Cloning Premier League’s Pirate Site DMCA Subpoena Toolkit
A Premier League DMCA subpoena requires Cloudflare to hand over the details of individuals behind 38 pirate streaming sites. Before that process could even begin, the Premier League needed to obtain certain information about the pirate sites to support its claims. Today we'll attempt to recreate the toolkit used to gather that information and, if all goes to plan, it won't cost a single penny, From: TF, for the latest news on copyright battles, piracy and more.

 Most prevalent in the movie and TV show sectors, applications for DMCA subpoenas are regularly filed at courts in the United States.
Most prevalent in the movie and TV show sectors, applications for DMCA subpoenas are regularly filed at courts in the United States.
Aside from their intended purpose, DMCA subpoenas can provide useful clues about future anti-piracy strategies. When subpoenas are contested by intermediaries, subpoena applications sometimes become copyright cases in their own right. From a rightsholders’ perspective, in some cases they may be the only potential source of information yet to be exhausted.
Getting Prepared
A few days ago, the UK’s Premier League asked a California federal court to issue a DMCA subpoena against Cloudflare. The application identifies 38 target pirate streaming sites, many of which utilize multiple domains. Since the platforms all use Cloudflare, the Premier League hopes that information held by the company will help to unmask the sites’ currently anonymous operators.
Before filing an application under Section 512(h) of the DMCA, which allows copyright owners to obtain a subpoena and receive “information sufficient to identify an anonymous infringer,” applicants are first required to send DMCA takedown notices to the platform in question. The notices should identify the infringing content and state where the content can be found; in cases involving streaming sites, the right tools can prove helpful.
Recreating the Toolkit
The screenshot below shows a live match playing on a pirate streaming site. Culled from the Premier League’s application, it provides clues that allow us to start identifying the tools in use and the problems they’re likely to solve once combined with Open Source Intelligence (OSINT).
At a basic level in this context, OSINT can be almost any information made available on the internet. The screenshot is our primary source; it will help us identify the tools to recreate the toolkit, which in turn will use other public information sources to satisfy the requirements of the application.
M3U8 Sniffer
 In this example it appears that when the Premier League visited the website sporttuna.pro, they were redirected to sporttuna.website and then to sporttuna.xyz (boxed in red).
In this example it appears that when the Premier League visited the website sporttuna.pro, they were redirected to sporttuna.website and then to sporttuna.xyz (boxed in red).
Like most pirate sites, the ‘backend link’ or source of the stream (boxed in green) isn’t on public display. These links can be obtained in various ways but in this case, Chrome extension M3U8 Sniffer is the weapon of choice.
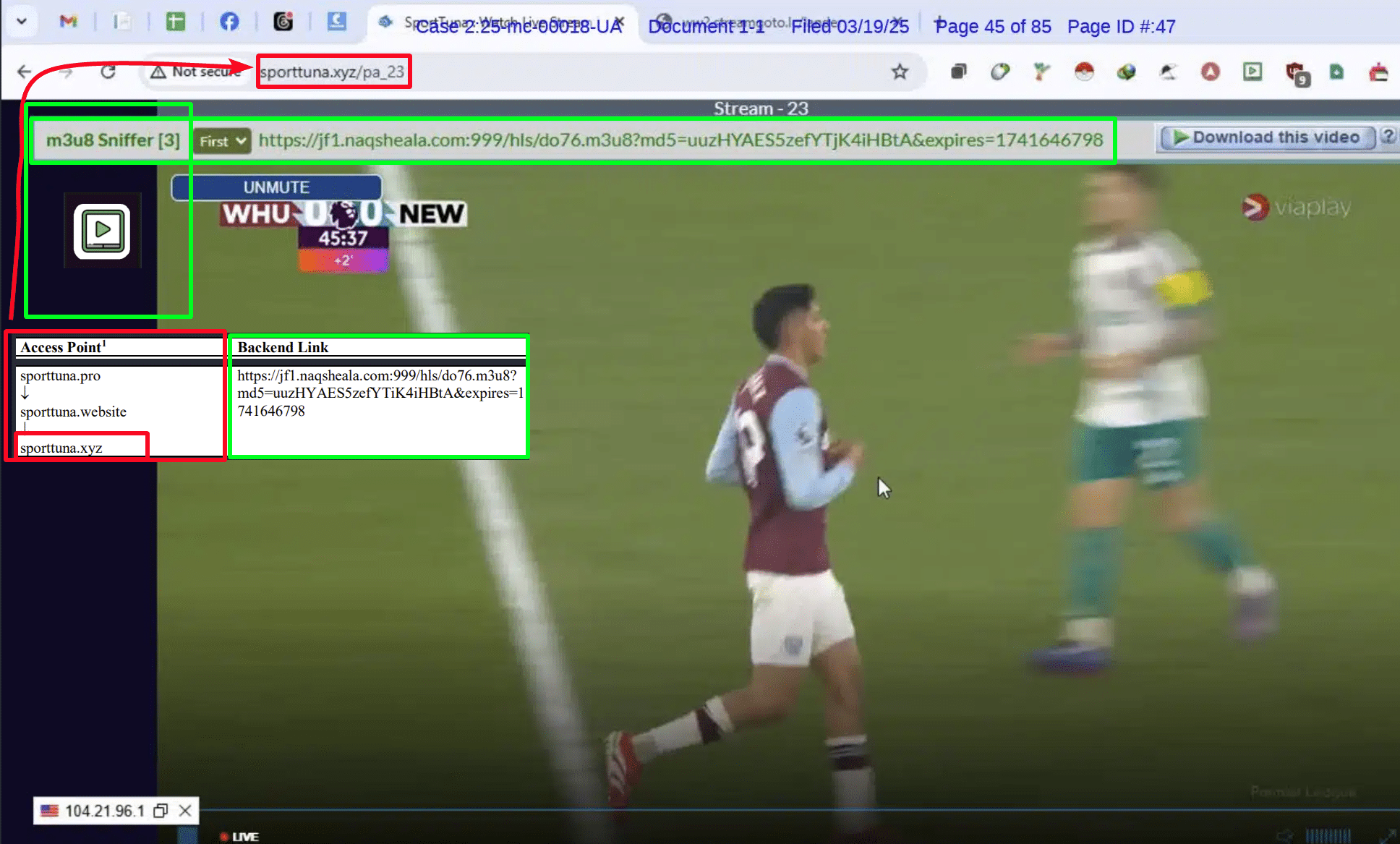
From the developer’s website: The extension intercepts visited web page’s network requests and identifies all m3u8 video stream URLs. When a m3u8 URL request is found, it is displayed in a box that overlays the visited web page (see images above) from which you can copy the m3u8 URL or play the video stream. Also, you can open the extension’s popup window to view the first and last m3u8 URLs found for each site, as well as to set a variety of extension options.
M3U8 Sniffer is a free extension available from the Chrome Web Store. Further information is available from the developer at SnifferTV.com.
Identifying the Remaining Tools
 Identifying the remaining tools was a little time-consuming but if we said the method was advanced or complicated, that would be a lie.
Identifying the remaining tools was a little time-consuming but if we said the method was advanced or complicated, that would be a lie.
We simply trawled through the browser evidence images and took screenshots of the toolbars. These contain the icons of the apps used to obtain the evidence.
After extracting the toolbar icons we put those we recognized to the side, then identified the remainder using reverse image search tools. Straightforward options include Google Images and Google Lens.
As an alternative, Chrome extension RevEye Reverse Image Search provides instant results from Google, Bing, Yandex, and TinEye.
(Note: Bad extensions exist, trust nobody, check the source)
Internet Download Manager
 Given that M3U8 Sniffer “does NOT provide functionality to download the actual video streams” another piece of software comes in handy. IDM is a popular choice in the niche and appears to be the downloader of choice in this particular toolkit.
Given that M3U8 Sniffer “does NOT provide functionality to download the actual video streams” another piece of software comes in handy. IDM is a popular choice in the niche and appears to be the downloader of choice in this particular toolkit.
