorized access attempts before data is compromised. Understanding these risks is the first step toward building a resilient cloud storage system that safeguards critical data while ensuring compliance and security. Essential Backup Strategies for Developers Data loss in cloud storage can happen due to accidental deletions, cyberattacks, or unexpected service outages. For developers, having a robust backup strategy is essential to ensure that applications remain operational and data remains recoverable. By implementing automated backups, versioning, and geo-redundancy, developers can prevent irreversible data loss and improve disaster recovery. Implementing Automated Backups Manual backups are unreliable and prone to human error. A scheduled, automated backup system ensures that data is continuously protected without requiring developer intervention. Why Automated Backups Are Critical Reduces the risk of permanent data loss by maintaining up-to-date copies of critical files. Protects against accidental deletions, ransomware attacks, and database corruption. Ensures compliance with regulations like GDPR and HIPAA, which require data retention policies. Example: Using ByteHide Storage’s Automatic Backup Feature ByteHide Storage offers built-in automated backups, allowing developers to: Configure scheduled backups without writing complex scripts. Set custom retention policies to ensure compliance with data protection laws. Restore previous versions of files instantly, minimizing downtime in case of data loss. Versioning: Protecting Against Overwrites & Corruption Saving only the latest version of a file can be risky. If a file is accidentally modified, corrupted, or deleted, recovering previous versions becomes impossible without versioning. How Version Control in Cloud Storage Prevents Data Loss Stores multiple versions of a file instead of just the most recent one. Allows developers to rollback changes and restore older versions if needed. Protects against accidental overwrites, data corruption, or malicious edits. Versioning is particularly useful for collaborative development environments, where multiple team members work on the same files and unintended modifications can happen. Geo-Redundant Storage for Disaster Recovery Cloud providers, including industry leaders like AWS and Google Cloud, have
Understanding Cloud Storage Data Loss Risks
Cloud storage offers convenience, scalability, and accessibility, but it’s not immune to data loss. Many developers assume that storing data in the cloud is inherently safe, yet without proper backup and security measures, critical files can be lost due to human error, cyberattacks, or provider failures.
Why Data Loss Happens in Cloud Storage
Even the most reliable cloud storage services can fail. Understanding the main causes of data loss helps developers implement preventive strategies before issues arise.
Accidental Deletions and Overwrites
Human errors, such as deleting the wrong file or overwriting important data, are among the most common causes of cloud data loss.
Many cloud providers do not offer built-in versioning or recovery options unless explicitly configured.Cloud Provider Outages and Failures
Even top providers like AWS, Google Cloud, and Microsoft Azure experience downtime or data center failures.
Without geo-redundancy or external backups, businesses risk losing access to their critical application data.Ransomware and Cyberattacks
Ransomware attacks encrypt cloud-stored files, making them inaccessible unless a ransom is paid.
Cybercriminals can also exploit weak authentication or misconfigured access permissions to delete or steal sensitive information.Sync Errors and Corruption
Syncing issues between cloud storage and local devices can overwrite valid files with corrupted or outdated versions.
If a file is incorrectly synced, it may be lost across all connected devices.
The Importance of a Robust Data Protection Strategy
To mitigate the risks of data loss in cloud storage, developers must implement a multi-layered data protection strategy that includes:
Proactive Backup and Security Measures
Automated backups ensure that even if a file is lost or corrupted, a previous version is available for recovery.
End-to-end encryption prevents unauthorized access to sensitive files.Compliance with GDPR, HIPAA, and SOC 2
Regulations like GDPR and HIPAA require strict data security, retention, and access control policies.
Implementing audit logs, role-based access control (RBAC), and data retention policies ensures compliance with industry standards.Implementing Multi-Layered Protection
Versioning and geo-redundancy protect against accidental deletions and provider failures.
Zero-knowledge encryption ensures that only authorized users can access cloud-stored data.
Real-time monitoring detects suspicious activity or unauthorized access attempts before data is compromised.
Understanding these risks is the first step toward building a resilient cloud storage system that safeguards critical data while ensuring compliance and security.
Essential Backup Strategies for Developers
Data loss in cloud storage can happen due to accidental deletions, cyberattacks, or unexpected service outages. For developers, having a robust backup strategy is essential to ensure that applications remain operational and data remains recoverable. By implementing automated backups, versioning, and geo-redundancy, developers can prevent irreversible data loss and improve disaster recovery.
Implementing Automated Backups
Manual backups are unreliable and prone to human error. A scheduled, automated backup system ensures that data is continuously protected without requiring developer intervention.
Why Automated Backups Are Critical
- Reduces the risk of permanent data loss by maintaining up-to-date copies of critical files.
- Protects against accidental deletions, ransomware attacks, and database corruption.
- Ensures compliance with regulations like GDPR and HIPAA, which require data retention policies.
Example: Using ByteHide Storage’s Automatic Backup Feature
ByteHide Storage offers built-in automated backups, allowing developers to:
- Configure scheduled backups without writing complex scripts.
