Enterprise Networks Unveiled: A Software Engineer's Guide to the Basics (Part 5)
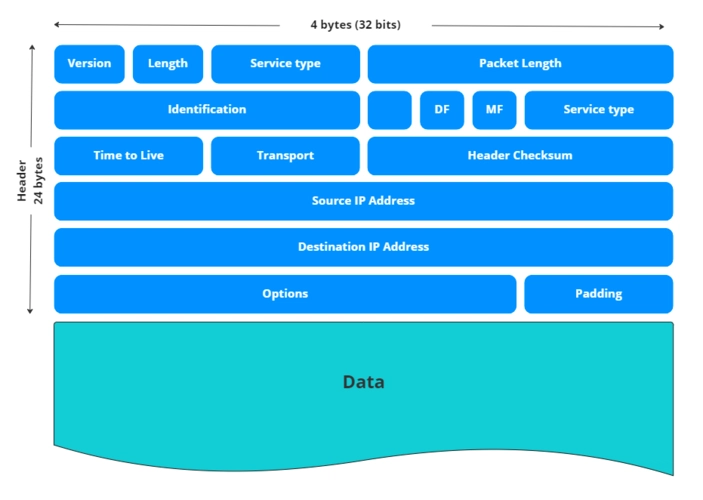
Now that we have a basis of knowledge on network design, it is time to revisit the IPv4 protocol and how it factors into network design. Recall that in Part Two we walked through the TCP/IP stack and learned about the structure of packets at the IP layer. In this post we'll explore this layer in more depth and understand how IP addresses allocation impacts network design. IP Addresses and Binary As shown in the image above (sourced from here), IPv4 addresses are 32 bits long. They consist of 4 octets (a collection of 8 bits), split by periods. Each octet can represent a value of 0-255. That is all the possible combinations of each bit being set to zero or 1. For example, considering the following binary (octet) string "00000010" would be equivalent to "2" because The 2's place bit is set to true while all others are false. Binary operates in base 2 vs base 10 (also known as decimal) that most people are used to working with normally. Working our way from right to left, each place is a power of 2 (similar to decimal, where were go from 1 to 10 to 100) as shown in the image below (sourced from here) With our octet (8 bits), the left most bit when enabled would represent 128(2^7). Moving to the right the next bit would be 64, then 32, then 16, then 8, then 4, then 2, and finally 1. With all bits enabled, we would get the maximum value (by adding all the above together) of 255. When considering the full 32 bits, this allows for roughly 4.3 billion unique IPv4 addresses. IPv6 was also created to address the potential exhaustion of IPv4 addresses. IPv6 uses 128 bits, allowing for a massive amount of address. However, it's adoption has been slow with limited support amongst various tooling. Private vs Public As computing grew in popularity, there came a desire to have private networks rather than everything being accessible to any other device on the internet. We saw an example of this in the last post where private connectivity was established between the multiple sites. What IP addresses should be used in these private networks to ensure we don't overlap with public services at certain IP addresses? Request for comments (RFC) number 1918 from the Internet Engineering Task Force (IETF) directed another governing body, Internet Assigned Numbers Authority (IANA), to reserve a collection of IPv4 addresses for private networks. The IPv4 protocol was also create by the IETF via the RFC process. IANA oversees the allocation of IP addresses globally, delegating to regional authorities like the American Registry for Internet Numbers (ARIN). The allocated private IPv4 ranges from RFC 1918 included: 10.0.0.0 – 10.255.255.255 (16,777,216 addresses) 172.16.0.0 – 172.31.255.255 (1,048,576 addresses) 192.168.0.0 – 192.168.255.255 (65,536 addresses) In 2012, one more network was also reserved for specific a use case relating to large scale internet service provider deployments: 100.64.0.0 – 100.127.255.255 (4,194,304 addresses) In large enterprises you will most often see the 10.x.x.x block used, due to the high upper limit of unique addresses. If you look at your home network, it may be using an address from the 192.168.x.x space (less devices to handle). Network Notation These networks can also be notated by which bits can change to represent devices vs which are static. The full 10.x.x.x block can be noted as 10.0.0.0/8 which indicates that the first 8 bits are static while the other 24 can change. Most home networks may use a smaller block of the 192.168.x.x, such as 192.168.1.0/24. In this case 24 bits are static, and 8 bits are allowed to change. This slash notation is known as CIDR notation which is short for "Classless Inter-domain Routing". This replaced the Classful approach which was less flexible. Within networking devices, CIDR notation can also be represented with what is known as a subnet mask, which can be efficiently stored as another 32 bits. For example, with our 192.168.1.0/24 network, the subnet mask would be 255.255.255.0. In the subnet mask (e.g., 255.255.255.0), the bits set to '1' correspond to the static network portion of the IP address, while the bits set to '0' represent the host portion that can change. Subnets What is a subnet anyways? Subnets are simply dividing the larger network into smaller components. Rather than allocating millions of IP addresses to a specific site that we know will never have more than 1000 devices, we can split apart the larger IP block. For example, our 192.168.1.0/24 could be a subnet of the full reserved range of 192.168.0.0/16. Similarly, a network of 10.0.1.0/24 could be a subnet of 10.0.0.0/8. Subnetting is not limited to the octet boundaries. For example, the network 192.168.1.0/24 could be split into two /25 networks, or 4 /26 networks. Each bit added or removed, halves or doubles the number of IP addresses respectively. A /24 network would have 254 (256-2) usable IP addresses. One address is s
