Outwitting the Adversarial Edge: Why Endpoint Management Needs an AI Upgrade
Artificial Intelligence (AI) has long been the darling of tech headlines. With all the fanfare, one would assume that businesses have mastered the tools. However, beneath the buzz, AI’s true potential still remains untapped. In 2021, the Identity Theft Resource Center clocked 1,862 data breaches. Today, a jaw-dropping 1.7 billion people have had their personal […] The post Outwitting the Adversarial Edge: Why Endpoint Management Needs an AI Upgrade appeared first on Unite.AI.


Artificial Intelligence (AI) has long been the darling of tech headlines. With all the fanfare, one would assume that businesses have mastered the tools. However, beneath the buzz, AI’s true potential still remains untapped.
In 2021, the Identity Theft Resource Center clocked 1,862 data breaches. Today, a jaw-dropping 1.7 billion people have had their personal data ripped open by cybercriminals operating at machine-gun speed. In short, while companies tinkered with AI as a shiny novelty, the bad guys took it deadly serious.
The mismatch stems from outdated defences. Many organizations continue to limp with legacy tools that cling to outdated notions of trust built for simpler times. Meanwhile, attackers have embraced Generative AI (GenAI) to bypass these defences with fileless malware and polymorphic code that evolves faster than traditional defences can adapt.
As laptops, desktops, smartphones, and IoT devices continue to multiply, the window for vulnerabilities expand. Endpoint management must evolve to meet this escalating challenge, or enterprises risk losing it all.
How GenAI Rescues IT from the Support Abyss
We’ve all been there- the agonizing wait for a customer support technician to untangle a technical mess. With thousands of tickets piling up, IT support teams are stretched thin by sprawling device ecosystems, remote workforces, and relentless cyber threats. Fortunately, with Eliza, a 1960s breakthrough in human-computer dialogue, we’ve leapt from basic scripts to Alexa’s smooth responses and now to GenAI powerhouses like Bard.
Picture this: a user’s firewall settings are botched. In the past, they would log a ticket and wait. Now, a GenAI-powered virtual assistant could diagnose the glitch in seconds and deliver a step-by-step fix. These agents could also guide users through onboarding, clarify policy-based queries, and resolve connectivity hiccups, freeing IT teams for more strategic tasks.
Better yet, instead of wading through dense documentation or decoding jargons, GenAI chatbots help employees tap into company-provided resources to surface precise solutions.
GenAI impact doesn’t stop at user support. For instance, when an endpoint stumbles in terms of failed updates or malicious crashes, GenAI can interpret logs from the organization's unified endpoint management (UEM) solution and cross-reference user reports, allowing an IT admin to resolve the issue. By bridging user assistance and system-level diagnostics, GenAI turns IT from a bottleneck into a strategic asset.
Closing the Endpoint Security Gap with GenAI
Identifying and containing a breach takes, on an average, a staggering 277 days and, weaponized AI has been making it harder to close this gap. While 90% of executives see AI-powered attacks as an escalating storm, one in three organizations still lack a documented strategy for defending against GenAI threats. Worse, adversaries now use AI to camouflage their moves within network traffic, making them harder to detect.
Take Kimsuky (aka Emerald Sleet), for instance. This North-Korean linked threat actor is known for its intricate eight-stage attack chain. The group exploits legitimate cloud services to blend in while leveraging AI for continuous reconnaissance, evasion, and adaptation.
Relying on reactive defences against such sophisticated attacks is turning out to be a losing bet. In a world where adversaries can breach systems in minutes, taking a day to ingest data and another to run a search is a lost battle. The smarter way, as Gartner suggests, is to view AI-enhanced security tools as force multipliers. While seasoned professionals handle nuanced decisions that require business context, allow AI to parse logs, learn from historical data, spot patterns and anticipate trouble before it strikes.
More than its ability to analyze vast datasets, embedding AI into an organization’s endpoint management framework has other advantages. For example, IT admins can ask plain-language questions like, “Which devices haven’t been updated in 90 days?” or “How many endpoints are running outdated antivirus?” The AI embedded within the organization’s UEM platform processes the request, digs through endpoint data, and delivers detailed reports, leaving IT admins to take faster and smarter decisions.
When a device falls out of compliance, perhaps by installing an unauthorized application, GenAI can analyze the context and recommend the best course of action executable via the UEM. This reduces the time between issue identification and resolution, ensuring endpoints remain compliant, secure and operational. Beyond individual incidences, AI solves compliance challenges by continuously monitoring and aligning the entire device fleet with regulatory standards- be it GDPR, HIPAA or any industry-specific mandates.
To outwit the adversarial edge, organizations ought to opt for defensive AI. Rather than overloading endpoints with agents or piling authentication layers on users, organizations need a strategic layout that weaves AI into their cybersecurity stack.
GenAI-Powered Automation: Revolutionizing Scripting and Beyond
For years, IT teams have leaned on scripts to automate repetitive tasks, ensure consistent deployments, minimize slip-ups and streamline workflows. Yet, even for professional coders, writing and fine-tuning scripts to manage endpoints can be a slog.
GenAI has eliminated these barriers with a bold leap into no-code automation. Instead of manually working on scripts, IT admins can now simply generate, say, a PowerShell script to deploy the latest patch and the solution spits a ready-to-run code in seconds. Paired with a UEM solution, IT admins could run the script effortlessly across thousands of devices. Tools like Hexnode Genie take it a step further by letting admins generate, validate, tweak or request a version tailored for diverse fleets.
Beyond automation, GenAI has been making its way into the domains of Zero Trust frameworks. While Zero Trust demands relentless verification of every access request, GenAI rises to the challenge, actively scanning, probing, and neutralizing threats in real-time. Advanced security platforms now weave Endpoint Detection and Response (EDR), Extended Detection and Response (XDR), and identity protection into a unified, AI-driven shield. When a suspicious login pings from an endpoint, GenAI doesn’t just flag it; it cross-references network data, assesses risk, and triggers a lockdown if needed.
The takeaway is clear: cobbled-up solutions aren’t sufficient to defend against threats designed to outmanoeuvre static defences. In this escalating AI arms race, clinging to yesterday’s defences isn’t just a gamble; it’s a blueprint for defeat. Enterprises must embrace AI as a companion to their traditional solutions. Sooner, endpoint management will become an autonomous entity in the IT ecosystem, detecting and mitigating evolving threats before they lead to a full-on breach.
The post Outwitting the Adversarial Edge: Why Endpoint Management Needs an AI Upgrade appeared first on Unite.AI.





























