From the official website: When you click on a download link in a browser, IDM will take over the download and accelerate it. You don’t need to do anything special, just browse the Internet as you usually do. IDM will catch your downloads and accelerate them. IDM supports HTTP, FTP, HTTPS and MMS protocols.
Unfortunately, IDM isn’t free but it is free to try via a 30-day trial. Some prefer JDownloader since the price is more predictable, but there are plenty of options in this niche.
Fiddler
 Our best guess at identifying this next tool comes with a small caveat that its icon was almost impossibly blurred and even when fresh it’s still pretty basic. Ultimately, a green diamond and a single white ‘F’ works here.
Our best guess at identifying this next tool comes with a small caveat that its icon was almost impossibly blurred and even when fresh it’s still pretty basic. Ultimately, a green diamond and a single white ‘F’ works here.
Fiddler and tools with similar functionality (web debugging proxy tools) are used extensively by developers and investigators when keeping a close eye on HTTP traffic is a must. For those who’ve never cared to take a closer look, it can be real eye-opener. Even the most innocuous websites can behave pretty badly until users notice, so there’s never a bad time to take a first look.
Fiddler Classic and Fiddler Everywhere are both available as free trials, and the same is true for Charles Proxy which appears regularly as evidence in Indian site-blocking cases.
Some prefer to monitor traffic with Wireshark but for others it can be too much. Open source and available on Linux, Windows (GUI), and macOS, MITM Proxy will scratch most itches for free.
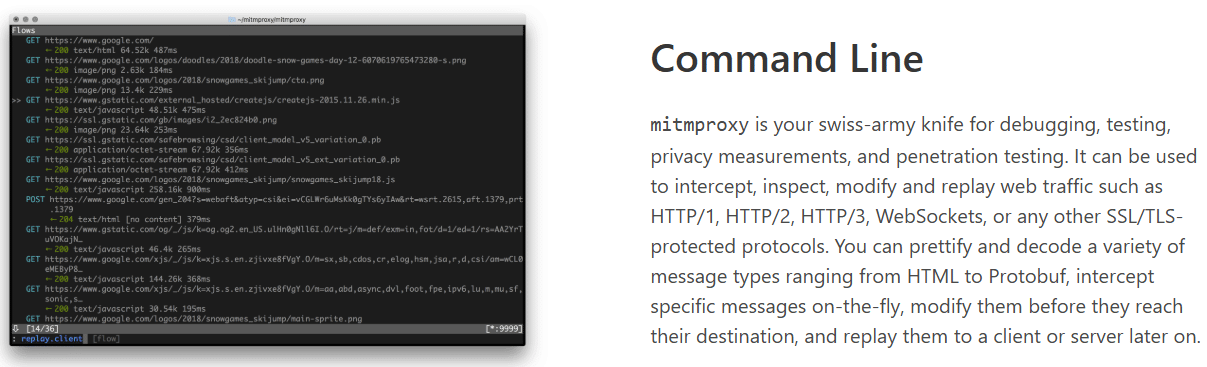
At a pocket friendly price of $0.00, the open source MITM Proxy (man-in-the-middle) does exactly as its name suggests, making it a popular choice.
Instant Datascraper
 Scraping data from websites in a structured and usable format isn’t always easy and for big jobs, things can quickly descend into a time-wasting nightmare.
Scraping data from websites in a structured and usable format isn’t always easy and for big jobs, things can quickly descend into a time-wasting nightmare.
Instant Data Scraper hopes to eliminate the frustrations often associated with scraping and with over a million users, people seem happy with the results.
It’s impossible to say how the Premier League uses Instant Datascraper, but it could easily consume a visible members’ list in an instant or scrape a mountain of forum posts. The options are only limited by data becoming unavailable.
From the official site: Instant Data Scraper is an automated data extraction tool for any website. It uses AI to predict which data is most relevant on a HTML page and allows saving it to Excel or CSV file (XLS, XLSX, CSV). This tool does not require website specific scripts, instead it uses heuristic AI analysis of HTML structure to detect data for extraction. This means that our scraping method works just as well with small and lesser known websites, as it does with global giants like Amazon. Also, our users do not need to have any coding, json or xml skills
The software is free and available direct from webrobots.io and the Chrome Store.
IPNetInfo | Investigator
IPNetInfo describes itself a small utility that allows people to easily find all available information about an IP address. That includes the owner of the IP address and sundry other details. Hosted on Nirsoft.com and GitHub respectively, both also have a bit more to offer.
Investigator is actually a collection of useful tools, one of which is bound to come in useful sooner or later. Developed by Nirsoft, IPNetInfo is surrounded by dozens of other useful free tools at Nirsoft.net so still worth a quick visit.
Those with access to a Linux command line also have access to the best tools when investigating domains, IP addresses, and DNS. For Windows users or those who simply prefer the convenience of GUIs, the following perform well and look great too: Digger Tools, DNSViz, URLQuery, DMNSApp, URLScan, and WebCheck.
Finally, a pair of outliers to consider.
The End: Emulators
 Given that there are Android emulators that are less elaborate, more predictable, and therefore better suited to the assumed job in hand, the discovery of two fairly elaborate emulators in the toolkit initially seems a little puzzling.
Given that there are Android emulators that are less elaborate, more predictable, and therefore better suited to the assumed job in hand, the discovery of two fairly elaborate emulators in the toolkit initially seems a little puzzling.
There’s bound to be a good reason they’re installed but right now, those reasons will have to wait until another day.
Of course, the answers to these questions and others like them, are always out there. ‘Out there’ is a very, very big place but the answers usually give themselves up quite quickly once curiosity arrives.
From: TF, for the latest news on copyright battles, piracy and more.