Now that we have a basis of knowledge on network design, it is time to revisit the IPv4 protocol and how it factors into network design. Recall that in Part Two we walked through the TCP/IP stack and learned about the structure of packets at the IP layer. In this post we'll explore this layer in more depth and understand how IP addresses allocation impacts network design.
IP Addresses and Binary
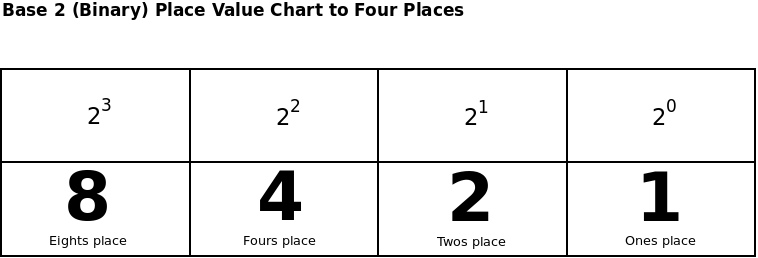
As shown in the image above (sourced from here), IPv4 addresses are 32 bits long. They consist of 4 octets (a collection of 8 bits), split by periods. Each octet can represent a value of 0-255. That is all the possible combinations of each bit being set to zero or 1. For example, considering the following binary (octet) string "00000010" would be equivalent to "2" because The 2's place bit is set to true while all others are false. Binary operates in base 2 vs base 10 (also known as decimal) that most people are used to working with normally. Working our way from right to left, each place is a power of 2 (similar to decimal, where were go from 1 to 10 to 100) as shown in the image below (sourced from here)
With our octet (8 bits), the left most bit when enabled would represent 128(2^7). Moving to the right the next bit would be 64, then 32, then 16, then 8, then 4, then 2, and finally 1. With all bits enabled, we would get the maximum value (by adding all the above together) of 255. When considering the full 32 bits, this allows for roughly 4.3 billion unique IPv4 addresses. IPv6 was also created to address the potential exhaustion of IPv4 addresses. IPv6 uses 128 bits, allowing for a massive amount of address. However, it's adoption has been slow with limited support amongst various tooling.
Private vs Public
As computing grew in popularity, there came a desire to have private networks rather than everything being accessible to any other device on the internet. We saw an example of this in the last post where private connectivity was established between the multiple sites.
What IP addresses should be used in these private networks to ensure we don't overlap with public services at certain IP addresses? Request for comments (RFC) number 1918 from the Internet Engineering Task Force (IETF) directed another governing body, Internet Assigned Numbers Authority (IANA), to reserve a collection of IPv4 addresses for private networks. The IPv4 protocol was also create by the IETF via the RFC process. IANA oversees the allocation of IP addresses globally, delegating to regional authorities like the American Registry for Internet Numbers (ARIN).
The allocated private IPv4 ranges from RFC 1918 included:
- 10.0.0.0 – 10.255.255.255 (16,777,216 addresses)
- 172.16.0.0 – 172.31.255.255 (1,048,576 addresses)
- 192.168.0.0 – 192.168.255.255 (65,536 addresses)
In 2012, one more network was also reserved for specific a use case relating to large scale internet service provider deployments:
- 100.64.0.0 – 100.127.255.255 (4,194,304 addresses)
In large enterprises you will most often see the 10.x.x.x block used, due to the high upper limit of unique addresses. If you look at your home network, it may be using an address from the 192.168.x.x space (less devices to handle).
Network Notation
These networks can also be notated by which bits can change to represent devices vs which are static. The full 10.x.x.x block can be noted as 10.0.0.0/8 which indicates that the first 8 bits are static while the other 24 can change. Most home networks may use a smaller block of the 192.168.x.x, such as 192.168.1.0/24. In this case 24 bits are static, and 8 bits are allowed to change. This slash notation is known as CIDR notation which is short for "Classless Inter-domain Routing". This replaced the Classful approach which was less flexible.
Within networking devices, CIDR notation can also be represented with what is known as a subnet mask, which can be efficiently stored as another 32 bits. For example, with our 192.168.1.0/24 network, the subnet mask would be 255.255.255.0. In the subnet mask (e.g., 255.255.255.0), the bits set to '1' correspond to the static network portion of the IP address, while the bits set to '0' represent the host portion that can change.
Subnets
What is a subnet anyways? Subnets are simply dividing the larger network into smaller components. Rather than allocating millions of IP addresses to a specific site that we know will never have more than 1000 devices, we can split apart the larger IP block. For example, our 192.168.1.0/24 could be a subnet of the full reserved range of 192.168.0.0/16. Similarly, a network of 10.0.1.0/24 could be a subnet of 10.0.0.0/8.
Subnetting is not limited to the octet boundaries. For example, the network 192.168.1.0/24 could be split into two /25 networks, or 4 /26 networks. Each bit added or removed, halves or doubles the number of IP addresses respectively. A /24 network would have 254 (256-2) usable IP addresses. One address is saved for the network address which network devices use to refer to the network, and one for broadcast address which enables send packets to all devices on the same network. A /25 network would have 126 (128-2) usable addresses, and a /26 would have 62 (64-2). Not all subnets have to be the same size, but they must not overlap. The systems which help manage the allocation of addresses are known as IP Addresses Management (IPAM) tools.
