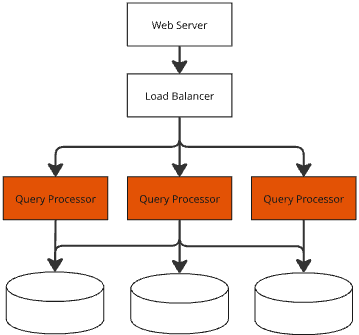
GorillaBot Attacks Windows Devices With 300,000+ Attack Commands Across 100+ Countries
A new botnet named “GorillaBot,” has orchestrated over 300,000 attack commands across more than 100 countries within a span of just three weeks. Built on the infamous Mirai botnet framework, GorillaBot represents a sophisticated malware evolution. It leverages advanced encryption and evasion techniques to target industries ranging from telecommunications to finance and education. Discovered by […] The post GorillaBot Attacks Windows Devices With 300,000+ Attack Commands Across 100+ Countries appeared first on Cyber Security News.

A new botnet named “GorillaBot,” has orchestrated over 300,000 attack commands across more than 100 countries within a span of just three weeks.
Built on the infamous Mirai botnet framework, GorillaBot represents a sophisticated malware evolution. It leverages advanced encryption and evasion techniques to target industries ranging from telecommunications to finance and education.
Discovered by the NSFOCUS Global Threat Hunting team, GorillaBot’s activity was tracked between September 4 and September 27, during which it executed its massive wave of attacks.
The malware has been designed to hijack vulnerable devices globally, turning them into tools for distributed denial-of-service (DDoS) attacks and other malicious activities.
Its capacity to penetrate various sectors has triggered concerns among cybersecurity professionals, leading to immediate demands for countermeasures. ANY.RUN’s interactive sandbox provides multiple benefits for in-depth malware analysis.
Unlike its predecessor, Mirai, GorillaBot incorporates custom encryption algorithms and anti-debugging measures, making it significantly harder to detect and analyze.
Mohamed Talaat’s analysis with ANY. RUN explains that these enhancements allow it to evade traditional security measures while maintaining robust communication with its command-and-control (C2) servers.
View analysis in ANY.RUN’s Interactive Sandbox
How GorillaBot Operates
GorillaBot’s operation begins with its infection of devices through vulnerabilities in Internet of Things (IoT) systems or other poorly secured endpoints. Once compromised, the malware establishes communication with its C2 server using raw TCP sockets.
This communication is secured using a custom XTEA-like cipher, which encrypts and decrypts data exchanged between the botnet and its controllers.
The malware also employs an advanced authentication mechanism involving the generation of a unique SHA-256-based token. This ensures that only legitimate bot instances can interact with the C2 infrastructure, effectively preventing unauthorized access.
Once authenticated, GorillaBot receives encoded attack commands that are decrypted and parsed for execution. These commands direct the botnet to launch targeted attacks against specific systems or networks.
Learn more about evasion malware’s ability to process both simple and complex attack instructions, which mirrors the functionality of Mirai but with added sophistication.
GorillaBot’s creators have incorporated multiple layers of evasion techniques to avoid detection. Before initiating its primary operations, the malware performs checks to identify whether it is running in a virtualized or containerized environment, often used by researchers for analysis. For instance:
- It examines system-level artifacts like the
/procfile system to determine if it is operating on a legitimate machine. - It searches for Kubernetes-related indicators such as “kubepods” in
/proc/1/cgroupfiles. If such markers are found, the malware terminates itself immediately.
Additionally, GorillaBot uses anti-debugging measures such as inspecting the TracerPid field in /proc/self/status to detect if debugging tools are monitoring it. The malware exits without executing its payload if any suspicious activity is detected.
By introducing new encryption methods and evasion tactics, attackers have demonstrated how older malware can be revitalized into formidable tools for cybercrime.
ANY.RUN emphasizes the importance of proactive defense strategies to combat threats like GorillaBot. Organizations are urged to:
- Regularly patch vulnerabilities in IoT devices and other networked systems.
- Deploy advanced intrusion detection systems capable of identifying encrypted C2 communications.
- Utilize sandboxing tools such as ANY.RUN for real-time malware behavior analysis.
As GorillaBot continues its global rampage, the need for coordinated international efforts to tackle botnets has never been more critical. With over 300,000 attacks already launched across more than 100 countries.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
The post GorillaBot Attacks Windows Devices With 300,000+ Attack Commands Across 100+ Countries appeared first on Cyber Security News.



































































![Apple's M5 iPad Pro Enters Advanced Testing for 2025 Launch [Gurman]](https://www.iclarified.com/images/news/96865/96865/96865-640.jpg)
![M5 MacBook Pro Set for Late 2025, Major Redesign Waits Until 2026 [Gurman]](https://www.iclarified.com/images/news/96868/96868/96868-640.jpg)
![Apple to Revamp Health App with AI-Powered Doctor [Gurman]](https://www.iclarified.com/images/news/96870/96870/96870-640.jpg)
![Lowest Prices Ever: Apple Pencil Pro Just $79.99, USB-C Pencil Only $49.99 [Deal]](https://www.iclarified.com/images/news/96863/96863/96863-640.jpg)













![What Google Messages features are rolling out [March 2025]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2023/12/google-messages-name-cover.png?resize=1200%2C628&quality=82&strip=all&ssl=1)






































![Chip Glitching 101 with [Hash]](https://hackaday.com/wp-content/uploads/2025/03/glitching.jpeg?#)
























































































































![[The AI Show Episode 141]: Road to AGI (and Beyond) #1 — The AI Timeline is Accelerating](https://www.marketingaiinstitute.com/hubfs/ep%20141.1.png)
![[The AI Show Episode 140]: New AGI Warnings, OpenAI Suggests Government Policy, Sam Altman Teases Creative Writing Model, Claude Web Search & Apple’s AI Woes](https://www.marketingaiinstitute.com/hubfs/ep%20140%20cover.png)
![[The AI Show Episode 139]: The Government Knows AGI Is Coming, Superintelligence Strategy, OpenAI’s $20,000 Per Month Agents & Top 100 Gen AI Apps](https://www.marketingaiinstitute.com/hubfs/ep%20139%20cover-2.png)

























































































































![From broke musician to working dev. How college drop-out Ryan Furrer taught himself to code [Podcast #166]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743189826063/2080cde4-6fc0-46fb-b98d-b3d59841e8c4.png?#)



![[FREE EBOOKS] The Ultimate Linux Shell Scripting Guide, Artificial Intelligence for Cybersecurity & Four More Best Selling Titles](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)



































.png?#)



















































