From Watchtowers to Wristbands: Modernizing Fortress Surveillance with AI and IoT
In a world where vigilance once meant sleepless nights and eyes fixed on distant horizons, the cost of human surveillance has always been high—both in energy and in error. Picture a group of knights in chainmail, their swords drawn as they scan the forested border of their stone stronghold. Each shift demands unwavering attention, and a single moment of distraction could allow a threat to slip through. The Modern Solution: AI-Powered Surveillance Meets IoT Sensing Even today, many operations—military or otherwise—still rely heavily on manual monitoring. Whether guarding a perimeter, protecting infrastructure, or maintaining a watch in remote areas, the reliance on human eyes and ears introduces delays, fatigue, and blind spots. And when an alert is missed, the consequences can be immediate and severe. What if the burden of eternal vigilance could be handed off to a smarter, faster, always-on system? By integrating AI-enabled surveillance cameras with a distributed IoT sensor network, we can transform a fortress (or any secure facility) into a proactive, intelligent sentinel. Here’s how: 1. Perimeter Awareness with Smart Sensors Strategically deploy IoT cameras, infrared sensors, and motion/vibration detectors around the perimeter—embedded in stone walls, hidden among trees, or placed along riverbanks. These devices form a resilient network, constantly monitoring for environmental anomalies. Recommended Tech Stack: Raspberry Pi 4 + Coral USB Accelerator for on-edge AI inference The Coral USB Accelerator is a USB device that provides the Edge TPU as a coprocessor for a computer. By connecting it to a Linux host computer, it accelerates the inference of machine learning models. The Edge TPU is a small ASIC (Application-Specific Integrated Circuit) designed by Google to provide high-performance ML inference for low-power devices. Combining the Coral USB Accelerator with a Raspberry Pi primarily allows for the acceleration of machine learning model inference processing. While the Raspberry Pi is a small, low-power computer, its computational capabilities are limited. The Coral USB Accelerator, equipped with the Google-designed dedicated ASIC called the Edge TPU, can be connected to the Raspberry Pi to perform machine learning inference, especially for TensorFlow Lite models, efficiently and at high speed. PIR (Passive Infrared) Sensors for heat signatures LoRaWAN modules (e.g., RAKwireless) for long-range, low-power sensor communication IP-rated outdoor camera modules with night vision and motion detection 2. Real-Time Threat Detection with AI When motion, heat, or sound is detected, AI jumps into action. Using computer vision models trained on distinguishing humans from animals, the system analyzes live footage and classifies the threat: Is it a person or wildlife? Is the individual armed? Are there multiple figures approaching? Recommended Services & Tools: YOLOv8 for real-time object detection YOLOv8:Deep Learning Algorithms for Object Detection Amazon Rekognition or Google Vision AI for image analysis (if using cloud-based processing) TensorFlow Lite for edge deployment 3. Smart Alerts to Wearable Devices Once a threat is confirmed, alerts are instantly transmitted to soldiers or guards equipped with smart badges, armband wearables, or even AR-enabled visors. A visual + haptic notification ensures nothing is missed—even in high-noise environments. Example Hardware: Nordic nRF52-based wearable with Bluetooth Low Energy Raspberry Pi Zero W for custom wrist devices Vuzix AR smart glasses for tactical visual feedback The wearable may display: A holographic minimap showing enemy location Threat level estimation Suggested defensive actions or fallback points 4. Centralized Dashboard for Command Units At the heart of the system sits a command dashboard—an interactive control panel accessible via tablet or secure terminal. It aggregates all sensor data, flags high-risk events, and maintains logs for forensic review. Dashboard Stack: Grafana or Kibana for visualization MQTT broker (e.g., Mosquitto) for device communication AWS IoT Core for cloud integration Conclusion: From Sword to Signal By augmenting medieval-style defense systems with modern AI and IoT, we can reduce the cost of constant human vigilance while vastly improving reaction speed and decision-making. This blend of chainmail and circuitry, stone and signal, shows us that the future of security lies not in more eyes on the wall—but in smarter, more connected ones.

In a world where vigilance once meant sleepless nights and eyes fixed on distant horizons, the cost of human surveillance has always been high—both in energy and in error. Picture a group of knights in chainmail, their swords drawn as they scan the forested border of their stone stronghold. Each shift demands unwavering attention, and a single moment of distraction could allow a threat to slip through.
The Modern Solution: AI-Powered Surveillance Meets IoT Sensing