Summary Networks
At scale, summary networks, also known as route summarization, can help keep routing processing efficient. Rather than randomly allocating subnets, a larger block can be reserved for a site and then sub divided into more subnets. Recall in the third post that routers leverage IP information to decide where to send packets next. Route tables typically consist of a list of networks (summary or network address) a device knows about and which next hop it should direct traffic to that is bound for that destination network.
Revisiting our Enterprise Network
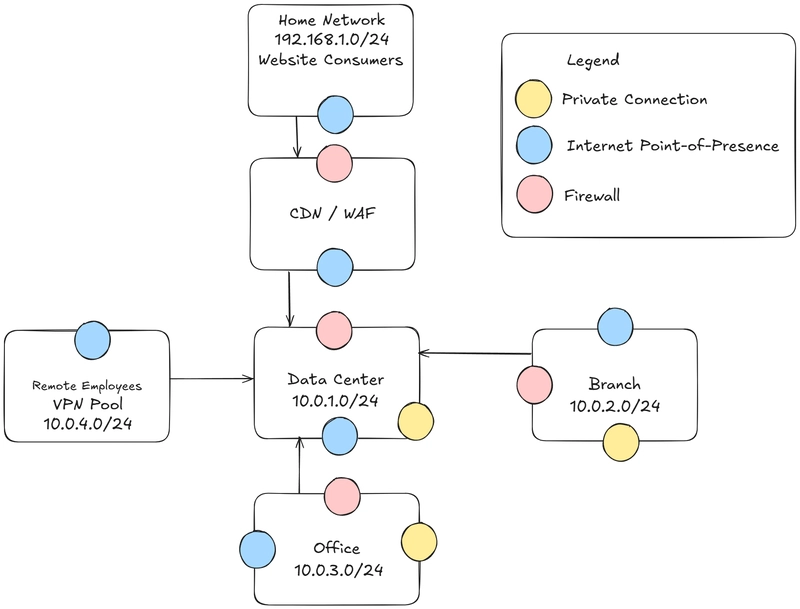
Let's apply the above knowledge to the architecture we discussed in our last post. Using the 10.0.0.0/8 reserved space, we've allocated subnets for the various sites
When a device in a branch needs to communicate with one in the data center, The routers it will encounter will share which networks they know about with each other. Once the request makes it to the first router, it will know which connection it needs to follow to move towards the 10.0.1.0/24 summary network. In this case that would be the private connectivity link. This approach would scale well even if we subnet-ed the 10.0.1.0/24 network into multiple subnets to account for different uses within the data center.
Network Address Translation
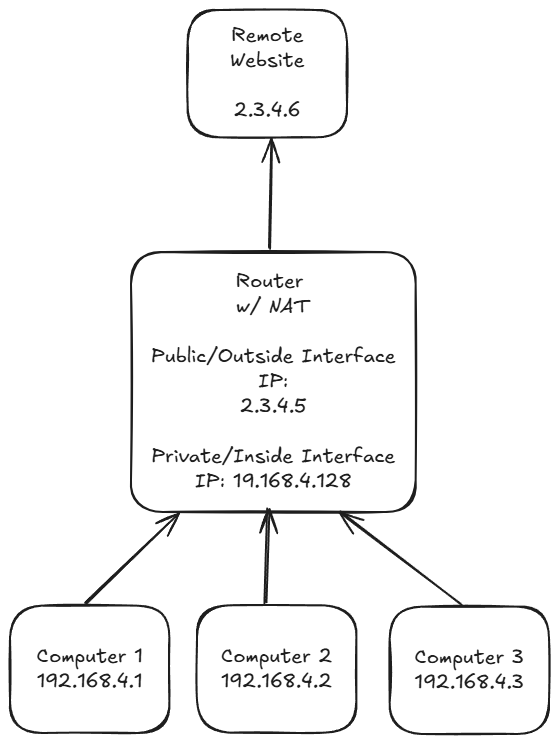
What happens when a device with a private IP address needs to communicate with one on the internet (web browsing, public APIs, etc)? A technique called Network Address Translation or NAT is used. The most common type of NAT you will encounter is a one-to-many NAT. Your home network is typically allocated one public IP address from the pool that your internet service provider owns (A Google search of "what's my ip" will show what IP address the site sees you as). Your router handles the NAT-ing process of the various devices on your network and the requests they make. The router keeps the state of each connection, so it knows how to handle the response from the website or API you are interacting with.
NAT-ing modifies the IP packet with the public/outside IP as the source on the request and re-introduces the private/inside IP for the response as the destination. One-to-many NATs are what allows different companies/home networks to all use the same private IP ranges without it causing conflicts since they each have unique public IP addresses.
If we again consider our enterprise network, each internet point of presence would have its own public IP, and provide similar functionality as shown above for acting as a one-to-many NAT to the internet.
Although it is most commonly used for private to internet communications, NAT-ing can also be used inside a private network. One-to-one NAT-ing may be used when there are two large existing networks are brought together (may occur during an acquisition). One-to-many may also be used, but it may impact network security effectiveness as all devices behind (inside) the NAT would inherit the access of the outside IP address of the NAT. A firewall rule with that outside IP address, would allow all inside IP addresses to access the service at the destination specified in the rule.
Building on the fundamentals you've learned from this and previous posts, we'll take a look at virtualization and container networking in the next post. This will include a look at both local development environments and orchestration platforms such as Kubernetes.
Key Takeaways
- IPv4 addresses are 32 bits long, consisting of four 8-bit octets separated by periods.
- Each octet can have a decimal value between 0 and 255, which corresponds to all possible combinations of its 8 binary bits.
- Private IPv4 address ranges are reserved for internal networks to avoid conflicts with public IP addresses. These ranges include 10.x.x.x, 172.16.x.x - 172.31.x.x, and 192.168.x.x.
- Network blocks can be denoted using CIDR notation (e.g., /8, /24), where the number indicates the number of fixed bits in the network portion.
- Subnet masks are 32-bit numbers used to identify the network and host portions of an IP address. Bits set to '1' represent the network portion, and bits set to '0' represent the host portion.
- Subnetting involves dividing a larger network into smaller, more manageable subnets.
- Route summarization (or summary networks) helps to improve routing efficiency by advertising a single summary route for multiple subnets.
- Network Address Translation (NAT) is used to allow devices with private IP addresses to communicate with the internet using one or more public IP addresses. Common types include one-to-many NAT (used in home networks) and one-to-one NAT.































