_Igor_Mojzes_Alamy.jpg?#)































































![Apple Considers Delaying Smart Home Hub Until 2026 [Gurman]](https://www.iclarified.com/images/news/96946/96946/96946-640.jpg)
![Tariffs Threaten Apple's $999 iPhone Price Point in the U.S. [Gurman]](https://www.iclarified.com/images/news/96943/96943/96943-640.jpg)
![iPhone 17 Pro Won't Feature Two-Toned Back [Gurman]](https://www.iclarified.com/images/news/96944/96944/96944-640.jpg)




































































































.webp?#)
.webp?#)
.webp?#)













































































![[The AI Show Episode 142]: ChatGPT’s New Image Generator, Studio Ghibli Craze and Backlash, Gemini 2.5, OpenAI Academy, 4o Updates, Vibe Marketing & xAI Acquires X](https://www.marketingaiinstitute.com/hubfs/ep%20142%20cover.png)
































































































































![From drop-out to software architect with Jason Lengstorf [Podcast #167]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743796461357/f3d19cd7-e6f5-4d7c-8bfc-eb974bc8da68.png?#)




![[DEALS] The Premium Learn to Code Certification Bundle (97% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)























-Mario-Kart-World-Hands-On-Preview-Is-It-Good-00-08-36.jpg?width=1920&height=1920&fit=bounds&quality=80&format=jpg&auto=webp#)

(1).jpg?width=1920&height=1920&fit=bounds&quality=80&format=jpg&auto=webp#)








.png?#)


















































![Emulation Console Update Bakes in Instant Free [Pirated] Game Downloads](https://torrentfreak.com/images/anbernic.png)