- Set custom retention policies to ensure compliance with data protection laws.
- Restore previous versions of files instantly, minimizing downtime in case of data loss.
Versioning: Protecting Against Overwrites & Corruption
Saving only the latest version of a file can be risky. If a file is accidentally modified, corrupted, or deleted, recovering previous versions becomes impossible without versioning.
How Version Control in Cloud Storage Prevents Data Loss
- Stores multiple versions of a file instead of just the most recent one.
- Allows developers to rollback changes and restore older versions if needed.
- Protects against accidental overwrites, data corruption, or malicious edits.
Versioning is particularly useful for collaborative development environments, where multiple team members work on the same files and unintended modifications can happen.
Geo-Redundant Storage for Disaster Recovery
Cloud providers, including industry leaders like AWS and Google Cloud, have experienced outages that resulted in data inaccessibility or loss. A geo-redundant storage strategy ensures that data is distributed across multiple locations, reducing the risk of permanent data loss due to a single point of failure.
How Geo-Redundancy Enhances Reliability
- Prevents data loss in case of regional server failures, provider outages, or natural disasters.
- Ensures high availability, allowing data to be accessed even if one data center goes offline.
- Meets compliance requirements for data resilience and disaster recovery planning.
Example: ByteHide Storage’s Geo-Redundant Infrastructure
ByteHide Storage enhances reliability by distributing backups across multiple secure locations. This ensures that:
- Data remains accessible even if one storage location fails.
- Developers can configure multi-region replication for critical backups.
- Applications experience minimal downtime in case of unexpected failures.
By combining automated backups, versioning, and geo-redundancy, developers can create a resilient data protection strategy, ensuring that their applications remain secure, compliant, and prepared for any data loss event.
Securing Cloud Data with Encryption & Access Controls
Storing data in the cloud introduces security risks, especially when dealing with sensitive user information, application logs, or confidential business records. Without strong encryption and strict access controls, data is vulnerable to unauthorized access, breaches, and compliance violations. Implementing end-to-end encryption (E2EE) and role-based access control (RBAC) ensures that only authorized users can access or modify stored data.
End-to-End Encryption to Prevent Unauthorized Access
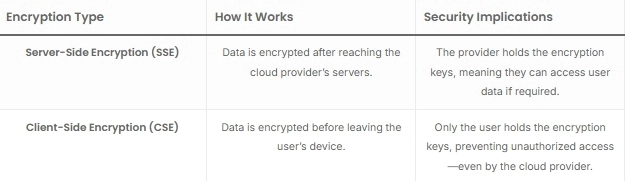
Encryption is the foundation of secure cloud storage. However, not all encryption methods offer the same level of protection. Many cloud providers encrypt data on their servers but still retain control over the encryption keys, meaning they can technically access user files if needed.
Why AES-256 Encryption Is Essential for Secure Cloud Backups
- AES-256 is the gold standard for encryption, used by governments, financial institutions, and security-focused applications.
- Protects cloud-stored data against hacks, insider threats, and unauthorized access attempts.
- Ensures compliance with GDPR, HIPAA, and SOC 2 by securing sensitive information at rest and in transit.
Server-Side Encryption vs. Client-Side Encryption
True zero-knowledge storage relies on client-side encryption, ensuring that only the file owner can decrypt their data. Without this level of security, cloud-stored files remain exposed to potential breaches or third-party access requests.
Role-Based Access Control (RBAC) for Data Protection
Encryption alone is not enough — developers must also control who has access to specific files. RBAC (Role-Based Access Control) is a crucial security measure that limits access based on user roles and permissions.
Limiting Data Access to Authorized Users Only
- Prevents accidental data exposure by ensuring users only see what they need.
- Enforces the principle of least privilege, reducing the risk of insider threats.
- Allows organizations to define different access levels for developers, administrators, and external stakeholders.
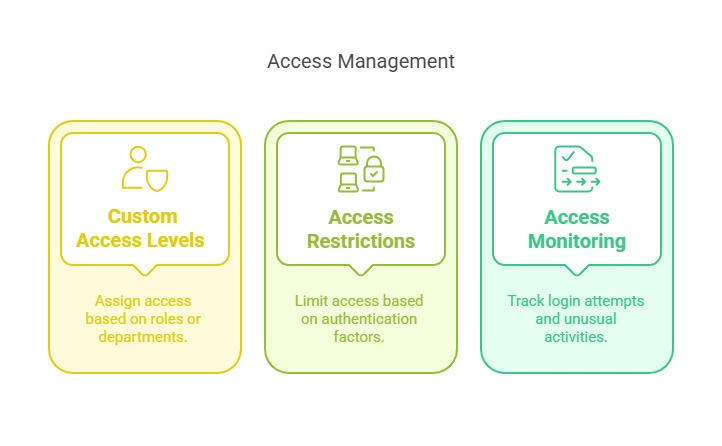
Example: How ByteHide Storage Enforces RBAC Policies
ByteHide Storage includes granular RBAC controls, allowing developers to:
- Assign custom access levels based on roles, departments, or project needs.
- Restrict access to sensitive files based on authentication factors like device or location.
- Monitor access logs to track failed login attempts, permission changes, or unusual activity.
Implementing Proactive Monitoring & Alerts
Preventing data loss in cloud storage isn’t just about backups and encryption — it also requires constant monitoring to detect and respond to potential threats. Without real-time visibility, unauthorized deletions, silent failures, or security breaches can go unnoticed until it’s too late.
By implementing real-time monitoring and automated alerts, developers can proactively identify anomalies, unauthorized access, and unexpected data modifications before they escalate into serious issues.
Setting Up Real-Time Monitoring for Cloud Storage
Effective cloud monitoring relies on log tracking and anomaly detection to detect suspicious activity, failed backup attempts, or unexpected data loss events.
How Log Tracking Prevents Silent Data Loss
- Detects unexpected deletions, failed writes, or access anomalies.
- Provides a detailed audit trail to investigate issues and security incidents.
- Helps ensure compliance with GDPR, HIPAA, and SOC 2 by maintaining detailed records of file operations.
Example: Leveraging ByteHide Storage & ByteHide Logs for Cloud Monitoring
ByteHide Storage includes built-in real-time monitoring, providing:
- Automated security insights to detect unauthorized modifications.
- Integrity checks to ensure that stored files remain unaltered and accessible.
- Audit logs for tracking who accessed or modified files, supporting compliance needs.
