Critical pgAdmin Vulnerability Let Attackers Execute Remote Code
A critical security vulnerability discovered in pgAdmin 4, the most widely used management tool for PostgreSQL databases, is allowing attackers to execute arbitrary code on affected systems. Security researchers have disclosed details of CVE-2025-2945, a severe Remote Code Execution (RCE) vulnerability with a CVSS score of 9.9, indicating the highest level of severity. The vulnerability […] The post Critical pgAdmin Vulnerability Let Attackers Execute Remote Code appeared first on Cyber Security News.
.webp?#)
A critical security vulnerability discovered in pgAdmin 4, the most widely used management tool for PostgreSQL databases, is allowing attackers to execute arbitrary code on affected systems.
Security researchers have disclosed details of CVE-2025-2945, a severe Remote Code Execution (RCE) vulnerability with a CVSS score of 9.9, indicating the highest level of severity.
The vulnerability affects all versions of pgAdmin 4 prior to 9.2, which was released on April 4, 2025. The security flaw exists in two separate POST endpoints: /sqleditor/query_tool/download and /cloud/deploy.
Both endpoints contain dangerous implementations that pass untrusted user input directly to Python’s eval() function without proper validation or sanitization.
The Centre for Cybersecurity Belgium (CCB) issued an urgent advisory on April 4, warning that exploitation could lead to “data breaches, system compromise, and operational downtime impacting confidentiality, integrity, and availability of critical businesses.”
pgAdmin Vulnerability Details
In the /sqleditor/query_tool/download/ This implementation allows attackers to send malicious Python code that will be executed on the server. For example, a simple malicious request could look like:
Similarly, in the /cloud/deploy endpoint, the high_availability parameter is directly passed to eval():
This allows attackers to craft malicious requests that can execute arbitrary code on the server, potentially leading to complete system compromise.
The summary of the vulnerability is given below:
Security experts have confirmed that successful exploitation requires authentication, but once achieved, attackers can:
Alongside the RCE vulnerability, researchers also identified CVE-2025-2946, a Cross-Site Scripting (XSS) vulnerability with a CVSS score of 9.1.
This flaw allows attackers to inject arbitrary HTML and JavaScript through query result rendering in both the Query Tool and View/Edit Data features.
The pgAdmin development team has released version 9.2, which removes the dangerous use of eval() functions and implements proper input validation.
The patch was released within 24 hours of the vulnerability being reported.
The CCB strongly recommends organizations to:
“While patching appliances or software to the newest version may provide safety from future exploitation, it does not remediate historic compromise,” warns the CCB.
Organizations using pgAdmin four are urged to check for signs of compromise and report any security incidents to their respective cybersecurity authorities.
The post Critical pgAdmin Vulnerability Let Attackers Execute Remote Code appeared first on Cyber Security News. Risk Factors Details Affected Products pgAdmin 4 versions prior to 9.2, including Query Tool and Cloud Deployment modules. Impact Remote Code Execution (RCE) Exploit Prerequisites Low-privileged authenticated access- Ability to send crafted POST requests to vulnerable endpoints (/sqleditor/query_tool/download and /cloud/deploy) CVSS 3.1 Score 9.9 (Critical) Impact and Exploitation
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try 50 Request for Free

_Igor_Mojzes_Alamy.jpg?#)
































































![Apple Considers Delaying Smart Home Hub Until 2026 [Gurman]](https://www.iclarified.com/images/news/96946/96946/96946-640.jpg)
![Tariffs Threaten Apple's $999 iPhone Price Point in the U.S. [Gurman]](https://www.iclarified.com/images/news/96943/96943/96943-640.jpg)
![iPhone 17 Pro Won't Feature Two-Toned Back [Gurman]](https://www.iclarified.com/images/news/96944/96944/96944-640.jpg)




































































































.webp?#)
.webp?#)













































































![[The AI Show Episode 142]: ChatGPT’s New Image Generator, Studio Ghibli Craze and Backlash, Gemini 2.5, OpenAI Academy, 4o Updates, Vibe Marketing & xAI Acquires X](https://www.marketingaiinstitute.com/hubfs/ep%20142%20cover.png)
































































































































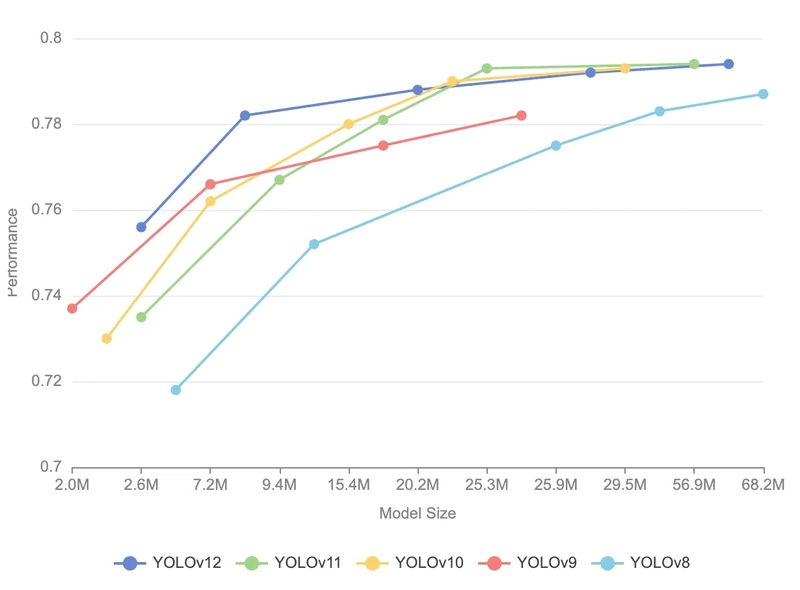
![From drop-out to software architect with Jason Lengstorf [Podcast #167]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743796461357/f3d19cd7-e6f5-4d7c-8bfc-eb974bc8da68.png?#)




![[DEALS] The Premium Learn to Code Certification Bundle (97% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)























-Mario-Kart-World-Hands-On-Preview-Is-It-Good-00-08-36.jpg?width=1920&height=1920&fit=bounds&quality=80&format=jpg&auto=webp#)

(1).jpg?width=1920&height=1920&fit=bounds&quality=80&format=jpg&auto=webp#)








.png?#)