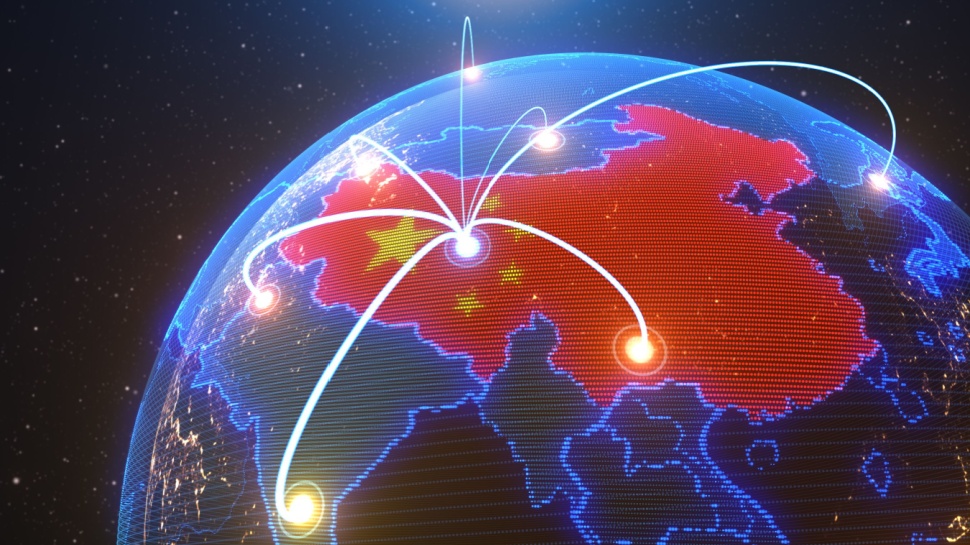
Dangerous new CoffeeLoader malware executes on your GPU to get past security tools
A new loader was spotted sporting some creative solutions to remain hidden.

- Security researchers Zscaler found a new loader used in different infostealing campaigns
- CoffeeLoader uses multiple tricks to bypass security and drop additional payloads
- Interestingly enough, it executes the code on the system’s GPU
Security researchers have found a dangerous new malware loader that can evade traditional endpoint detection and response (EDR) solutions in a clever and concerning way.
Researchers from Zscaler ThreatLabz said they recently observed CoffeeLoader in the wild, describing it as a “sophisticated” malware loader.
For detection evasion, CoffeeLoader uses a number of features, including call stack spoofing, sleep obfuscation, and the use of Windows fibers, the researchers said. Call stacks can be described as a digital breadcrumb trail that records which functions a program has called. Security tools can use call stacks to track program behavior, and detect suspicious activity. CoffeeLoader, however, hides its tracks by forging a fake breadcrumb trail.

Monitor your credit score with TransUnion starting at $29.95/month
TransUnion is a credit monitoring service that helps you stay on top of your financial health. With real-time alerts, credit score tracking, and identity theft protection, it ensures you never miss important changes. You'll benefit from a customizable online interface with clear insights into your credit profile. Businesses also benefit from TransUnion’s advanced risk assessment tools.
Preferred partner (What does this mean?)View Deal
Armoury
A malware loader’s task usually is to infiltrate a system and execute or download additional malware, such as ransomware or spyware. It acts as the initial infection stage, often evading detection by security tools before deploying the main payload.
Sleep obfuscation makes the malware’s code and data encrypted while the tool is in a sleep state - therefore, the malware’s unencrypted artifacts are present in memory only when the code is being executed.
Zscaler describes Windows fibers as an “obscure and lightweight mechanism for implementing user-mode multitasking.”
Fibers allow a single threat to have multiple execution contexts (fibers), which the application can switch between, manually. CoffeeLoader uses Windows fibers to implement sleep obfuscation.
But perhaps the most concerning aspect of the loader is Armoury, a packer that executes the code on the system’s GPU, hindering analysis in virtual environments.
“After the GPU executes the function, the decoded output buffer contains self-modifying shellcode, which is then passed back to the CPU to decrypt and execute the underlying malware,” the researchers explained.
“ThreatLabz has observed this packer used to protect both SmokeLoader and CoffeeLoader payloads.”
The researchers said they saw CoffeeLoader being used to deploy Rhadamanthys shellcode, meaning it is deployed in infostealing campaigns.
You might also like
- One of the most powerful ransomware hacks around has been cracked using some serious GPU power
- We've rounded up the best password managers
- Take a look at our guide to the best authenticator app





































































![Apple's M5 iPad Pro Enters Advanced Testing for 2025 Launch [Gurman]](https://www.iclarified.com/images/news/96865/96865/96865-640.jpg)
![M5 MacBook Pro Set for Late 2025, Major Redesign Waits Until 2026 [Gurman]](https://www.iclarified.com/images/news/96868/96868/96868-640.jpg)
![Apple to Revamp Health App with AI-Powered Doctor [Gurman]](https://www.iclarified.com/images/news/96870/96870/96870-640.jpg)
![Lowest Prices Ever: Apple Pencil Pro Just $79.99, USB-C Pencil Only $49.99 [Deal]](https://www.iclarified.com/images/news/96863/96863/96863-640.jpg)













![What Google Messages features are rolling out [March 2025]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2023/12/google-messages-name-cover.png?resize=1200%2C628&quality=82&strip=all&ssl=1)







































![Chip Glitching 101 with [Hash]](https://hackaday.com/wp-content/uploads/2025/03/glitching.jpeg?#)

























































































































![[The AI Show Episode 141]: Road to AGI (and Beyond) #1 — The AI Timeline is Accelerating](https://www.marketingaiinstitute.com/hubfs/ep%20141.1.png)
![[The AI Show Episode 140]: New AGI Warnings, OpenAI Suggests Government Policy, Sam Altman Teases Creative Writing Model, Claude Web Search & Apple’s AI Woes](https://www.marketingaiinstitute.com/hubfs/ep%20140%20cover.png)
![[The AI Show Episode 139]: The Government Knows AGI Is Coming, Superintelligence Strategy, OpenAI’s $20,000 Per Month Agents & Top 100 Gen AI Apps](https://www.marketingaiinstitute.com/hubfs/ep%20139%20cover-2.png)

























































































































![From broke musician to working dev. How college drop-out Ryan Furrer taught himself to code [Podcast #166]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743189826063/2080cde4-6fc0-46fb-b98d-b3d59841e8c4.png?#)



![[FREE EBOOKS] The Ultimate Linux Shell Scripting Guide, Artificial Intelligence for Cybersecurity & Four More Best Selling Titles](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)


































.png?#)