For developers needing custom real-time tracking, ByteHide Logs can be integrated to:
- Capture detailed application-level events related to cloud storage interactions.
- Set up custom log-based alerts to track unusual patterns, such as repeated failed access attempts.
- Enhance troubleshooting and security investigations by correlating logs from different systems.
Combining ByteHide Storage’s built-in monitoring with custom tracking from ByteHide Logs provides a comprehensive approach to cloud storage security, ensuring both automated insights and granular event tracking.
Enabling Instant Alerts for Unauthorized Changes
Monitoring alone isn’t enough — developers need real-time alerts to detect and respond to threats as they happen.
How to Detect Unexpected Deletions, Modifications, or Access Attempts
- Set up event-driven notifications to flag abnormal storage activity.
- Configure role-based access alerts to track unauthorized permission changes.
- Use integrity checks to verify that critical files remain unchanged.
Best Tools for Automating Alerts and Responses
- ByteHide Storage’s built-in alerting system automatically notifies developers of critical security events.
- Webhook integrations can trigger external workflows in incident response systems.
- SIEM (Security Information and Event Management) tools, such as Splunk or Datadog, can be used alongside ByteHide Logs for advanced security analytics.
By proactively monitoring cloud storage and setting up real-time alerts, developers can prevent silent data loss, detect security threats faster, and ensure compliance with data protection regulations.
Creating a Disaster Recovery Plan for Cloud Data
No matter how secure a cloud storage system is, data loss can still happen due to system failures, cyberattacks, or accidental deletions. Having a disaster recovery plan (DRP) ensures that developers can quickly restore lost data, minimize downtime, and maintain compliance with industry regulations.
A solid cloud disaster recovery strategy includes regular data restoration tests and compliance-aligned storage practices to protect critical business information.
Testing Data Restoration & Recovery Procedures
Many organizations set up backups but fail to verify if they can successfully restore their data when needed. Regular testing ensures that backups are reliable, accessible, and aligned with business continuity goals.
Why Regular Recovery Drills Are Necessary
- Ensures that backups are functional and can be restored without data corruption.
- Identifies bottlenecks or failures in the restoration process before an actual emergency.
- Helps organizations meet compliance requirements for data retention and disaster recovery planning.
How Developers Can Verify Backup Integrity and Access
- Conduct scheduled recovery tests by restoring files in a sandbox environment.
- Validate backup timestamps, completeness, and data integrity after restoration.
- Use ByteHide Storage’s versioning and backup management tools to restore files efficiently.
- Implement automated validation scripts to compare original and restored data for discrepancies.
By testing data restoration procedures regularly, developers can identify potential failures before they impact production environments.
Ensuring Compliance with Industry Standards
Regulatory frameworks like GDPR, HIPAA, and SOC 2 require businesses to securely store and recover sensitive data. A disaster recovery plan must align with these standards to avoid legal risks and ensure data protection.
Overview of GDPR, HIPAA, and SOC 2 Compliance for Cloud Storage
- GDPR: Requires data encryption, right to be forgotten, and strict access control for personal information.
- HIPAA: Mandates protected health information (PHI) encryption, access logging, and retention policies for healthcare data.
- SOC 2: Focuses on security, availability, and confidentiality in cloud data management, requiring audit trails and disaster recovery plans.
Example: How ByteHide Storage Simplifies Compliance Management
ByteHide Storage offers built-in compliance tools to help developers meet regulatory requirements effortlessly:
- Zero-knowledge encryption ensures that only authorized users can access stored data.
- Automated backup retention policies align with HIPAA’s 7-year storage requirement.
- Granular access controls (RBAC) restrict unauthorized data exposure.
- Audit logs and real-time monitoring track file changes for SOC 2 reporting.
Future-Proofing Cloud Storage with Preventive Measures
Data loss in the cloud isn’t just a possibility — it’s a reality for many businesses that don’t have the right safeguards in place. Whether it’s accidental deletions, cyberattacks, or provider failures, the best way to protect critical data is through proactive security and recovery strategies.
Key Takeaways for Preventing Data Loss
Throughout this guide, we’ve covered essential data loss prevention strategies that every developer should implement:
- Automated backups ensure that lost files can always be restored.
- Versioning protects against accidental overwrites or corruption.
- Geo-redundancy prevents cloud outages from causing permanent data loss.
- End-to-end encryption guarantees that sensitive data stays private.
- Real-time monitoring and alerts help detect unauthorized access before damage is done.
Why Automation Is Key to Secure Cloud Storage
Security isn’t just about preventing breaches — it’s also about reducing human error. Manually managing backups, monitoring access logs, or configuring disaster recovery plans is time-consuming and prone to mistakes. That’s why automation plays a critical role in cloud data protection.
With the right tools, developers can ensure:
✔ Backups run automatically, without the need for manual intervention.
✔ Data remains encrypted at all times, making unauthorized access impossible.
✔ Storage is redundant across
In an era where data breaches and cloud failures are more common than ever, developers need a secure, automated, and reliable cloud storage solution. By integrating ByteHide Storage, businesses can protect their most valuable asset — their data — without added complexity.






































