![Apple to Craft Key Foldable iPhone Components From Liquid Metal [Kuo]](https://www.iclarified.com/images/news/96784/96784/96784-640.jpg)

![Apple to Focus on Battery Life and Power Efficiency in Future Premium Devices [Rumor]](https://www.iclarified.com/images/news/96781/96781/96781-640.jpg)







































































































_Federico_Caputo_Alamy.jpg?#)


































































![[The AI Show Episode 139]: The Government Knows AGI Is Coming, Superintelligence Strategy, OpenAI’s $20,000 Per Month Agents & Top 100 Gen AI Apps](https://www.marketingaiinstitute.com/hubfs/ep%20139%20cover-2.png)


![[The AI Show Episode 138]: Introducing GPT-4.5, Claude 3.7 Sonnet, Alexa+, Deep Research Now in ChatGPT Plus & How AI Is Disrupting Writing](https://www.marketingaiinstitute.com/hubfs/ep%20138%20cover.png)








































































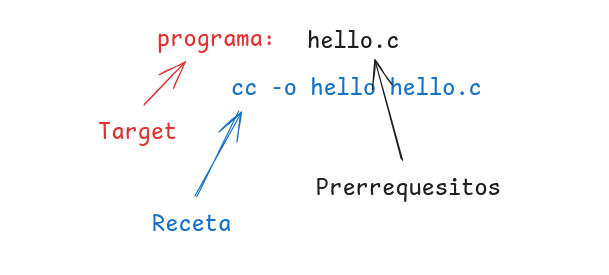































![From hating coding to programming satellites at age 37 with Francesco Ciulla [Podcast #165]](https://cdn.hashnode.com/res/hashnode/image/upload/v1742585568977/09b25b8e-8c92-4f4b-853f-64b7f7915980.png?#)






























.jpg?width=1920&height=1920&fit=bounds&quality=80&format=jpg&auto=webp#)





.png?#)