![Nomad Goods Launches 15% Sitewide Sale for 48 Hours Only [Deal]](https://www.iclarified.com/images/news/96899/96899/96899-640.jpg)


![Apple Watch Series 10 Prototype with Mystery Sensor Surfaces [Images]](https://www.iclarified.com/images/news/96892/96892/96892-640.jpg)

















![watchOS 11.4 now available with three new features for Apple Watch [U: Back]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2025/01/watchOS-11.4-hero.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)






















































































_Andrew_Angelov_Alamy.jpg?#)







































































![[The AI Show Episode 142]: ChatGPT’s New Image Generator, Studio Ghibli Craze and Backlash, Gemini 2.5, OpenAI Academy, 4o Updates, Vibe Marketing & xAI Acquires X](https://www.marketingaiinstitute.com/hubfs/ep%20142%20cover.png)













































































































![Is this a suitable approach to architect a flutter app? [closed]](https://i.sstatic.net/4hMHGb1L.png)


















![From broke musician to working dev. How college drop-out Ryan Furrer taught himself to code [Podcast #166]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743189826063/2080cde4-6fc0-46fb-b98d-b3d59841e8c4.png?#)






























-1280x720.jpg?width=1920&height=1920&fit=bounds&quality=80&format=jpg&auto=webp#)



















![Baldur's Gate 3-Themed Stardew Valley Mod Hit With Takedown By D&D Owner [Update: It's Back]](https://i.kinja-img.com/image/upload/c_fill,h_675,pg_1,q_80,w_1200/72456bbdaa2125a0df912aa9d205bb26.webp)