![Lowest Prices Ever: Apple Pencil Pro Just $79.99, USB-C Pencil Only $49.99 [Deal]](https://www.iclarified.com/images/news/96863/96863/96863-640.jpg)
![Apple Releases iOS 18.4 RC 2 and iPadOS 18.4 RC 2 to Developers [Download]](https://www.iclarified.com/images/news/96860/96860/96860-640.jpg)














![What Google Messages features are rolling out [March 2025]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2023/12/google-messages-name-cover.png?resize=1200%2C628&quality=82&strip=all&ssl=1)








































![Chip Glitching 101 with [Hash]](https://hackaday.com/wp-content/uploads/2025/03/glitching.jpeg?#)


























































































































![[The AI Show Episode 141]: Road to AGI (and Beyond) #1 — The AI Timeline is Accelerating](https://www.marketingaiinstitute.com/hubfs/ep%20141.1.png)
![[The AI Show Episode 140]: New AGI Warnings, OpenAI Suggests Government Policy, Sam Altman Teases Creative Writing Model, Claude Web Search & Apple’s AI Woes](https://www.marketingaiinstitute.com/hubfs/ep%20140%20cover.png)
![[The AI Show Episode 139]: The Government Knows AGI Is Coming, Superintelligence Strategy, OpenAI’s $20,000 Per Month Agents & Top 100 Gen AI Apps](https://www.marketingaiinstitute.com/hubfs/ep%20139%20cover-2.png)

























































































































![From broke musician to working dev. How college drop-out Ryan Furrer taught himself to code [Podcast #166]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743189826063/2080cde4-6fc0-46fb-b98d-b3d59841e8c4.png?#)



![[FREE EBOOKS] The Ultimate Linux Shell Scripting Guide, Artificial Intelligence for Cybersecurity & Four More Best Selling Titles](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)


































.png?#)