Even today, many operations—military or otherwise—still rely heavily on manual monitoring. Whether guarding a perimeter, protecting infrastructure, or maintaining a watch in remote areas, the reliance on human eyes and ears introduces delays, fatigue, and blind spots. And when an alert is missed, the consequences can be immediate and severe.
What if the burden of eternal vigilance could be handed off to a smarter, faster, always-on system? By integrating AI-enabled surveillance cameras with a distributed IoT sensor network, we can transform a fortress (or any secure facility) into a proactive, intelligent sentinel.
Here’s how:
1. Perimeter Awareness with Smart Sensors
Strategically deploy IoT cameras, infrared sensors, and motion/vibration detectors around the perimeter—embedded in stone walls, hidden among trees, or placed along riverbanks. These devices form a resilient network, constantly monitoring for environmental anomalies.
Recommended Tech Stack:
-
Raspberry Pi 4 + Coral USB Accelerator for on-edge AI inference
- The Coral USB Accelerator is a USB device that provides the Edge TPU as a coprocessor for a computer. By connecting it to a Linux host computer, it accelerates the inference of machine learning models.
- The Edge TPU is a small ASIC (Application-Specific Integrated Circuit) designed by Google to provide high-performance ML inference for low-power devices.
- Combining the Coral USB Accelerator with a Raspberry Pi primarily allows for the acceleration of machine learning model inference processing. While the Raspberry Pi is a small, low-power computer, its computational capabilities are limited. The Coral USB Accelerator, equipped with the Google-designed dedicated ASIC called the Edge TPU, can be connected to the Raspberry Pi to perform machine learning inference, especially for TensorFlow Lite models, efficiently and at high speed.
- PIR (Passive Infrared) Sensors for heat signatures
- LoRaWAN modules (e.g., RAKwireless) for long-range, low-power sensor communication
- IP-rated outdoor camera modules with night vision and motion detection
2. Real-Time Threat Detection with AI
When motion, heat, or sound is detected, AI jumps into action. Using computer vision models trained on distinguishing humans from animals, the system analyzes live footage and classifies the threat:
- Is it a person or wildlife?
- Is the individual armed?
- Are there multiple figures approaching?
Recommended Services & Tools:
-
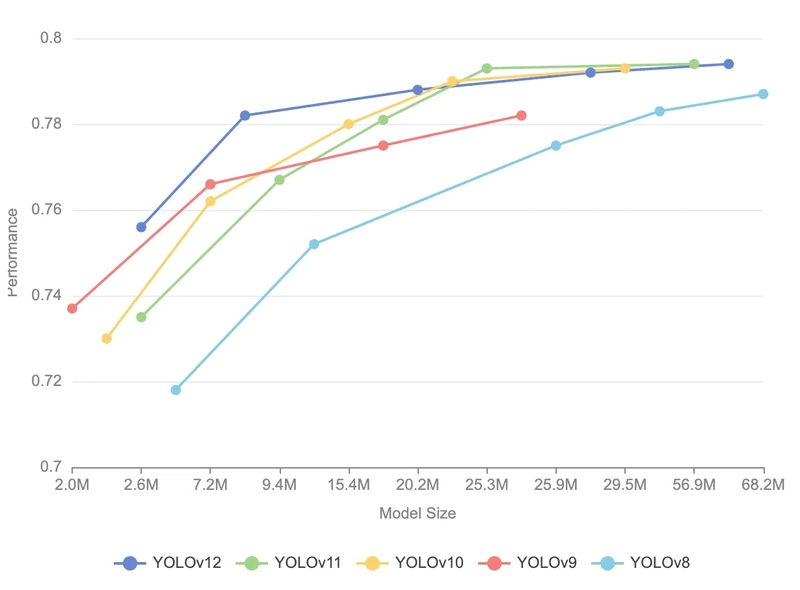
YOLOv8 for real-time object detection
- YOLOv8:Deep Learning Algorithms for Object Detection
- Amazon Rekognition or Google Vision AI for image analysis (if using cloud-based processing)
- TensorFlow Lite for edge deployment
3. Smart Alerts to Wearable Devices
Once a threat is confirmed, alerts are instantly transmitted to soldiers or guards equipped with smart badges, armband wearables, or even AR-enabled visors. A visual + haptic notification ensures nothing is missed—even in high-noise environments.
Example Hardware:
- Nordic nRF52-based wearable with Bluetooth Low Energy
- Raspberry Pi Zero W for custom wrist devices
- Vuzix AR smart glasses for tactical visual feedback
The wearable may display:
- A holographic minimap showing enemy location
- Threat level estimation
- Suggested defensive actions or fallback points
4. Centralized Dashboard for Command Units
At the heart of the system sits a command dashboard—an interactive control panel accessible via tablet or secure terminal. It aggregates all sensor data, flags high-risk events, and maintains logs for forensic review.
Dashboard Stack:
- Grafana or Kibana for visualization
- MQTT broker (e.g., Mosquitto) for device communication
- AWS IoT Core for cloud integration
Conclusion: From Sword to Signal
By augmenting medieval-style defense systems with modern AI and IoT, we can reduce the cost of constant human vigilance while vastly improving reaction speed and decision-making. This blend of chainmail and circuitry, stone and signal, shows us that the future of security lies not in more eyes on the wall—but in smarter, more connected ones.

_Igor_Mojzes_Alamy.jpg?#)
































































![Apple Considers Delaying Smart Home Hub Until 2026 [Gurman]](https://www.iclarified.com/images/news/96946/96946/96946-640.jpg)
![Tariffs Threaten Apple's $999 iPhone Price Point in the U.S. [Gurman]](https://www.iclarified.com/images/news/96943/96943/96943-640.jpg)
![iPhone 17 Pro Won't Feature Two-Toned Back [Gurman]](https://www.iclarified.com/images/news/96944/96944/96944-640.jpg)




































































































.webp?#)
.webp?#)
.webp?#)













































































![[The AI Show Episode 142]: ChatGPT’s New Image Generator, Studio Ghibli Craze and Backlash, Gemini 2.5, OpenAI Academy, 4o Updates, Vibe Marketing & xAI Acquires X](https://www.marketingaiinstitute.com/hubfs/ep%20142%20cover.png)
































































































































![From drop-out to software architect with Jason Lengstorf [Podcast #167]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743796461357/f3d19cd7-e6f5-4d7c-8bfc-eb974bc8da68.png?#)




![[DEALS] The Premium Learn to Code Certification Bundle (97% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)























-Mario-Kart-World-Hands-On-Preview-Is-It-Good-00-08-36.jpg?width=1920&height=1920&fit=bounds&quality=80&format=jpg&auto=webp#)

(1).jpg?width=1920&height=1920&fit=bounds&quality=80&format=jpg&auto=webp#)








.png?#)